Progress in Near-Real Time Attack Detection at the Platform Level
Progress in Near-Real Time Attack Detection at the Platform Level
- 13 pages
- For Official Use Only
- September 13, 2010
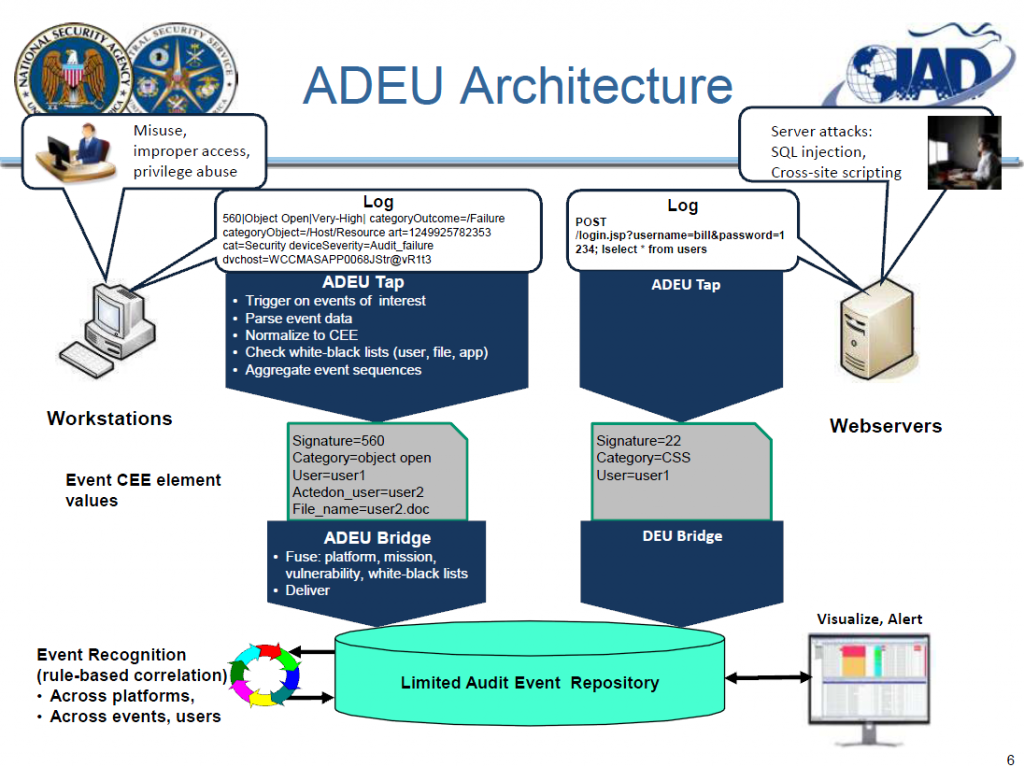
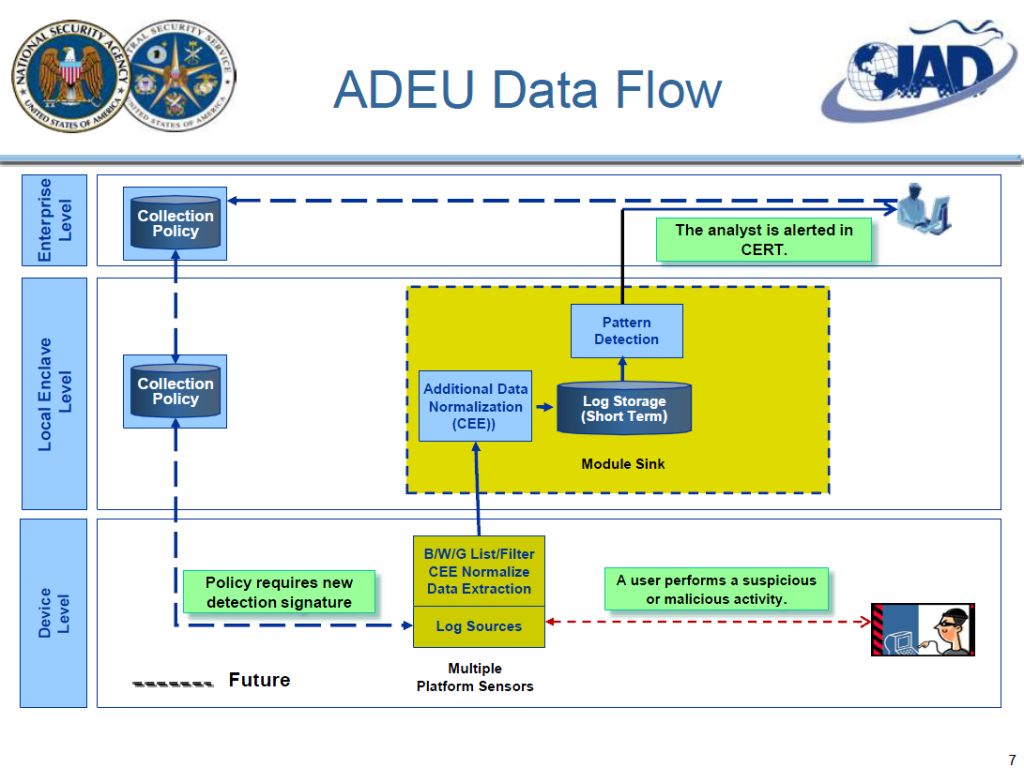
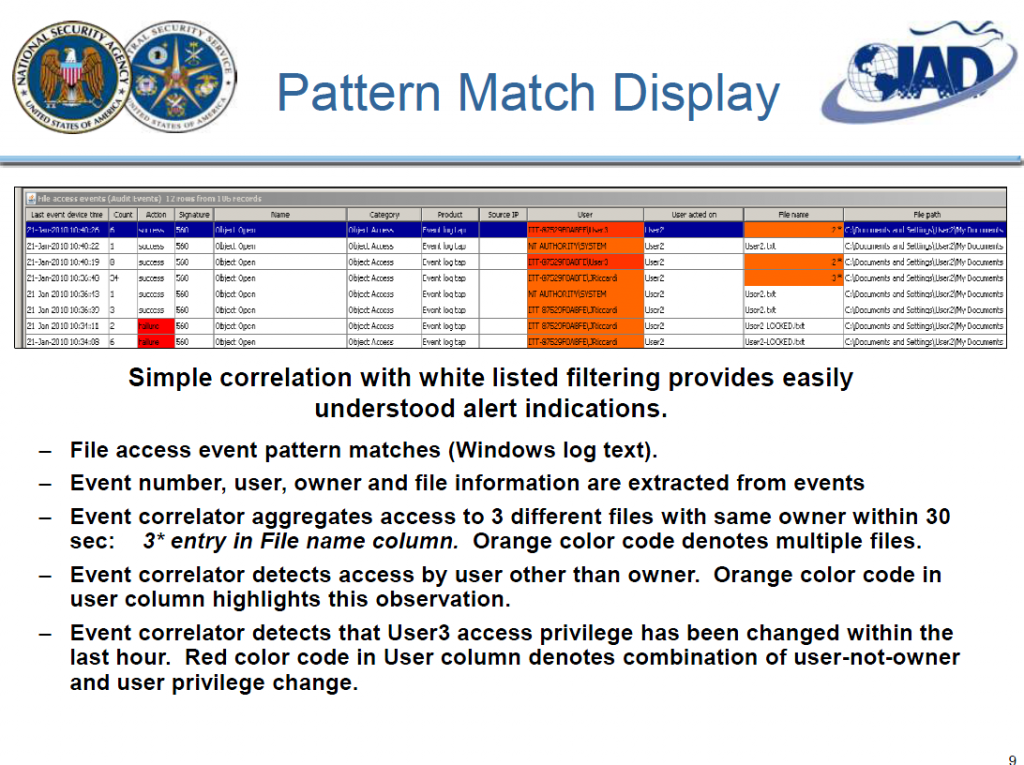
The overall objective of the this task was to architect and implement a capability that will enable automated parsing, normalization, extraction, aggregation, filtering and then detection of attack patterns based on log and log like data in near real time depending on local network settings. We call this the Audit Data Extraction Utility (ADEU).
• Real World Problems
– Audit logs are created in many different variations.
• Attack identification using multi-platform analysis nearly impossible.
– Collecting all audit and audit like data and then identifying attacks
in near real time is difficult within the current architecture.
• The massive amount of data overloads our network resources.
• Dynamic anomaly detection using audit logs creates many false
positives.
• Practical Solution
– Not all log data is needed.
• By minimizing the data elements based on detection needs, a
deployed agent can collect only the audit data required to match
defined attack use cases using static analysis.
• White-listing regular non-malicious log entries further reduces
excessive data collection
• Data normalization to an evolving standard supports automated multiplatform
analysis.…
ADEU “Flag” Lists
• Detection of non-persistent memory executable.
• Generic, configurable capability to assign a flag
value based on an event attribute:
– White-listed application (normal, ignore)
– Red-listed application (malware)
– Red-listed document (critical doc)
– Black-listed IP address (known bad)
– Yellow-listed user (suspect)
• Lookups executed client-side for false-positive
reduction using Prefetch.
• Implemented via ADEU transformation plug-in
API.…