Executive Order 13636: Improving Critical Infrastructure Cybersecurity Cyber-Dependent Infrastructure Identification Working Group (CDIIWG)
- 20 pages
- For Official Use Only
- March 11, 2013
Overview of Executive Order 13636
– Executive Order (EO) 13636, Improving Critical Infrastructure Cybersecurity was released on February 12, 2013
– Relies on public-private collaboration to improve critical infrastructure cyber posture
– Includes elements to enhance information sharing, develop a cybersecurity framework, and create a voluntary cybersecurity program
– Requires the Department of Homeland Security (DHS) to identify the “critical infrastructure where a cybersecurity incident could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security”DHS will work with CIPAC to execute Section 9 of the EO
“Within 150 days of the date of this order, the Secretary shall use a risk-based approach to identify critical infrastructure where a cybersecurity incident could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security.” (EO 13636, Section 9)
Apply consistent, objective criteria
Stakeholders include:
– Critical Infrastructure Partnership Advisory Council (CIPAC)
– Sector Specific Agencies (SSA)
– Sector Coordinating Councils (SCC)
– Government Coordinating Councils (GCC)
– Critical infrastructure owners and operatorsThe list of identified critical infrastructure will be reviewed and updated on an annual basis
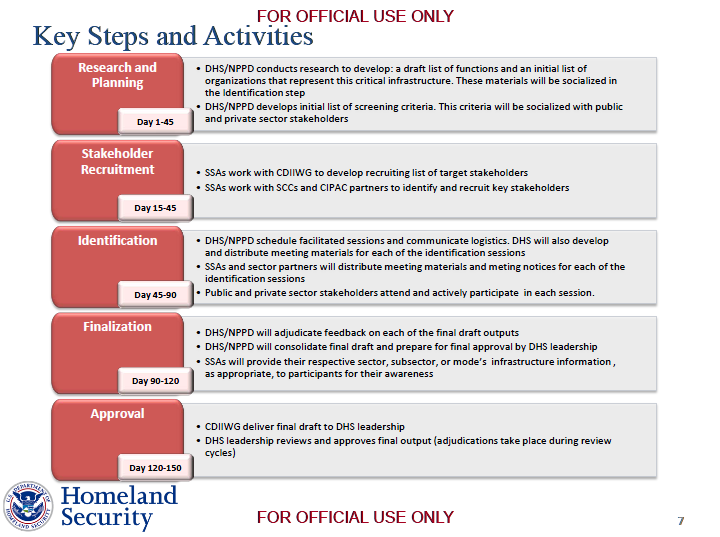
Execution of Section 9 will be led by the Cyber-Dependent Infrastructure Identification Working Group (CDIIWG)
Overview of CDII Approach (1 of 2)
Only a small subset of U.S. infrastructure will fall under the focus of the EO activity
– Owners and operators will have the opportunity to provide relevant information
– A review process will be established for the identification as critical infrastructureFocus is on critical infrastructure that could be compromised through cyber exploitation and which, if incapacitated, could result in catastrophic national, public health, or economic consequences
– Higher standard than debilitating, which is what is used in the base definition to define critical infrastructure
– The Secretary of DHS will provide a list of critical infrastructure most at risk in the context of a cyber incident within 150 days of EO release
– Commercial IT products and consumer information technology services will not be directly designated under the EO as infrastructure most at riskAll sectors will be engaged –through engagement and initial analysis it may be determined that a sector does not have any infrastructure that meets the threshold, the focus of the initial list will not be on that sector(s)
Sectors with existing CI identification processes and lists should be leveraged where appropriate
Functions-based approach to identify critical infrastructure
– Accounts for the virtual and distributed nature of cyber infrastructure
– Focuses on the critical activities, services, or products being produced or provided by a sector, subsector, or mode
– Functions are identified based on the national or regional level consequences that can result from a disruption or exploitation of the infrastructure
– Does not identify a specific organization’s assets, networks, or systems; focus is on sector functions and the types of systems that support themRequires the application of criteria that will be used to screen the infrastructure that aligns to the critical functions
– Consistently applied within sectors and, where possible, across sectors as wellStakeholder engagement will be conducted throughout this effort
– CDIIWG will work with sectors (SSAs, SCCs, GCCs) via the CIPAC partnership framework…