ASYMMETRIC WARFARE GROUP TACTICAL INFORMATION SUPERIORITY
- 10 pages
- February 2011
- 3.35 MB
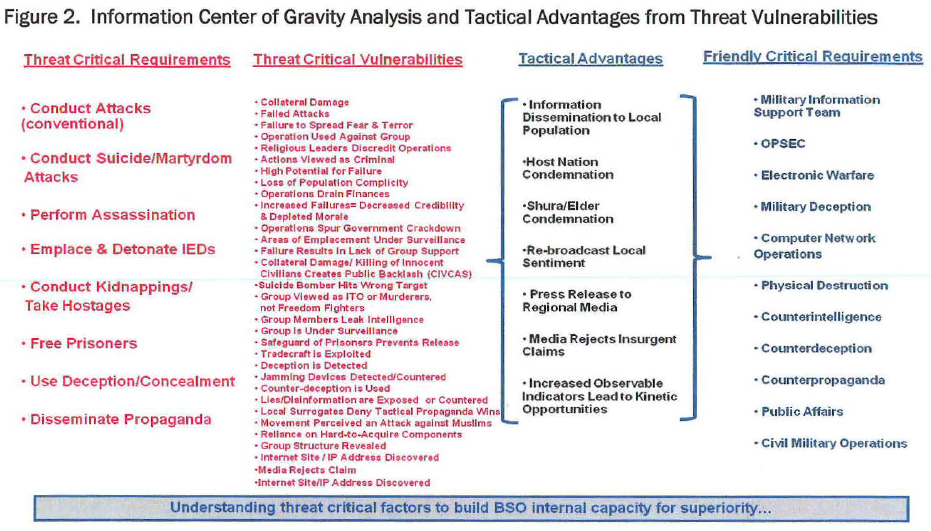
This document facilitates discussion, training, and implementation of effective information superiority methods at the Battalion and Brigade level. This paper discusses the Center of Gravity analysis model for identifying threat networks, Critical Capabilities, and Critical Vulnerabilities; use of the methodology to determine the threat vulnerabilities; and as a basis for understanding how to achieve Information Superiority.
The battalion commander instantly knew from looking at the map, with all of the red significant activities plotted on the overlay, that renewed operations in the valley would be rough. Almost every route into and out of the area had seen recent Improvised Explosive Device (IED) activity. Worse, it seemed that many of the villages in the valley were supportive of insurgent activity. The insurgents had recently stepped up their propaganda campaign in the area, as well, intimidating villagers, kidnapping elders, assassinating key figures, leaving behind strong warnings against cooperating with Coalition Forces, while also reinforcing their own message: the insurgents would prevail over the foreign forces because they were from the region, the insurgents would take care of the people that supported their activities, and they would continue to be in the area long after the Coalition Forces left.
The commander planned a deliberate clearing operation to regain control of the major routes in the area, deny insurgents traditional safe havens, and bolster Host Nation Security Forces and Government officials, but he also knew t hat if he entered the valley using too much force that he might further alienate the locals. The commander could not stay in the valley, holding the terrain against insurgent reinfiltration indefinitely-he would be forced to withdraw and plan for other operations, hoping the locals and Host Nation Security Forces would be willing and able to defend the area against the enemy.
How could the commander expect the villagers to aid his unit in denying the area as a support base for insurgents when there was no apparent common ground? How was he, as a Commander, supposed to communicate his intent to the local people, Host Nation officials, and to other key individuals? His battalion’s task organization included three Infantry Companies, an Anti-Tank Company, a Mortar Platoon, and a Scout Sniper Platoon. Additionally, the commander’s capabilities were augmented by a Tactical Military Information Support Team, a Military Source Operations (MSO) qualified Counterintelligence (CI) Team, and an Explosive Ordnance Detachment (EOD) Team. The commander also had new devices (including the Radio-In-The-Box or RIAB); some of these newly issued devices were pieces of equipment his leaders and Soldiers had never seen or used before deploying into theater.
The commander had enough combat forces to clear, and temporarily hold the valley, but what then? The commander knew he would achieve immediate but limited security in the area and also reach his higher headquarter’s directed end state. But how could he achieve longer term effects so that he would not have to repeat the mission again in just four months?
Lethal options in a Counter Insurgency (COIN) environment are only a portion of the necessary operations that must be successfully conducted at the tactical level. Non-Lethal options provide a balance to more kinetic operations, providing choices that can impact the threat and the population in longer term ways. Information Superiority, at the tactical level, is an essential requirement for successfully defeating insurgents in the COIN fight.
…