Goals for a Common Approach to Threat Frameworks
Following a common approach helps to:
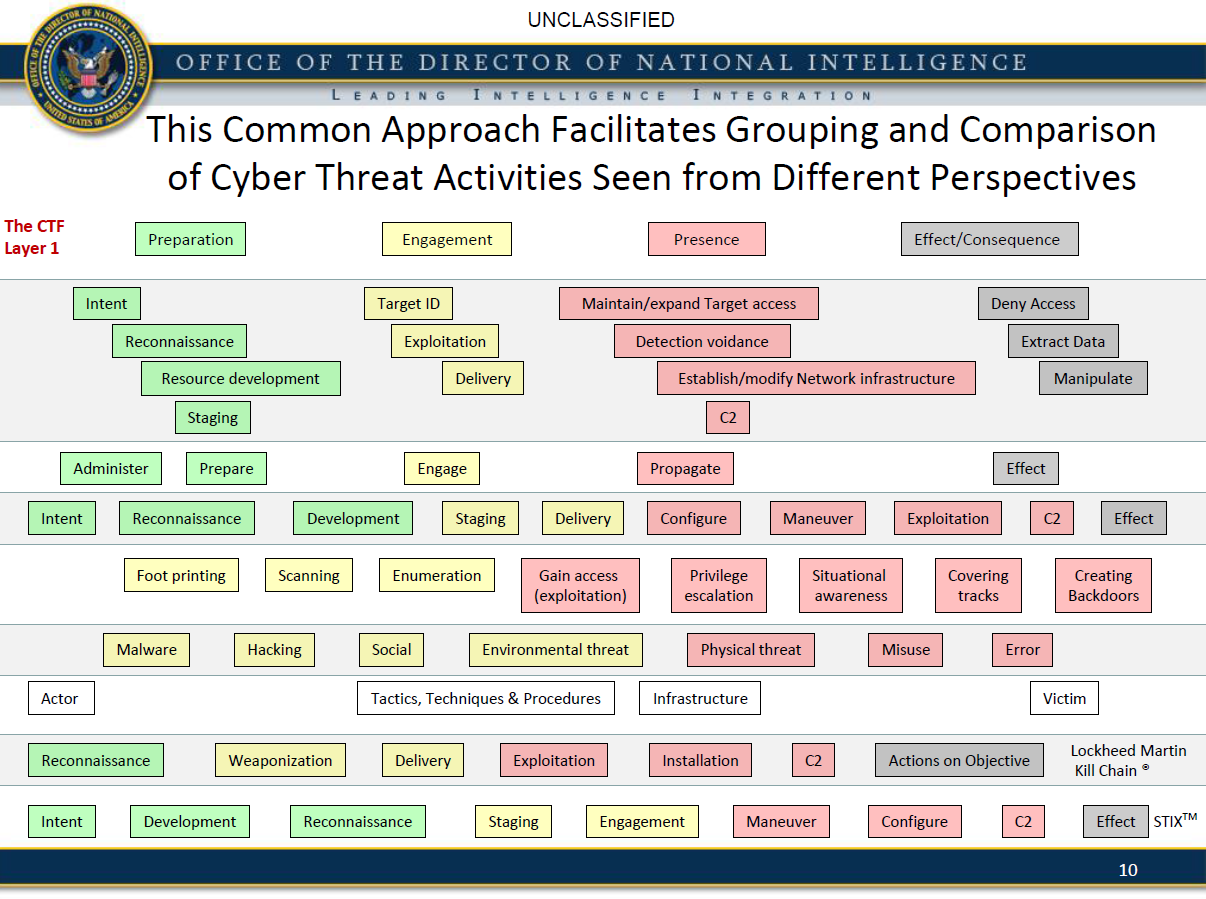
• Establish a shared ontology and enhance information-sharing since it is easier to maintain mapping of multiple models to a common reference than directly to each other
• Characterize and categorize threat activity in a straightforward way that can support missions ranging from strategic decision-making to analysis and cybersecurity measures and users from generalists to technical experts
• Support common situational awareness across organizations
Key Attributes and Goals in Building a Cyber Threat Framework
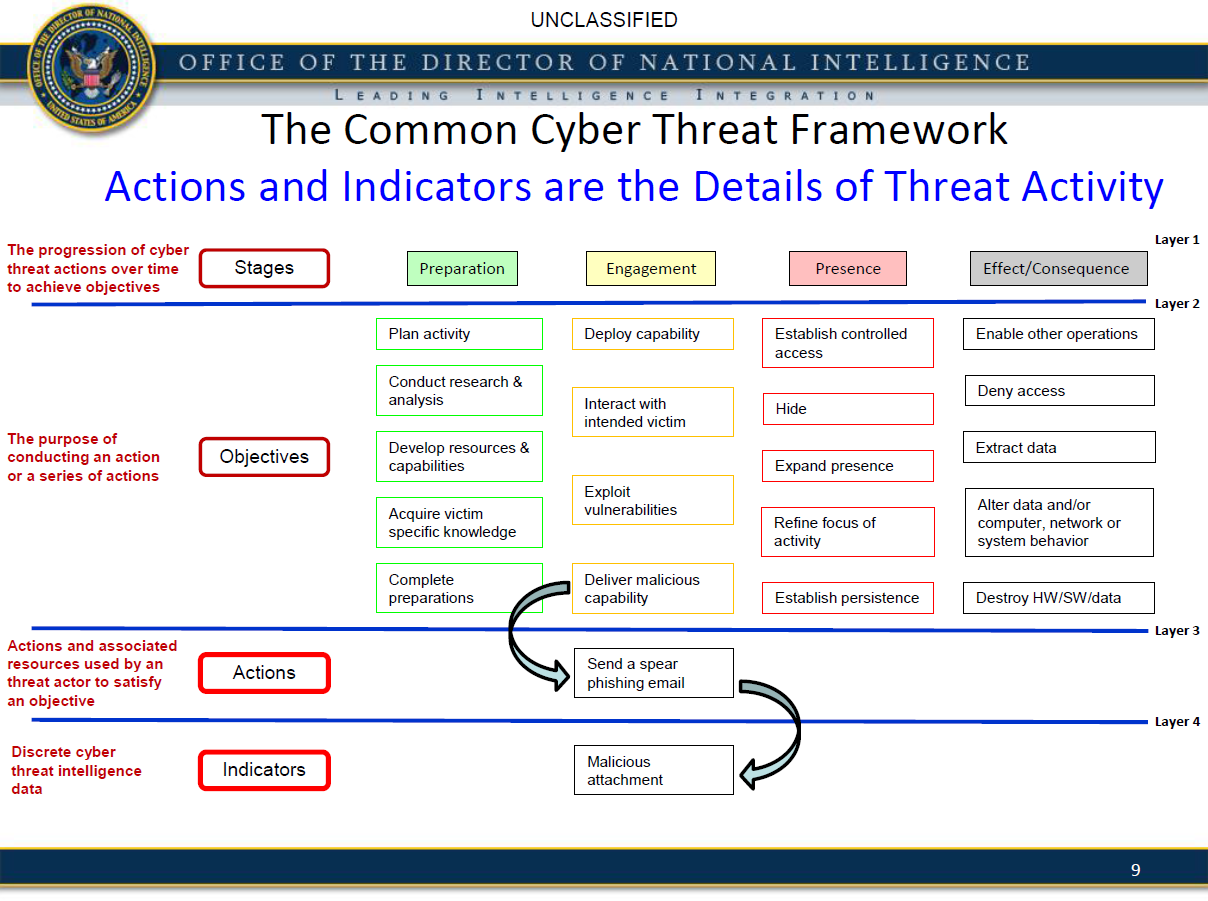
• Incorporate a hierarchical/layered perspective that allows a focus on a level detail appropriate to the audience while maintaining linkage and traceability of data
• Employ Structured and documented categories with explicitly defined terms and labels (lexicon)
• Focus on empirical/sensor-derived ‘objective’ data
• Accommodate a wide variety of data sources, threat actors and activity
• Provide as a foundation for analysis and decision-making
The Common Cyber Threat Framework
• Since 2012, the Office of the DNI has worked with interagency partners to build and refine The Common Cyber Threat Framework reflecting these key attributes and goals
• The Common Cyber Threat Framework is not intended to displace or replace an organization’s existing model which is tailored to its specific mission and requirements; rather, it is intended to:
Serve as a viable Universal Translator (a cyber Esperanto or Rosetta Stone) facilitating efficient and possibly automated exchange of data and insight across models once each has been mapped to it and the mappings shared
Provide a Starting Point featuring a simple threat model and value-neutral concepts. It can be customized for any organization as needed—and any deviations from the common approach are readily apparent, facilitating mapping and data exchange.