NATIONAL STRATEGY FOR TRUSTED IDENTITIES IN CYBERSPACE
- 52 pages
- April 2011
A secure cyberspace is critical to our prosperity. We use the Internet and other online environments to increase our productivity, as a platform for innovation, and as a venue in which to create new businesses. “Our digital infrastructure, therefore, is a strategic national asset, and protecting it—while safeguarding privacy and civil liberties—is a national security priority” and an economic necessity. By addressing threats in this environment, we will help individuals protect themselves in cyberspace and enable both the private sector and government to offer more services online.
As a Nation, we are addressing many of the technical and policy shortcomings that have led to insecurity in cyberspace Among these shortcomings is the online authentication of people and devices: the President’s Cyberspace Policy Review established trusted identities as a cornerstone of improved cybersecurity.
In the current online environment, individuals are asked to maintain dozens of different usernames and passwords, one for each website with which they interact. The complexity of this approach is a burden to individuals, and it encourages behavior—like the reuse of passwords—that makes online fraud and identity theft easier. At the same time, online businesses are faced with ever-increasing costs for managing customer accounts, the consequences of online fraud, and the loss of business that results from individuals’ unwillingness to create yet another account. Moreover, both businesses and governments are unable to offer many services online, because they cannot effectively identify the individuals with whom they interact Spoofed websites, stolen passwords, and compromised accounts are all symptoms of inadequate authentication mechanisms.
Just as there is a need for methods to reliably authenticate individuals, there are many Internet transactions for which identification and authentication is not needed, or the information needed is limited.
It is vital to maintain the capacity for anonymity and pseudonymity in Internet transactions in order to enhance individuals’ privacy and otherwise support civil liberties. Nonetheless, individuals and businesses need to be able to check each other’s identity for certain types of sensitive transactions, such as online banking or accessing electronic health records.
The National Strategy for Trusted Identities in Cyberspace (NSTIC or Strategy) charts a course for the public and private sectors to collaborate to raise the level of trust associated with the identities of individuals, organizations, networks, services, and devices involved in online transactions.
…
The realization of this vision is the user-centric “Identity Ecosystem” described in this Strategy. It is an online environment where individuals and organizations will be able to trust each other because they follow agreed upon standards to obtain and authenticate their digital identities—and the digital identities of devices. The Identity Ecosystem is designed to securely support transactions that range from anonymous to fully-authenticated and from low- to high-value.
…
Role of the Private Sector
Only the private sector has the ability to build and operate the complete Identity Ecosystem, and the final success of the Strategy depends upon private-sector leadership and innovation.
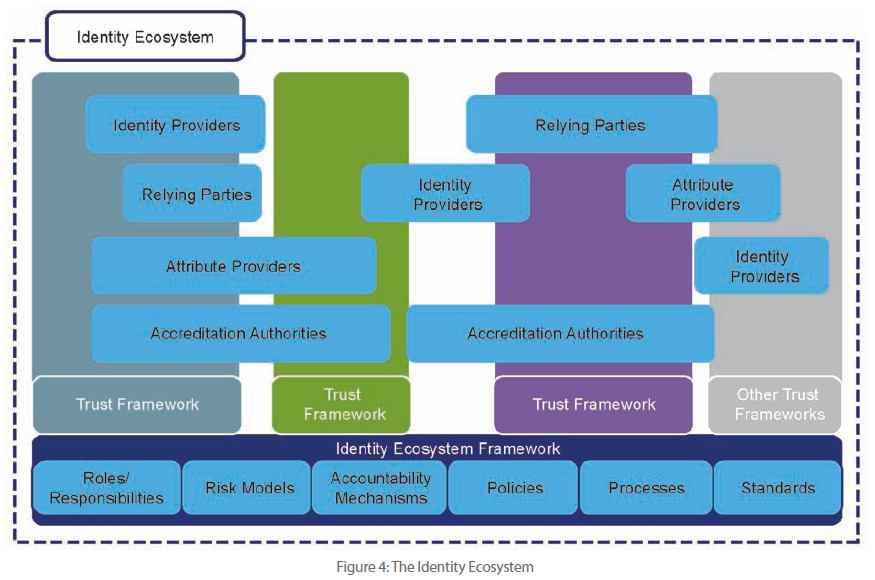
The key operational roles within the Identity Ecosystem include: subjects, relying parties, identity providers, attribute providers, and accreditation authorities For each of these ecosystem roles, the private sector will constitute the majority of the actors For example, most identity and attribute providers will be private-sector organizations.
The Strategy can only succeed if the Identity Ecosystem is self-sustaining, which will require the development of business models for each of the service provider roles in the ecosystem Many of these business models will be entirely new, and only the private sector can provide the innovation necessary to realize them.