Office of Homeland Security & Preparedness Intelligence Bureau
Office of Homeland Security & Preparedness Intelligence Bureau
- 9 pages
- For Official Use Only
- January 6, 2009
Key Findings
• Both domestic and international terrorist groups have expressed interest in contaminating drinking water in the United States, and domestic groups have attempted to do so with some success. However, there are no known threats to New Jersey’s Water Sector at this time.
• The types of contaminants most likely to be used by terrorists are biological and chemical agents that are accessible, not easily susceptible to degradation, and that overcome the dilution, filtration, and disinfection aspects of the drinking water process.
• The Storage and Distribution stage of the drinking water process is the stage most
vulnerable to contamination. More specifically, although it has yet to become a
conventional threat, backflow contamination – increased pressure on the user side of the
connection, forcing water and contaminants back into distribution pipelines – debunks
traditional thought regarding the feasibility of drinking water contamination, in that it
requires fewer resources and can be instigated at access points such as fire hydrants and
most types of residential and commercial connections.Risk Overview
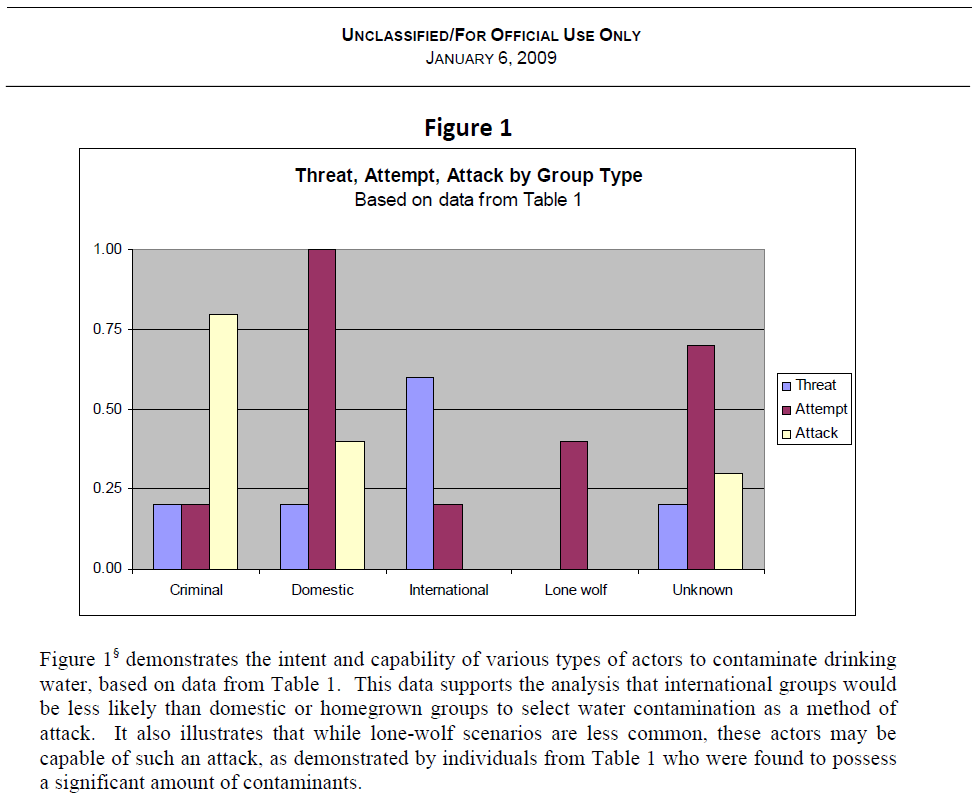
Domestic terrorist groups have historically threatened, and in some cases have executed
contamination of drinking water systems. Such groups are likely to continue targeting the Water
Sector in the future. These groups include, but are not limited to, hate groups, eco-terrorists, antigovernment and religiously motivated groups. International terrorist groups, specifically Islamic
extremists such as al Qaeda, have shown interest in contaminating US drinking water. However,
contaminating drinking water is not known to be a characteristic attack of these groups, and it is not
as sensational as an attack using explosives. The State of New Jersey Terrorism Threat
Assessment, May 2008 concludes that homegrown terrorists* are more likely to attack in the near
future than international groups such as al Qaeda – although an al Qaeda attack would probably be
more catastrophic. Homegrown terrorists may find drinking water contamination more appealing,
as they have fewer resources and would be less capable of organizing and carrying out a
sensational, large-scale al Qaeda-type attack. Additionally, “lone-wolf” actors may be capable of such an attack, and some have been found to possess significant amounts of contaminants in the
past.Contaminating drinking water could endanger public health via direct contamination, and adversely
affect overlapping sectors such as agriculture, health, fire suppression, and power generation. The
psychological effects of contamination of the drinking water supply would be far-reaching and
long-lasting. This could result in public panic and create a loss of confidence in the ability of
government and industry leaders to protect consumers.Previous instances of terrorists obtaining contaminants, as well as some successful introductions of
contaminants into water systems, demonstrate the feasibility of successfully targeting drinking
water. Table 1, at the end of this assessment, outlines specific threats to the water sector in the
United States based on open-source reporting. The data includes 26 incidents which date back to
1968. These incidents were selected based on the perceived credibility of the threat, and to
demonstrate the variety of groups and methods associated with water contamination.Types of Contaminants
The Environmental Protection Agency (EPA) has identified over 200 contaminants of interest for
intentional drinking water contamination, based on health and dispersal effects.1 To be most
effective, these contaminants would need to withstand the dilution, filtration, and disinfection
effects of the water process. This could be achieved by using contaminants in high quantity, of
high potency, or those that are not easily susceptible to degradation. Terrorists would most likely
seek out contaminants that are available and accessible on the open market.Chemical contaminants may be readily accessible, as many industrial chemicals can be obtained
online, while other chemicals such as insecticides are available at hardware and feed stores.
Additionally, chemical contaminants may be more resistant to chlorine treatment than many
biological pathogens, making them an attractive option for terrorists.2Biological pathogens are often more difficult to obtain and store, and effective delivery would be
complex and require specialized knowledge. While biological agents tend to be less accessible than
their chemical counterparts, they are still appealing as potential contaminants to the water supply,
as can be seen in historical incidents in Table 1. Additionally, as technological development
continues, cultivating biological contaminants will become easier, thereby making pathogens more
appealing for use in water contamination.Methods and Points of Access for Contamination
Raw Water Sources
Many threats received regarding the contamination of drinking water discuss introducing the
contaminant into the drinking water supply by adding a toxin to a raw water source, such as a reservoir. Intakes† are the part of the raw water stage that has the most potential for intentional
contamination. Raw source water is often easily accessible, and targeting the source stage of the
process would allow the attacker to act farther from the kill zone. However, due to the size and
residence time of water in the raw source stage, a very large amount of contaminant would be
necessary to create significant contamination of drinking water. Furthermore, because this is the
pre-treatment stage of the process, contaminants that are not easily susceptible to degradation and
that are able to maintain their toxicity throughout the treatment processes would be required for
effective contamination.Treatment
Contamination at the treatment stage of the process could be executed via physical tampering with
filtration equipment or via cyber attacks. Physical tampering with filtration equipment alone could
allow unsafe water to pass to the distribution system, but it would be most effective when
accompanied by introducing contaminants.Tampering at the treatment stage could also be accomplished via cyber attacks on the Supervisory
Control and Data Acquisition (SCADA) system, the computer network that monitors and controls
the drinking water process. Using cyber methods to contaminate drinking water could cause
chemical underdosing/overdosing, disabled service, reduced pressure flow, overflow of untreated
sewage into public waterways, or the sending of false information to operators to prevent awareness
of real-time operating conditions. A recent example of a cyber intrusion into utilities overseas is
informative. According to a recent statement by Tom Donahue, a senior CIA analyst, “We have
information, from multiple regions outside the United States, of cyber intrusions into [electric]
utilities, followed by extortion demands. We suspect, but cannot confirm, that some of these
attackers had the benefit of inside knowledge. We have information that cyber attacks have been
used to disrupt power equipment in several regions outside the United States. In at least one case,
the disruption caused a power outage affecting multiple cities. We do not know who executed
these attacks or why, but all involved intrusions through the Internet.”3 Additionally, Table 1
includes incidents of cyber intrusions which date back to at least 1994. (For additional information,
please refer to the OHSP product: The Cyber-Terror Threat, available on the OHSP secure Web
site at www.state.nj.us).Storage and Distribution
Instances of vandals gaining access to finished water storage tanks are also cause for concern, as
they demonstrate the feasibility of access to this stage of the drinking water process. In most cases,
water in storage tanks will not be treated again before reaching the consumer; the amount of water
in storage tanks is considerably less than sources in the supply stage, and would require less
contaminant for a successful attack.According to a 2004 Government Accountability Office report, as well as industry experts, the
distribution system is the stage most vulnerable to intentional contamination.4 Distribution is a
post-treatment stage of the drinking water process that includes bottling companies and distribution
pipelines. Contaminated drinking water can also affect bottling and food processing companies,
which often draw their water from the local supply. This could allow contaminated water to reach
a broader public.A potential method of contamination in the distribution stage is backflow contamination. Backflow
contamination involves changing the pressure in the distribution pipes to alter the flow and push
used/non-potable water or other substances from any domestic, industrial, or institutional piping
system back into the drinking water distribution system. Backflow can be initiated inexpensively
and without specialized knowledge or access to water supply network facilities. This method of
contamination would allow easier access, since the introduction point could be any residential or
commercial facility or fire hydrant within the distribution network. It also requires contaminants of
less potency, as this occurs in a post-treatment stage of the process.Consequences
The economic losses of an attack on the Water Sector would be considerable, as documented in the
1993 unintentional contamination of water with Cryptosporidium‡ in Milwaukee. The damage to
infrastructure, as well as cost to the health-care sector and government agencies involved in this
case, totaled around $96 million. The financial consequences of contamination vary. For example,
oil-based contaminants would be more difficult to remove from the drinking water system and may
require costly replacement of equipment that could be time-consuming, thus increasing the duration
of a denial of service and increasing the cost of replacement of infrastructure. Furthermore, the
food and beverage industry, which largely uses water from a local system in the production of its
products, would be adversely affected by water contamination.Outlook
An August 2008 posting on a Web site linked to al Qaeda demonstrates a continued interest in
drinking water contamination against the West. The post calls for an attack on the drinking water
of major cities and includes tips on how to carry out such attacks, specifically citing the use of
distribution pipelines to do so.5 Authorities have also found documents in the possession of
individuals in the United States linked to al Qaeda, regarding how to poison water supplies.
According to an interview with a senior al Qaeda member in May 2003, “The al Qaeda
organization said that it will use new methods of fighting the Americans, indicating its intention to
poison the drinking water of several American states.”…