
A Department of Justice Inspector General report on the FBI’s surveillance activities conducted under section 702 of the Foreign Intelligence Surveillance Act.

A group of cyber actors utilizing infrastructure located in Iran have been conducting computer network exploitation activity against public and private U.S. organizations, including Cleared Defense Contractors (CDCs), academic institutions, and energy sector companies. The actors typically utilize common computer intrusion techniques such as the use of TOR, open source reconnaissance, exploitation via SQL injection and web shells, and open source tools for further network penetration and persistence. Internet-facing infrastructures, such as web servers, are typical targets for this group. Once the actors penetrate a victim network, the actors exfiltrate network design information and legitimate user credentials for the victim network. Often times, the actors are able to harvest administrative user credentials and use the credentials to move laterally through a network.

This Private Industry Notification (PIN) highlights the use of Global Positioning Systems (GPS) jammers by criminals to thwart law enforcement response and investigation into cargo thefts in the United States. Since at least February 2012, various law enforcement and private sector partners have reported that GPS tracking devices have been jammed by criminals engaged in nefarious activity including cargo theft and illicit shipping of goods. Although banned by federal law, the jammers are readily available over the Internet and easy to employ.

Destructive malware used by unknown computer network exploitation (CNE) operators has been identified. This malware has the capability to overwrite a victim host’s master boot record (MBR) and all data files. The overwriting of the data files will make it extremely difficult and costly, if not impossible, to recover the data using standard forensic methods. Analysis of this malware is presented to provide the computer network defense (CND) community with indicators of this malware.
The FBI Cyber Division has issued a notification to private industry and law enforcement to be aware of the potential for retaliatory cyber attacks following recent U.S. military actions in the Middle East. While the FBI has “no information at this time to indicate specific cyber threats to US networks or infrastructure in response to ongoing US military air strikes against the terrorist group known as the Islamic State of Iraq and the Levant (ISIL)” the bulletin states that the FBI believes that “extremist hackers and hacktivist groups, including but not limited to those aligned with the ISIL ideology, will continue to threaten and may attempt offensive cyber actions against the United States in response to perceived or actual US military operations in Iraq or Syria.”

The FBI has no information at this time to indicate specific cyber threats to US networks or infrastructure in response to ongoing US military air strikes against the terrorist group known as the Islamic State of Iraq and the Levant (ISIL), also known as the Islamic State of Iraq and al-Shams (ISIS) or the Islamic State (IS). However, the FBI assesses extremist hackers and hacktivist groups, including but not limited to those aligned with the ISIL ideology, will continue to threaten and may attempt offensive cyber actions against the United States in response to perceived or actual US military operations in Iraq or Syria. The FBI bases this assessment on recent, nonspecific, and probably aspirational threats made on social media platforms to carry out cyber as well as physical attacks in response to the US military presence in the Middle East.

The FBI is providing the following information with HIGH confidence. The FBI has observed malicious actors targeting healthcare related systems, perhaps for the purpose of obtaining Protected Healthcare Information (PHI) and/or Personally Identifiable Information (PII). These actors have also been seen targeting multiple companies in the healthcare and medical device industry typically targeting valuable intellectual property, such as medical device and equipment development data.

This review is a follow-up to three previous OIG reports concerning the FBI’s use of national security letter authorities. In our first and second NSL reports, issued in March 2007 and March 2008, the OIG found repeated instances of the FBI’s misuse of NSL authorities during 2003 through 2006. During our first NSL review we also discovered the FBI’s practice of issuing exigent letters and using other informal methods to obtain telephone records, instead of using NSLs or other legal process. We addressed these practices in a separate report issued in January 2010.
A bulletin issued by the Department of Homeland Security, the FBI and the National Counterterrorism Center earlier this month warns law enforcement and private security personnel that malicious cyber actors can use “advanced search techniques” to discover sensitive information and other vulnerabilities in websites. The bulletin, titled “Malicious Cyber Actors Use Advanced Search Techniques,” describes a set of techniques collectively referred to as “Google dorking” or “Google hacking” that are used to refine search queries to provide more specific results.

Malicious cyber actors are using advanced search techniques, referred to as “Google dorking,” to locate information that organizations may not have intended to be discoverable by the public or to find website vulnerabilities for use in subsequent cyber attacks. “Google dorking” has become the acknowledged term for this malicious activity, but it applies to any search engine with advanced search capabilities. By searching for specific file types and keywords, malicious cyber actors can locate information such as usernames and passwords, e-mail lists, sensitive documents, bank account details, and website vulnerabilities. For example, a simple “operator:keyword” syntax, such as “filetype:xls intext:username,” in the standard search box would retrieve Excel spreadsheets containing usernames. Additionally, freely available online tools can run automated scans using multiple dork queries.

The FBI assesses that if autonomous cars are approved by Congress for use by the public nationwide in the next five to seven years, these vehicles will have a high impact on transforming what both law enforcement and its adversaries can operationally do with a car. State regulators in California, Florida, and Nevada already legalized the use of these vehicles within their states.

Efforts to gain expertise with explosive, incendiary, and chemical/biological devices may lead to injuries and emergency treatment, which may provide potential indicators of violent extremist activities to responding emergency medical service (EMS) personnel. Scene size-up and patient assessment provide first responders the opportunity to view both the scene and any patient injuries. EMS personnel and other first responders should consider the totality of information gleaned through direct observation and the statements of patients, witnesses, and bystanders to evaluate whether an injury is a genuine accident or related to violent extremist activity.

The FBI and NCIS believe a group of cyber actors have been using various social networking sites to conduct spear phishing activities since at least 2011. FBI and NCIS investigation to date has uncovered 56 unique Facebook personas, 16 domains, and a group of IP addresses associated with these actors. These personas typically would attempt to befriend specific types of individuals such as government, military, or cleared defense contractor personnel. After establishing an online friendship the actor would send a malicious link (usually through one of the associated domains) to the victim, either through e-mail or in a chat on the social networking site eventually compromising the target’s computer.

Terrorists in late December 2013 conducted three attacks targeting people using public transportation systems in Russia, emphasizing terrorists’ persistent interest in attacking locations where large congregations of people are confined to small, often enclosed spaces. Russian officials claim North Caucasus-based violent extremists associated with the Imirat Kavkaz (IK) probably conducted these attacks to embarrass the Russian government in the build-up to the 2014 Olympic Games in Sochi. The IK, a violent extremist group based in Russia, has no known capability in the Homeland and is unlikely to directly target Western interests overseas.

Today the Western District of Pennsylvania unsealed an indictment naming five members of the People’s Liberation Army of the People’s Republic of China on 31 counts, including conspiring to commit computer fraud (18 U.S.C. §§ 371, 1030), accessing a computer without authorization for the purpose of commercial advantage and private financial gain (18 U.S.C. § 1030(a)(2)(C), (c)(2)(B)), damaging computers through the transmission of code and commands (18 U.S.C. § 1030(a)(5)), aggravated identity theft (18 U.S.C. § 1028A), economic espionage (18 U.S.C. § 1831(a)(1)), and theft of trade secrets (18 U.S.C. § 1832(a)(1)). Each of the defendants provided his individual expertise to a conspiracy to penetrate the computer networks of six US companies while those companies were engaged in negotiations or joint ventures with or were pursuing legal action against state-owned enterprises in China. The following technical details are indicators released in the indictment related to these actors’ activity.

On 13 May 2014, FBI NY initiated a coordinated takedown focusing on individuals who purchased the Blackshades malware. Field offices across the United States, as well as foreign partners, engaged in subject interviews, searches, hardware seizures, and arrests. The FBI seized the primary domain utilized to purchase Blackshades products.

On April 15, 2013, two pressure cooker bombs placed near the finish line of the Boston Marathon detonated within seconds of each other, killing three and injuring more than two hundred people. Law enforcement officials identified brothers Tamerlan and Dzhokhar Tsarnaev as primary suspects in the bombings. After an extensive search for the then-unidentified suspects, law enforcement officials encountered Tamerlan and Dzhokhar Tsarnaev in Watertown, Massachusetts. Tamerlan Tsarnaev was shot during the encounter and was pronounced dead shortly thereafter. Dzhokhar Tsarnaev, who fled the scene, was apprehended the following day and remains in federal custody.

Law enforcement continues to see reporting of malicious cyber actors using fake help desk scams, also known as technical support scams. These scams, if successful, seek to compromise and take control of computer systems. Malicious cyber actors send users an e-mail or they make cold calls, purportedly representing a help desk from a legitimate software or hardware vendor. The malicious cyber actors try to trick users into believing that their computer is malfunctioning—often by having them look at a system log that typically shows scores of harmless or low-level errors—then convincing them to download software or let the “technician” remotely access the personal computer to “repair” it.
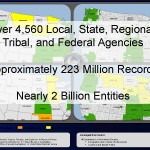
The Law Enforcement National Data Exchange (N-DEx) run by the FBI Criminal Justice Information Services (CJIS) Division now contains approximately 223 million records on nearly two billion entities. A FBI CJIS presentation from February 2014 posted on the website of the Integrated Justice Information Systems Institute includes detailed information on state and local data contributors including a tally of the total number of records contributed by state.