This FOUO report on threats to federal facilities was accidentally posted to the USDA website and then removed. This copy was obtained via Google’s caching of the document.
Interagency Security Committee Report
- 131 pages
- For Official Use Only
- April 12, 2010
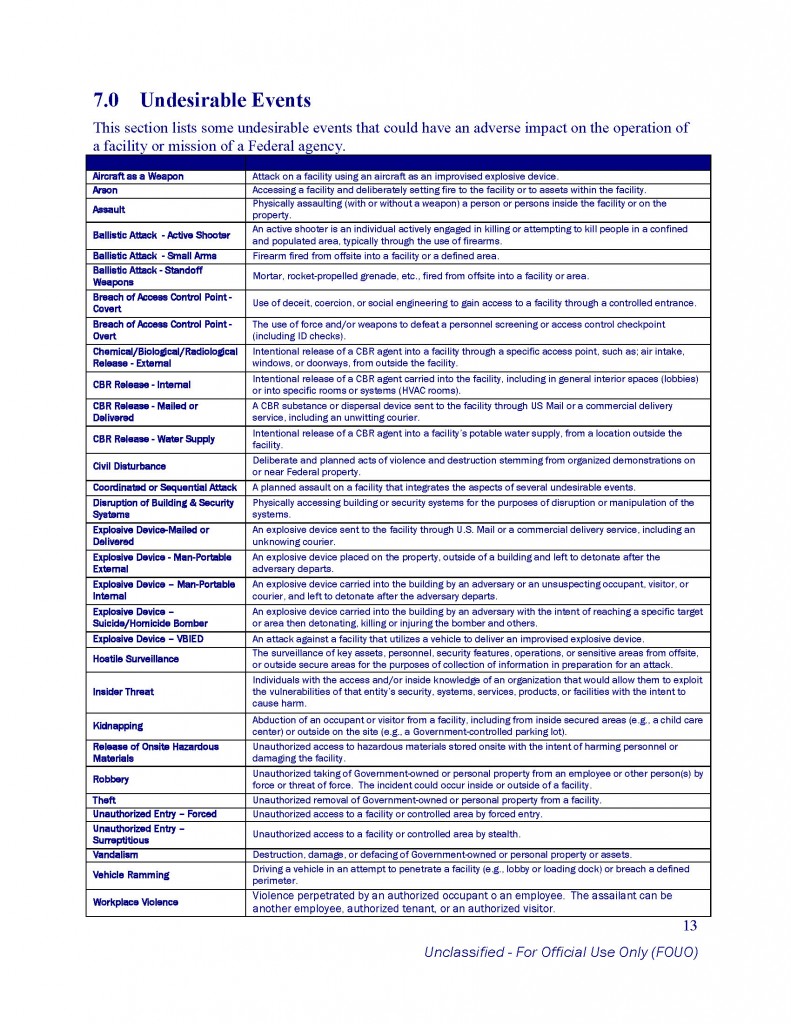
Threat Assessment of Undesirable Events
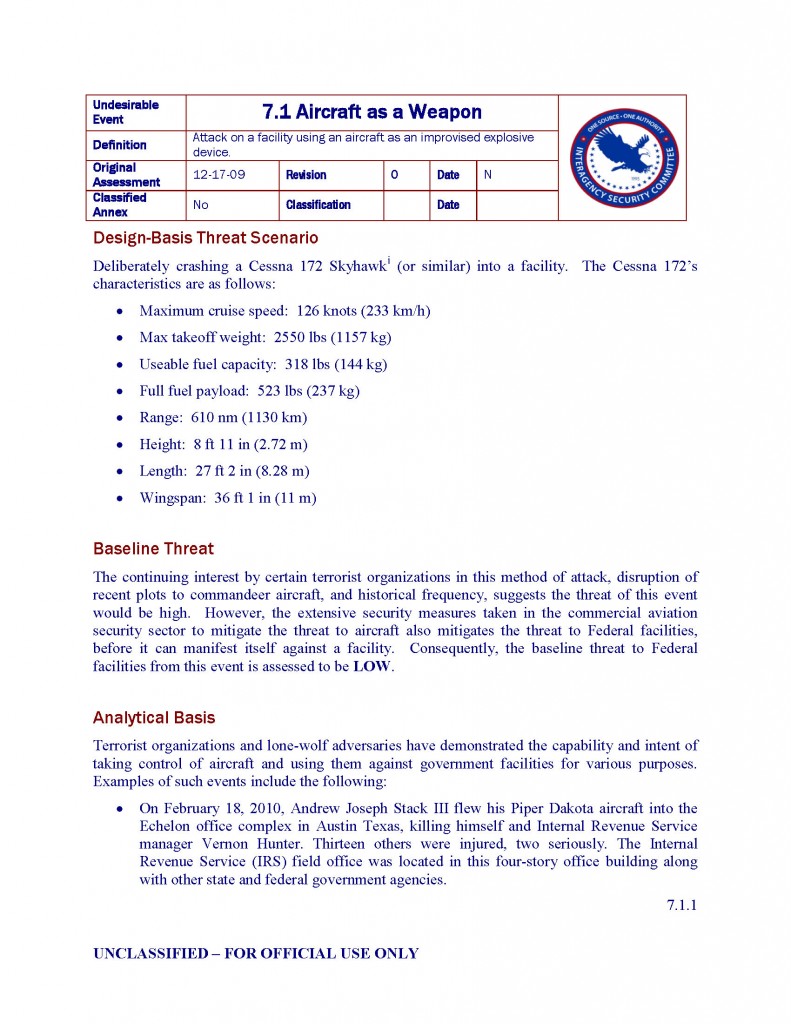
Each event is presented as a standalone document. As the need arises, event documents may be updated or replaced, and undesirable events added in order to keep this report as current as possible.
Analysis and synthesis of the threat stream – and in particular the consolidation of threat reporting from various members of the intelligence community (IC) – has been an ongoing effort since the creation of the U.S. Department of Homeland Security (DHS). Volumes of applicable information already exist in disparate reports from a variety of agencies. This document is an extension of that goal of consolidation. Where sufficient information was already collected, quality analysis conducted, or applicable reports were already prepared, that information was to be consolidated into this document. In some cases, further analysis may have been necessary to make the information more clearly applicable to the protection of Federal facilities, or to more clearly define the characteristics of an event.
In conducting this assessment, the Working Group adhered to the specifications of the 2009 DHS National Infrastructure Protection Plan (NIPP) for conducting a threat assessment:
• Broad spectrums of attack methods that may be employed have been identified.
• In identifying target attractiveness factors, each event document accounts for an adversary’s ability to recognize the target.
• In assessing events where security measures outside the influence of Federal facilities impact the planning and implementation by adversaries, the deterrence value of those existing security measures is considered. (Deterrence of on-site countermeasures is considered in determining vulnerability as part of a facility-specific-risk assessment.)
• The level of demonstrated capabilities of adversaries with regard to each particular attack method is considered.
• The degree of the adversaries’ intent to carry out such attacks against Federal facilities is considered.
• The likelihood that an adversary would attempt a given attack method against a Federal facility has been estimated.…