The following bulletin from the Department of Homeland Security’s National Cybersecurity and Communications Integration Center was obtained from the website of California State University Long Beach.
National Cybersecurity and Communications Integration Center
- 3 pages
- TLP: GREEN
- October 17, 2014
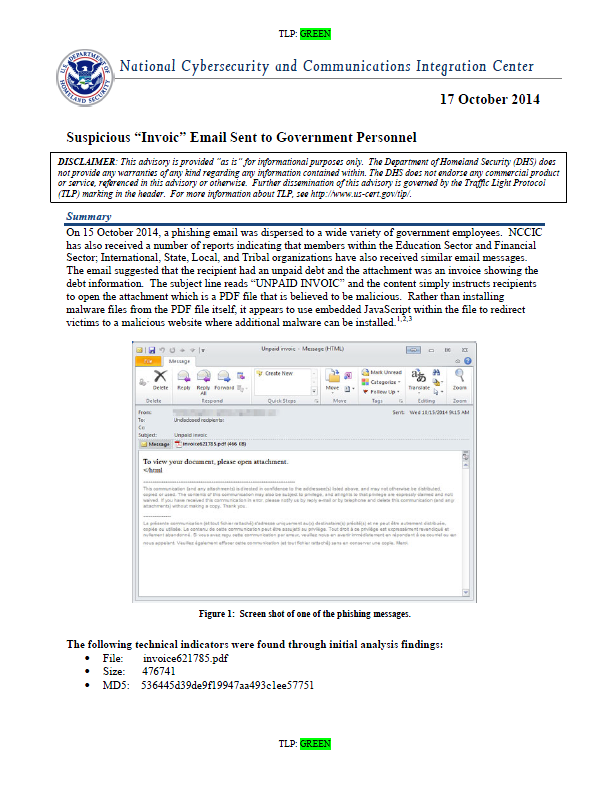
On 15 October 2014, a phishing email was dispersed to a wide variety of government employees. NCCIC has also received a number of reports indicating that members within the Education Sector and Financial Sector; International, State, Local, and Tribal organizations have also received similar email messages. The email suggested that the recipient had an unpaid debt and the attachment was an invoice showing the debt information. The subject line reads “UNPAID INVOIC” and the content simply instructs recipients to open the attachment which is a PDF file that is believed to be malicious. Rather than installing malware files from the PDF file itself, it appears to use embedded JavaScript within the file to redirect victims to a malicious website where additional malware can be installed.
The following technical indicators were found through initial analysis findings:
• File: invoice621785.pdf
• Size: 476741
• MD5: 536445d39de9f19947aa493c1ee57751It should be noted that the PDF file’s naming convention has been observed with different numerical values following the word “invoice” and invoice is spelled correctly in some of the email messages and incorrectly in others, but the campaign is likely the same.
Analysis conducted on the MD5 Hash in VirusTotal yields that only 29 of 54 possible security vendors are detecting it right now and there is a possibility that the campaign could eventually lead to machines becoming compromised with the Dyre/Dyreza banking malware. Dyreza is similar to many other types of banking malware in that it exploits vulnerability within the infected machine’s system, gives malicious actors remote access onto the infected machine, and intercepts sensitive login information (e.g. usernames and passwords). Most of the major security vendors (F-Secure, AVG, BitDefender, McAfee, Kaspersky, Symantec, and so on) are detecting the malware; however, there is a possibility that this campaign could be using a newer variant of the Dyre/Dyreza banking malware.
Vendor Naming Convention of Detected Malware:
• AVG – Exploit_c.ABHT
• F-Secure – Exploit.PDF.CVE-2013-2729.A
• Kaspersky – Exploit.PDF.Agent.c
• McAfee – Exploit-CVE2013-2729
• Microsoft – Exploit:JS/Pdfjsc.BC
• Symantec – Trojan.Pidief
• TrendMicro – TROJ_PIDIEF.YYJUPossible Malicious IP addresses:
• 63.167.150.122
• 64.50.186.140
• 65.55.169.133
• 65.55.169.124
• 74.114.188.69
• 159.220.28.56
• 157.56.110.117
• 157.56.110.130
• 157.56.110.148
• 216.22.15.81The following email addresses were observed sending similar phishing messages:
• Tharvey[@]vista-dental.com
• Jerry.Beets[@]pilottravelcenters.com
• Alena.Karatkevich[@]ppnc.org
• Jed[@]countertrade.com
• Charlieg[@]glendinningprods.com
• aris.tzounakos[@]aon.ca
• Pthorpe[@]samuel.com
• jacky.williams[@]thomsonreuters.comInitial findings suggest that the campaign aims to exploit vulnerabilities CVE-2013-2729 and CVE-2010-0188; both of which exploit vulnerability within Adobe Reader and Acrobat. Each of these vulnerabilities are old and Adobe has issued patches and software updates that do address these vulnerabilities. A good suggestion for those who received this message would be to verify the version of Adobe and Acrobat they are using and if outdated, implementing the updates is recommended.
This is a good example of how malicious cyber actors often reuse old tactics and techniques. This is also a good example of how important it is to follow best practices and install updates and patches for software applications as they become available. Users that have the most updated versions of both Adobe and Acrobat likely would not be vulnerable to this attack as it does not seem to function with updated versions, but those who received the message should still be cautious.