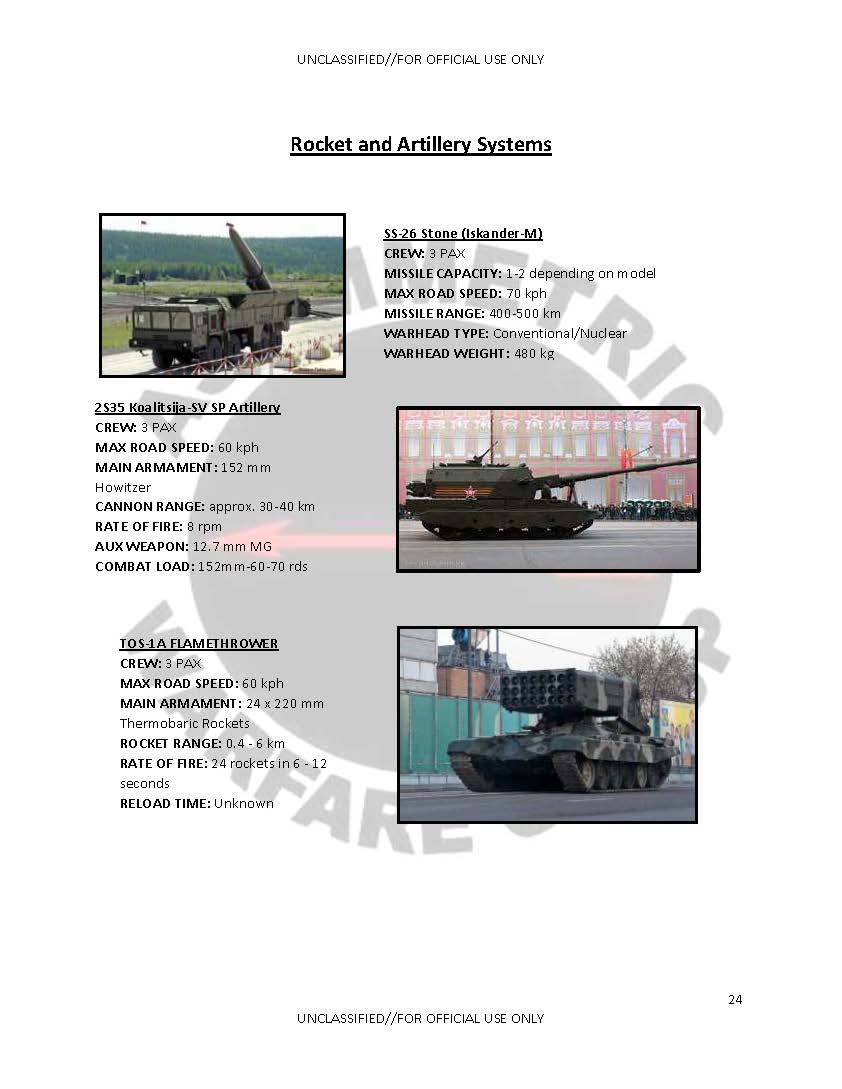
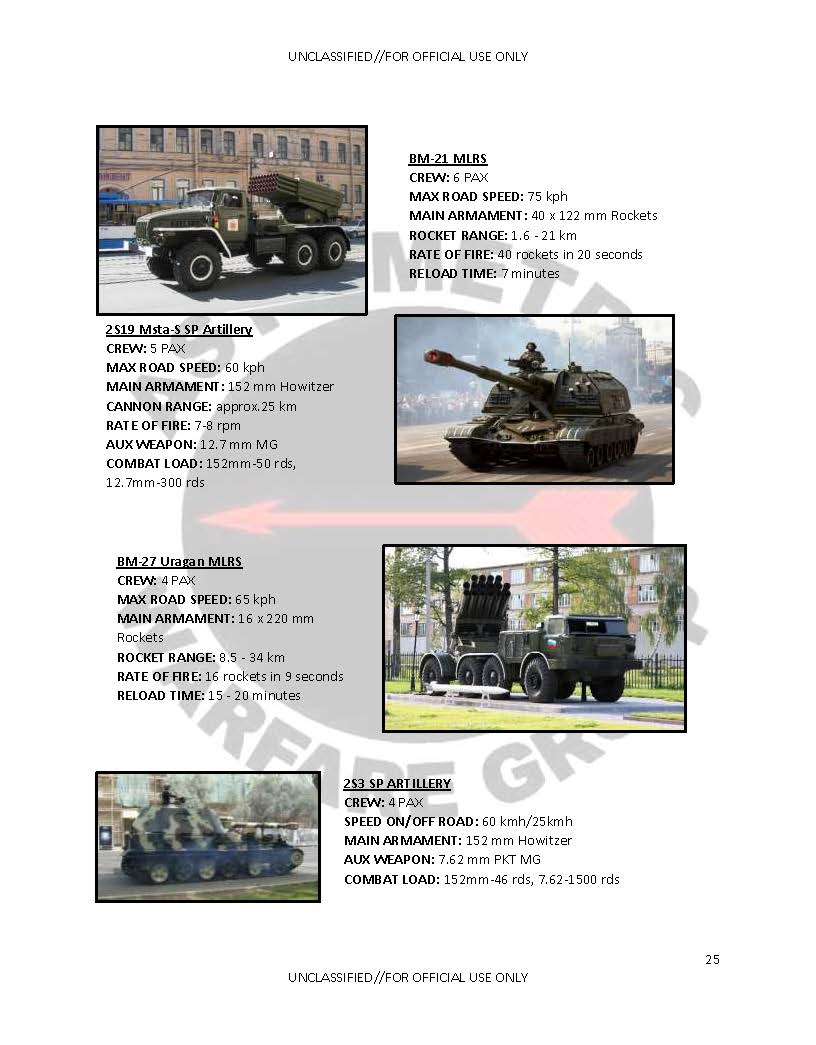
(U) As the American Army fought in Iraq and Afghanistan, it became the best tactical level counter insurgency force of the modern era. America’s enemies, however, did not rest. Russia observed the transformation of the American Army and began a transformation of their own. This new military barely resembles its former Soviet self. Wielding a sophisticated blend of Unmanned Aircraft Systems (UAS), electronic warfare (EW) jamming equipment, and long range rocket artillery, it took the Soviet model out of the 1980s and into the 21st Century.
(U) Ukraine’s 2014 Euromaidan Revolution overthrew a corrupt Russian supported president and threatened to place a pro-European government in power on the very outskirts of the Russian Federation. In March 2014, Russia occupied Ukraine’s Crimea with SPETsNAZ units in a virtually bloodless operation. SPETsNAZ then infiltrated into the Donbas region, fomenting unrest and sparking a pro-Russian insurgency.
(U) Over the next few months, the Ukrainian military and volunteer militia fought back rather successfully. They pushed the separatists back to the very border with Russia. Then everything changed. Russian regular troops with heavy equipment attacked across their border and fought a series of encirclement battles resulting in hundreds of Ukrainian troops killed and the Ukrainian Anti-Terror Operation teetering on the brink of defeat.
(U) How do we combat this enemy? America has not encountered this type of conflict for nearly a generation and needs to transform to fight and win in complex maneuver warfare. Several factors contribute to potential challenges U.S. formations may face in such a conflict: It has been several years since we deployed large numbers of troops in combat in Iraq or Afghanistan. Our junior leaders, both officers and enlisted, have less and less combat experience. Our equipment has been designed to combat an insurgency, not an enemy with potential overmatch. How do we protect our troops from unmanned aerial vehicles (UAVs), communications and GPS jamming, and layered air defense networks?
(U) This handbook attempts to examine the tactics used by Russia in Ukraine as the military component of their New Generation Warfare doctrine. We will attempt to describe their capabilities and applications of combat power. Finally, this handbook will present recommendations for U.S. Battalions and Brigade Combat Teams to counter these Russian methods of war. The war in Ukraine is still ongoing. The Russian Forces are still involved in Syria and continue to improve from their successes and shortfalls. We, as American Soldiers, must do the same. As the saying goes, “Only fools learn from their mistakes. The wise man learns from the mistakes of others.”
…
(U) CYBER
(U) Russia’s developing capabilities have also incorporated the cyber realm. The U.S. dependence on computer networks and the amount of technology present even at the company level, create vulnerabilities to Russia’s new found capabilities. Contributing factors for increased cyber-attacks are their low risk to high pay off ratio and increasingly interconnected U.S. military networks. Everyday U.S. military functions, such as Web-based or computer generated administrative and logistical operations or activities. This creates a significant vulnerability to cyber intrusion and network degradation.
(U) Cyber-attacks can effectively shape the battlefield and require very little risk on the part of the perpetrator. Since U.S. formations operate under selfimposed restrictions, like ethical hacking and prioritizing protective measures over offensives in the cyber realm, they are limited in their capabilities compared to Russian counterparts.
(U//FOUO) Russia is also able to reach into its nonmilitary cyber expertise to complement their military capabilities. The Kremlin cooperates with criminal hacker groups and the Russian government employs thousands of professional hackers as part of their whole of government Information Operations strategy. This severely outnumbers U.S. military cyber capabilities and means that U.S. brigades could be subjected to cyber-attacks from pro-Russian sympathizers in countries not even involved in a conflict.
(U) As with the degraded communication environment, Cyber Meaconing Intrusion, Jamming and Intercept (MIJI) is a very real threat to U.S. formations.
…