NIST Key Management Workshop
- Jonathan Booth, Chief KMI Systems Engineering, National Security Agency
- Petrina Gillman, IA Infrastructure Development Technical Director, National Security Agency
- 5 pages
- For Official Use Only
- June 8, 2009
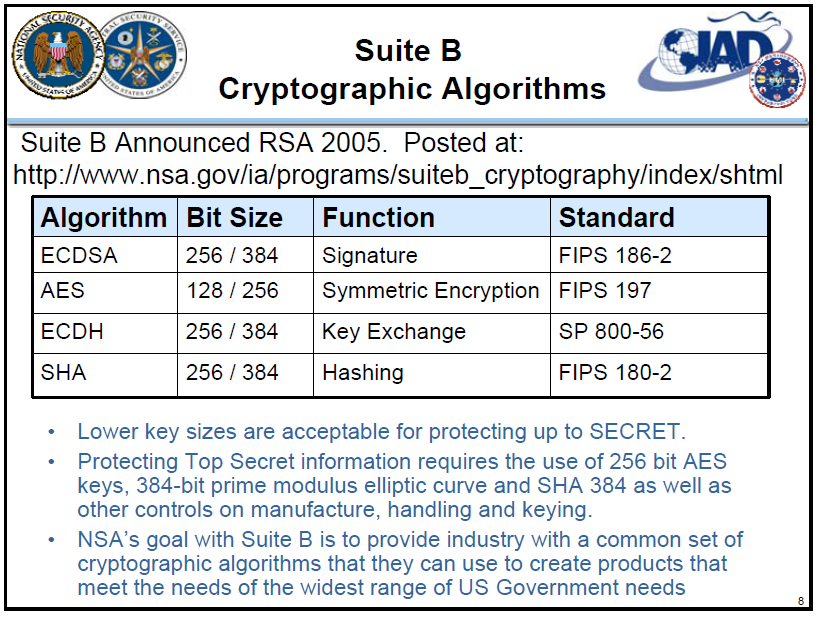
Key Management Lifecycle
• Key Management Lifecycle Model arising from our 50+ Years of Experience
– Identification of crypto key needs and recipients
– Generation
– Distribution & Accounting/Tracking
– Storage
– Usage
– Destruction
• Define in Key Management Planning document at initial product & system definition. Refine, during design, as more details defined.Key Management Design Challenges
• Key Management growing in complexity
• Cryptography providing more information assurance capabilities in highly networked systems
• Systems must support cyberspace requirements & legacy interoperability
• Algorithms well specified but few industry standard formats for keys
• X.509 is the exceptionVendor Specific Key Format Explosion
• Default has been for each vendor to define their own key format and packaging
– Large and expensive support tail
• Hundreds of key generation programs
• Not just generation also ordering, distribution, accounting and destruction differences
• NSA defining standard packaging and key formats
– Working in standards bodies to address gaps in industry standards for keys
– Defining profiles of industry standards for use in products used in national security systemsNSA Crypto Key Standardization Activities
• IETF
– Define Cryptographic Message Syntax (CMS), IETF RFC 3852, profiles for key and software packages
– Define a standard Trust Anchor Format and Trust Anchor Management Protocol
– Create standard asymmetric private key format
– Create standard symmetric key format
– Leveraging Certificate Management using CMS (CMC) for x.509 certificate management
• PKIX
– X.509 Suite B Certificate and CRL ProfileThe Need for Interoperability
• Many Interoperability Drivers (e.g. Katrina)
– Wide range of customers including
• DoD, FBI, DHS, State and Local Authorities, FEMA, Allies, Charities
– Drives dual use devices
• High assurance government devices that can interoperate with commercial devices
• Commercial assurance devices that can interoperate with High Assurance Government Devices
⇒Key formats as import as algorithm for interoperability
⇒Also need to address protocols, codecs etc…