Our BSA analysis of 6048 IP addresses associated with the Tor darknet found that in the majority of the SAR filings, the underlying suspicious activity, most frequently account takeovers, might have been prevented if the filing institution had been aware that their network was being accessed via Tor IP addresses. Darknets are Internet based networks used to access content in a manner designed to obscure the identity of the user and his or her associated Internet activity.
This FinCEN Executive Alert to financial institutions is for informational purposes only, and does not request financial institutions to take any specific action. The information contained in this Executive Alert is intended to be shared with your institution’s executives in BSA/AML compliance and Cyber Security.
Tor, Darknets, and Cybercrime
Darknets also known as cypherspace, the Deep web, or anonymous networks are Internet based networks that individuals use to access content in a manner designed to obscure the identity of the user and his or her associated Internet activity. Tor is the largest darknet with between 500,000 and a million users worldwide. Tor nodes are dedicated servers with an IP address that relay encrypted communications between users of the Tor darknet. They are readily identifiable through open source research.
Tor has been associated with a variety of cybercrimes, including child pornography and darknet marketplaces for illicit goods and services.
Some online businesses routinely detect IP addresses associated with Tor nodes and block these customers from accessing their services because they have determined that Tor activity often is connected to cybercrime.
Hidden Tor Connections Permeate SAR Filings
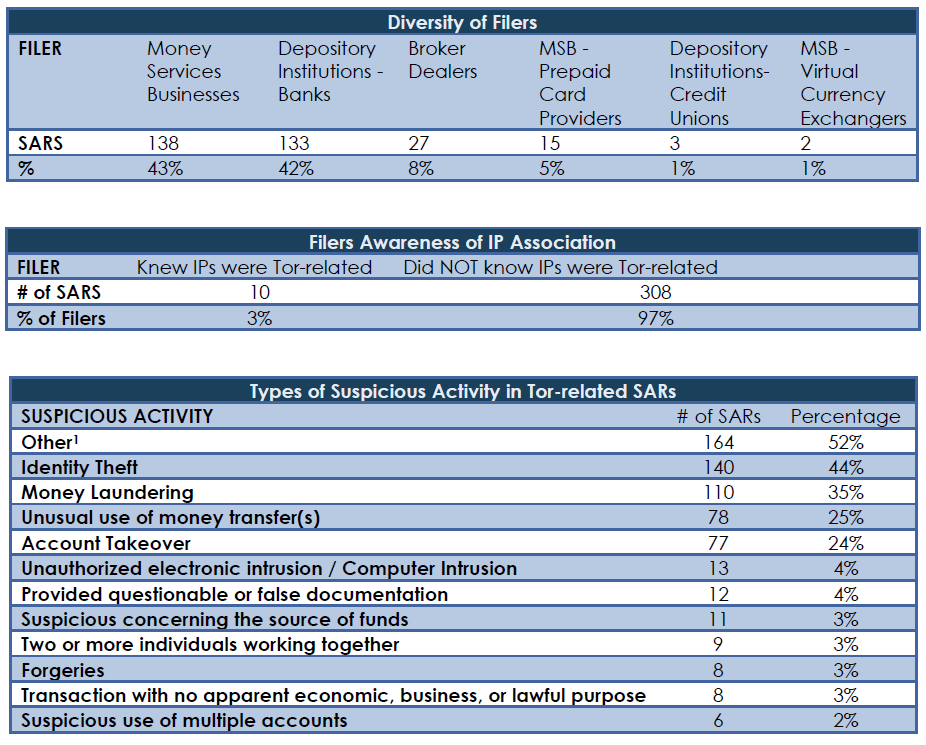
We conducted a BSA data search against a list of 6048 known Tor nodes covering the period from 8/2/2001 to 7/14/2014; this search yielded 975 hits across 318 unique documents. The transactions associated with these SARs totaled $23,888,549. Analysis of these documents found that few filers were aware of the connection to Tor, that the bulk of these filings were related to cybercrime, and that Tor related filings were rapidly rising.
An analysis of these SARs revealed that:
Filers Unaware of the IP Association with Tor. A keyword search of the narratives for “Tor” revealed that only 10 SARs referenced the Tor darknet. In two SARs, the filer filed because of a customer’s use of Tor. Even in these, however, it is unclear if knowledge of this was immediate, or after the suspicious activity in question occurred.
Identity Theft and Account Takeover Often Cited. Our analysis of the type of suspicious activity indicates that a majority of the SARs were filed for account takeover or identity theft. In addition, analysis of the SARs filed with the designation “Other” revealed that most were filed for “Account Takeover,” and at least five additional SARs were filed incorrectly and should have been “Account Takeover”.
Awareness May Be Key to Countering Tor related Cybercrime
Financial Institutions may benefit immediately from a heighted awareness of Tor nodes and incorporating this knowledge into their transaction monitoring efforts to prevent unauthorized intrusions and other cybercrime.
Our narrative analysis of SARs related to account takeovers found that the unauthorized logins to customer accounts may have been prevented if the filing institution had been aware that the IP from which the login originated was associated with a known TOR node.
The information in this document is provided to the recipient in confidence. Unauthorized release of this information may result in criminal, civil, or disciplinary sanctions under the Bank Secrecy Act (“BSA”) and other laws, and the loss of access to information. The information is to be used only to allow the recipient to aid in the government’s investigation and enforcement of the BSA and other laws, and may not be released, disseminated, disclosed, or transmitted outside your organization without the prior, written approval of FinCEN.