On February 24, 2021, President Biden issued Executive Order 14017 on America’s Supply Chains directing the Secretary of Energy to submit a supply chain strategy overview report for the energy sector industrial base (as determined by the Secretary of Energy). The U.S. Department of Energy (DOE) defines the Energy Sector Industrial Base (ESIB) as the energy sector and associated supply chains that include all industries/companies and stakeholders directly and indirectly involved in the energy sector. The energy sector industrial base involves a complex network of industries and stakeholders that spans from extractive industries, manufacturing industries, energy conversion and delivery industries, end of life and waste management industries, and service industries to include providers of digital goods and services.
As the energy sector has become more globalized and increasingly complex, digitized, and even virtualized, its supply chain risk for digital components – the software, virtual platforms and services, and data – in energy systems has evolved and expanded.
All digital components in U.S. energy sector systems are vulnerable and may be subject to cyber supply chain risks stemming from a variety of threats, vulnerabilities, and impacts. This includes digital components in all systems within the ESIB, namely those systems operated by asset owners across different energy subsectors (e.g., electricity, oil and natural gas, and renewables) and the systems operated by a worldwide industrial complex with capabilities to perform research and development and design, produce, operate, and maintain energy sector systems, subsystems, components, or parts to meet U.S. energy requirements.
Supply chain risks for digital components including software, virtual platforms and services, and data have grown in recent years as increasingly sophisticated cyber adversaries have targeted exploiting vulnerabilities in these digital assets. Supply chain risks for digital components in energy sector systems will continue to evolve and likely increase as these systems are increasingly interconnected, digitized, and remotely operated.
…
All digital components in all types of U.S. energy sector systems are vulnerable and may be subject to cyber supply chain risks stemming from a variety of threats, vulnerabilities, and impacts. This includes all systems within the U.S. Energy Sector Industrial Base (ESIB), namely those systems operated by asset owners across different energy subsectors (e.g., electricity, oil and natural gas, and renewables) and the systems operated by a worldwide industrial complex with capabilities to perform research and development and design, produce, operate, and maintain energy sector systems, subsystems, components, or parts to meet U.S. energy requirements.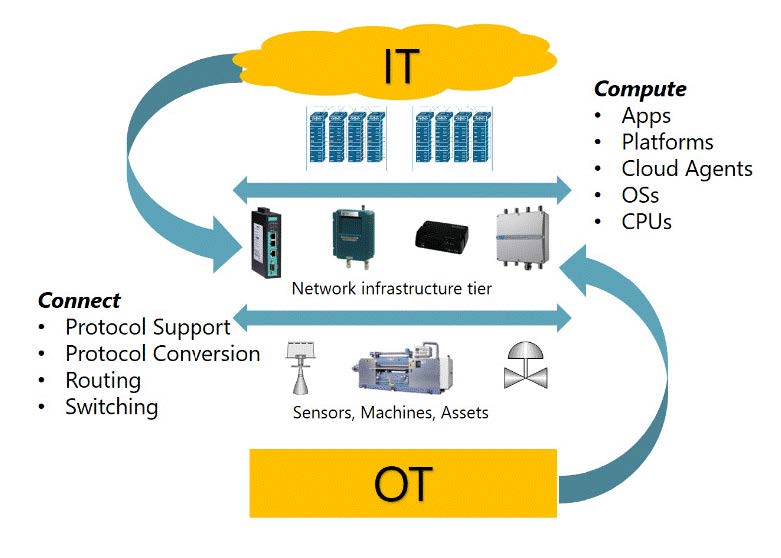
…
2.3 Reliance on Foreign Suppliers
Cyber components in energy sector systems are globally sourced in an increasingly fragmented and dynamic digital supply chain. Software for IT and OT systems is increasingly developed in foreign countries where skilled labor pools exist, internet connectivity is available, and lower wages are common. Cyber supply chain risks stem from several conditions related to this reliance on lower cost foreign suppliers of software, which may be designed, developed, manufactured, maintained, or supplied by persons owned or controlled by, or subject to the jurisdiction or direction of, a foreign adversary.
Under these conditions, software and firmware can be developed by untrusted individuals who could insert malicious code that is difficult to detect due to the size and complexity of these systems. Additionally, software, firmware, and datasets can be developed in adversary nations that practice ubiquitous collection of all digital information on networks that transit their territory, which creates an opportunity to insert malicious code or otherwise interfere in software developed within their borders or compromise the integrity of datasets.
Similarly, virtual platforms and services that are hosted in datacenters resident in some adversary nations are subject to the same types of collection and interference. The compromise of the SolarWinds Orion platform is the most serious recent example that demonstrates that any software maintenance supply chain is vulnerable to manipulation at the hands of a strategic, well-resourced nation-state operation.
…
3.2 Adversarial Artificial Intelligence
A relatively new field of research, Adversarial AI, focuses on how to corrupt, confuse, and manipulate AI models, either by interfering with their learning process or with their decision making. There are a number of types of attacks that exploit the learning and functioning of the AI, but the attack of particular relevance for the data supply chain is known as data poisoning.
Data poisoning or model poisoning involves corrupting the integrity of the dataset used in training to impact the AI model’s ability to perform correctly (i.e., make correct predictions). By inserting artfully manipulated data, researchers have demonstrated the ability to generate incorrect and inaccurate results. These manipulated results were difficult to detect and were unexpectedly persistent when introduced at an early stage of model training, even with subsequent rounds of training using unaltered datasets. For data poisoning to be successful, the attacker aims to gain access to the model’s training data, and, somewhere in the supply chain of that training data, insert malicious content specifically designed to impact the result.

