Office of the Army Chief Information Officer/G-6
- Version 1.2
- 21 pages
- February 2015
The network is one of the key technological focus areas described in the Army Operating Concept (October 2014). As an enabler of situational understanding across the joint force, the network must “empower leaders at the lowest levels with relevant combat information, situational understanding, and access to joint and Army capabilities.” The Army Operating Concept calls for developing and modernizing “capabilities, such as cloud-enabled networks for mobile operations in austere environments and across wide areas,” that are “simple and resilient, anticipating enemy efforts to disrupt communications.”
The world is evolving into an increasingly interconnected environment. The Army of 2020 will operate in a complex world where cloud-based computers receive data from tens of billions of devices. These computers will have the capacity to digest, correlate, contextualize, process and then present data back to humans in a way that assists our decision-making process. The Army is modernizing its network to prepare for the impending data-driven, cloud-based world, as depicted in Figure 1. While legacy networking architectures stored and protected data locally, cloud-based architectures will store and protect data in a centralized yet distributed repository that enables global access. The Army Network Campaign Plan outlines current efforts that posture the Army for success in a cloud-based world.
The Army is following Industry best practices to transition to the cloud. Cloud-based networking requires assured and sufficient bandwidth. The Army is employing Multi-Protocol Label Switching (MPLS) and other transport upgrades designed and to increase exponentially increase the throughput of our global ‘backbone’ and the connectivity to posts, camps and stations. With Joint Regional Security Stacks (JRSS), the Army is transitioning from legacy security that protected data locally and required hundreds of security stacks to regionalized security that protects data in the cloud. The Army’s application rationalization project will help reduce the number of applications the Army maintains (currently more than 25,000), and it will modernize and move the remaining applications to the cloud. Once bandwidth is sufficient, security is applied and data/applications reside in the cloud, the Army will then provide secure access to data from mobile devices. The end state is a global cloud-based network designed to provide Soldiers access to tailored and timely information at the point of need. As the network aggregates, processes, secures and presents data in a way that is easily understood, Soldiers will be able to make informed, more effective decisions as they perform the missions of the future.
…
The technological environment is characterized by rapid innovation, widespread access to powerful computer processing capabilities that were once restricted to use by government and academia, and persistent and evolving cybersecurity threats.
Rapid changes in technology shorten the useful life of many of the physical components that make up the network. To compensate, a faster, more flexible approach to both acquisition and training is required in order to maintain capability while mitigating vulnerabilities. Such an approach must include security features that are “baked into” systems from the outset and not “bolted on” as an afterthought.
Growing computer processing power presents multiple threats and opportunities. The ability to store tremendous amounts of data, combined with powerful analytical tools, makes it possible to query large distributed collections of loosely structured information to support faster, more intelligent decision making. So-called big data technology will enable the Army to detect or predict previously undetectable anomalies in the network but it may also arm adversaries with the ability to disrupt U.S. operations. Enemy actions may not be easily distinguishable from legitimate activity, and the lack of full visibility across the network creates vulnerabilities and delays detection and response.
Threats will continue to grow in scale and sophistication as access and computing power grow. They range from state-sponsored offensive military operations and espionage activities, to violent extremist organizations intent on disrupting the American way of life, to criminals and recreational hackers seeking financial gain and notoriety. Additionally, in cyberspace, traditional boundaries do not exist and anonymous attacks can occur at near light speed. Given the progression of these advanced persistent threats, we must continuously develop new approaches to managing and securing information, and ensuring our ability to operate and provide our workforce the right capabilities to defend, monitor, detect, isolate and respond to threats in real time.
Network architecture also presents significant challenges. The Army’s current network is comprised of top secret, secret and unclassified enclaves, with more than 1,000 external access points. This makes the network as a whole difficult to secure and to manage. The always present pressure to deploy new technology must be balanced against approved requirements, risks and compatibility with the DoD global architecture. The more complex and opaque the network, the greater are the chances of critical, high-impact vulnerabilities, including insider threats.
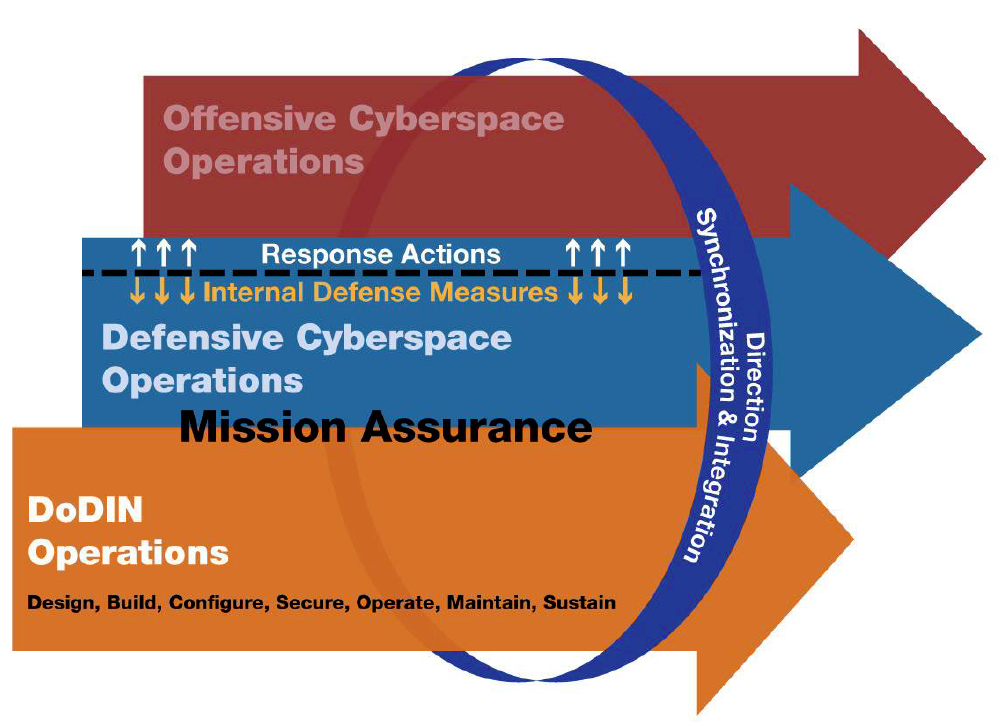
The technological environment will shape how the Army fights in the cyberspace domain. The Army retains overmatch through combining technologies and integrating them with organizational, doctrinal, leader development, training and personnel policies. To maintain our advantage in the technological environment, we must develop a right-sized, well trained cadre of Signal, Cyber and Intelligence professionals to conduct, support and enable all three lines of cyberspace operations (CO) depicted in Figure 2: Department of Defense Information Network (DoDIN) Operations, Defensive Cyberspace Operations (DCO) and Offensive Cyberspace Operations (OCO). With the establishment of Army Cyber Command, Second Army, the Cyber Center of Excellence (CCoE) and the new Career Field 17 cyber branch, the Army will be able to address the significant challenges of recruiting, training and retaining the people necessary to generate the human capital required for successful cyberspace operations.
The successful execution of cyberspace operations requires the integrated and synchronized employment of offensive, defensive and DoDIN operations, underpinned by effective and timely operational preparation of the environment. Offensive Cyberspace Operations are cyberspace operations intended to project power through the application of force in and via cyberspace. Defensive Cyberspace Operations are cyberspace operations intended to defend DoD or other friendly cyberspace. DoDIN operations are actions taken to design, build, configure, secure, operate, maintain and sustain DoD communications systems and networks in a way that creates and preserves data availability, integrity, confidentiality, user/entity authentication and non-repudiation.