Homeland Infrastructure Threat and Risk Analysis Center (HITRAC)
- Domestic Threat Analysis Division (DTA)
- 17 pages
- For Official Use Only
- November 10, 2009
• DHS organization: Cyber Threat Branch
– Mission
– Role
– Responsibilities
– Requirements
– Focus areas
• The cyber threat environment
• Cyber threats to control systems…
Cyber Threat Branch Responsibilities
• Execute the responsibilities created by the Homeland Security Act of 2002:
– Access, receive, and analyze law enforcement, intelligence, and other information from federal, state, and local agencies and private sector entities to:
• Identify and assess the nature and scope of terrorist threats
• Detect and identify threats to the United States
• Understand threats in light of actual and potential vulnerabilities
– Carry out comprehensive assessments to determine the risk posed by terrorist attacks
• Outreach plays a critical role in the mission
– The CTB provides threat briefings and teleconferences to:
• Sector Coordinating Councils
• Government Coordinating Councils
• Key industry associations
• State and local officials, including fusion centersThree primary mission requirements as outlined by HSPD-7, the Homeland Security Act of 2002, the Comprehensive National Cybersecurity Initiative, the National Infrastructure Protection Plan, and the I&A Strategic Plan:
– Provide intelligence support for the DHS National Protection and Programs Directorate and the federal civilian domain.
– Provide intelligence analysis regarding cyber threats and threats to information technology and communication assets to homeland critical infrastructure/key resources owners and operators and
federal, state, local, tribal, law enforcement, and private sector partners
– Serve as the DHS enterprise designee to Intelligence Community efforts related to the cyber domain:
• National Cyber Study Group
• National Intelligence Estimates
• Intelligence Community Assessments
• National Intelligence Priorities Framework…
…
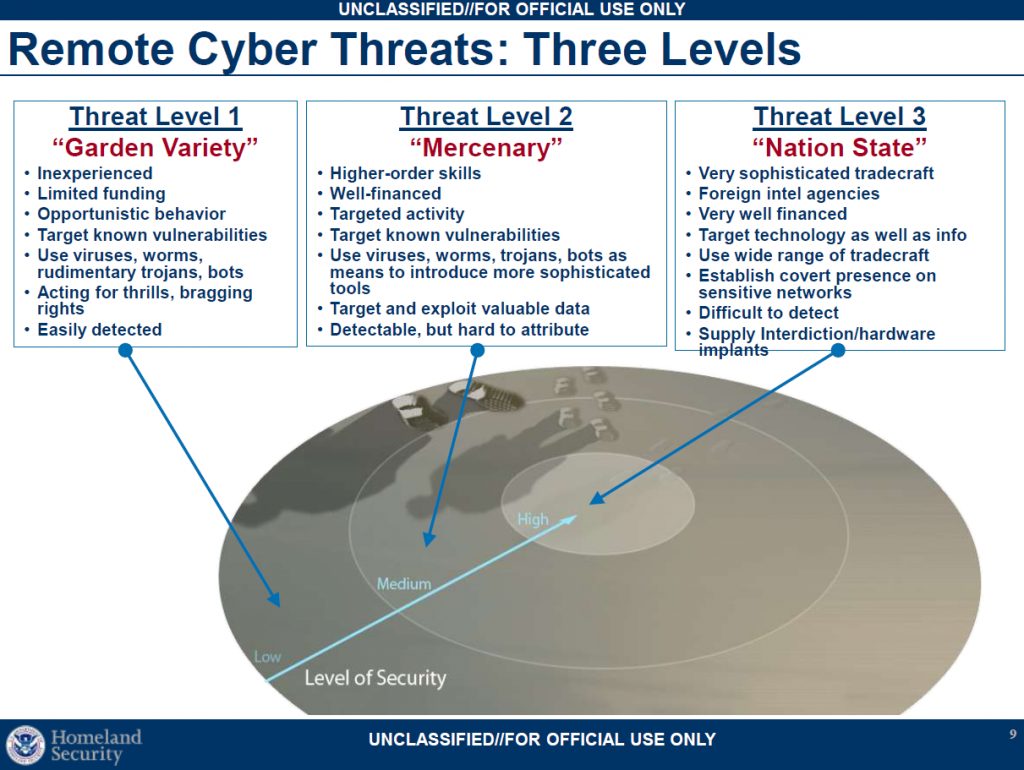
The Cyber Threat Environment
• Malicious cyber activity routinely is directed at the U.S. Government, private sector, and academia
– Growing more sophisticated, targeted, and prevalent
– Nature and source of the threat is diverse
– Designed to
• Exploit data gathered from information systems or networks (computer network exploitation)
• Disrupt, deny, degrade, or destroy information resident in computers and computer networks or the computers and networks themselves (computer network attack)
• We have limited insight on intrusions into private sector networks, but are becoming more aware of U.S. information infrastructure vulnerabilities to cyber attacks
– Key factors: dynamic business environment, reliance on open systems and COTS, management/enterprise networks‟ Internet connections
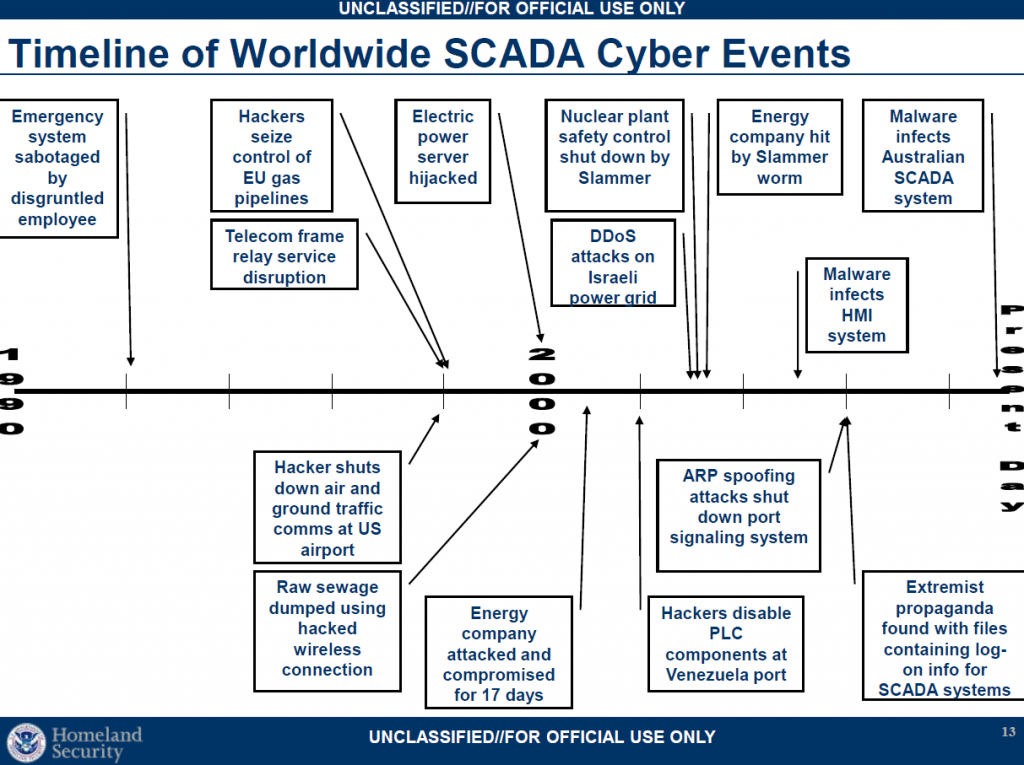
• Worldwide, power, chemical, water systems, and manufacturing companies have similar control systems
• Six vendors of process management systems are used in over 75 percent of U.S. domestic systems*
– This commonality in systems suggests that an adversary would not require a great deal of time to develop tools for new attacks or possibly could move rapidly from target to target…