| Team Themis Corporate Information Reconnaissance Cell (CIRC) Proposal | 12 pages | UNCLASSIFIED//FOUO//PROPIN | Download |
| Team Themis Corporate Information Reconnaissance Cell (CIRC) Presentation | 9 pages | Download | |
| HBGary – Berico Teaming Agreement | 7 pages | Download |
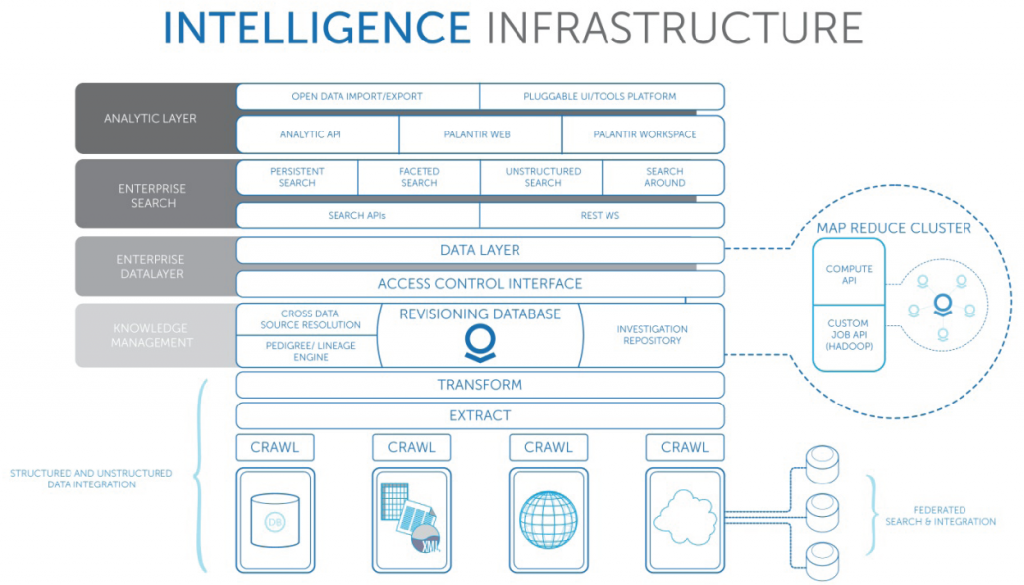
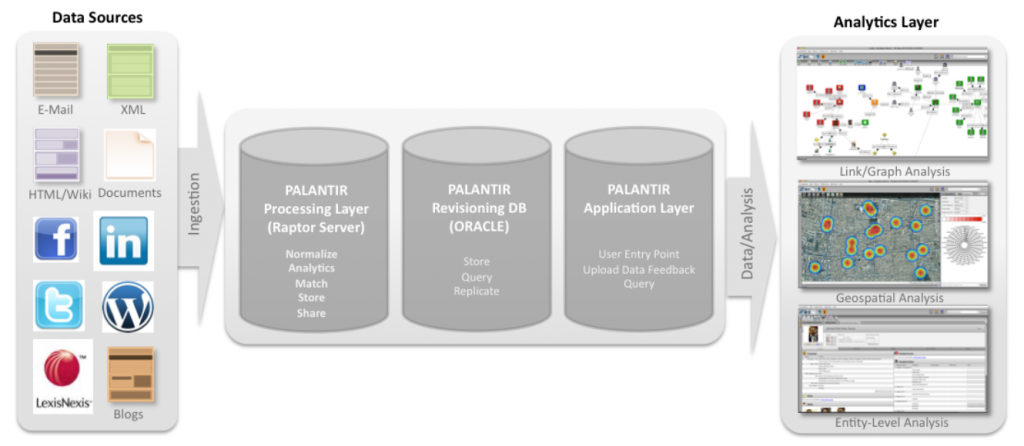
Internet based communications, most predominately the growing spectrum of social media platforms, allow people to coordinate and communicate in a highly efficient and collaborative manner, even when vastly geographically distributed. These same services and technologies can also make it difficult to attribute information to specific entities. Anonymizing and misattribution technologies used to mask location and identity have become commonplace. In many cases, people and/or organizations use the inherent insecurity in Internet communications to conduct criminal or unethical activities. This represents a paradigm shift in the capability of individuals and small groups to conduct effective planning and execution of asymmetric operations and campaigns that can have major impacts on large organizations or corporations.
Despite the increased capability and anonymity that these new communications technologies provide, it is still possible to counter individuals and groups who are leveraging networks, platforms, and/or applications to conduct criminal and/or unethical activities. In such cases, it is necessary to develop a more forward leaning investigative capability to collect, analyze, and identify people or organizations conducting such activities. In order to effectively track and understand the complex, interconnected networks involved in these actions, it becomes critical to utilize proven, cutting-edge tools and analytical processes; applying them in a deliberate, iterative manner against those involved in illicit activities. The most effective way to limit the capability of individuals and/or groups is to develop a comprehensive picture of the entities involved through focused collection, conduct rapid analysis to identify key nodes within the network, and determine the most effective method for influencing/limiting these entities.
…