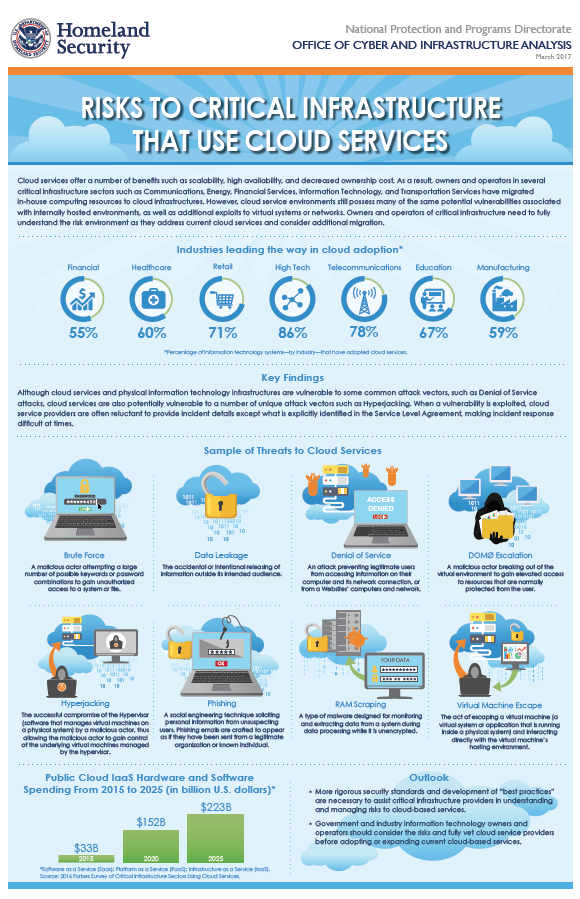
Cloud services offer a number of benefits such as scalability, high availability, and decreased ownership cost. As a result, owners and operators in several critical infrastructure sectors such as Communications, Energy, Financial Services, Information Technology, and Transportation Services have migrated in-house computing resources to cloud infrastructures. However, cloud service environments still possess many of the same potential vulnerabilities associated with internally hosted environments, as well as additional exploits to virtual systems or networks. Owners and operators of critical infrastructure need to fully understand the risk environment as they address current cloud services and consider additional migration.
Key Findings
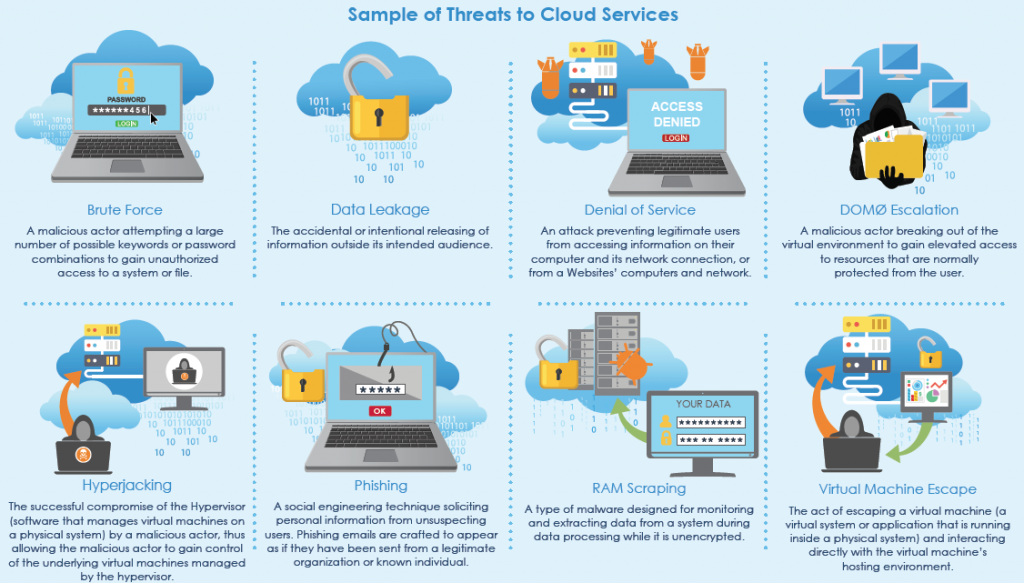
Although cloud services and physical information technology infrastructures are vulnerable to some common attack vectors, such as Denial of Service attacks, cloud services are also potentially vulnerable to a number of unique attack vectors such as Hyperjacking. When a vulnerability is exploited, cloud service providers are often reluctant to provide incident details except what is explicitly identified in the Service Level Agreement, making incident response difficult at times.
More rigorous security standards and development of “best practices” are necessary to assist critical infrastructure providers in understanding and managing risks to cloud-based services.
Government and industry information technology owners and operators should consider the risks and fully vet cloud service providers before adopting or expanding current cloud-based services.
…