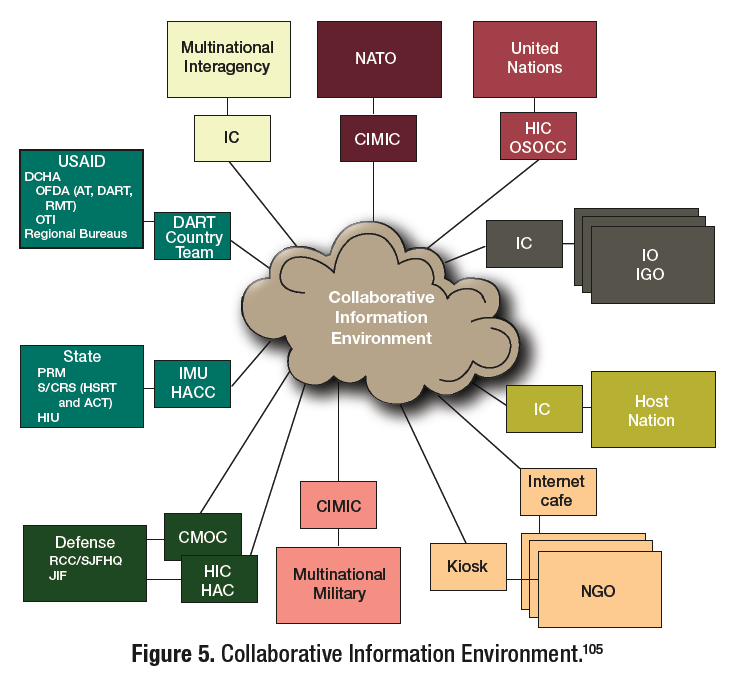
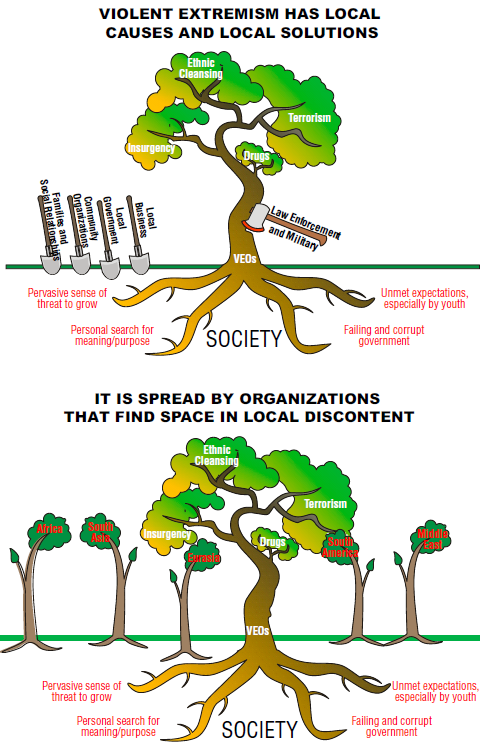
Interagency Teaming to Counter Irregular Threats Handbook
Interagency Teaming to Counter Irregular Threats Handbook
- Johns Hopkins University Applied Physics Laboratory
- 186 pages
- For Official Use Only
- December 2009
- 30.9 MB
1.1 What This Handbook Is
If you have picked up this handbook, or had it handed to you, you are likely an interagency team leader or team member or a military commander or civilian leader with the responsibility for setting up an interagency team. If this is your first exposure to working with the interagency, it can be a daunting prospect. This handbook is intended to provide you with a basic understanding of the interagency environment as well as insights and best practices that your team can put to use to counter irregular threats in the field or at operational level.
For the purposes of this handbook, “irregular threat” operations, both domestic and international, have been categorized into 10 broad areas:
- Counter Trafficking in Persons (TIP)
- Counter Weapons of Mass Destruction (WMD)
- Counternarcotics
- Counter-Threat Finance
- Homeland Defense/Homeland Security (HLD/HLS)
- Unconventional Warfare (UW)
- Counterterrorism
- Counter Cyberwarfare
- Counterinsurgency (COIN)
- Counter-Piracy
In addition to these threats, strategic communications are beginning to emerge as a concern. Although security, stabilization, nationbuilding,
and related efforts are not explicitly listed, these activities are integral parts of the approach to countering an irregular threat such as an insurgency.This handbook describes ways for you and your team to effectively engage, develop, and sustain partnerships with each other. The intent is to raise awareness of some of the issues that must be addressed in such interagency teams. The handbook includes an overview of the challenges to interagency teaming, suggests best practices gleaned from research in interagency teaming as well as from the broader fields of cross-cultural communications and organizational change; and provides resources for further study. The companion CD includes a hyperlinked version of this handbook and provides copies of a small library of relevant open-source references.
To enhance readability among a diverse audience, every effort has been made to keep this handbook as free of jargon and acronyms as is reasonably possible. The acronyms that have been used are defined in Appendix A, and Appendix B provides a glossary of some of the phrases and concepts used in this handbook. As a general rule, U.S. government departments will be referred to in this handbook by their short names (e.g., Defense, State, Justice, Homeland Security) and agencies will be referred to by their acronyms (e.g., FBI, CBP).
…
If you have picked up this handbook, or had it handed to you,
you are likely an interagency team leader or team member or a
military commander or civilian leader with the responsibility
for setting up an interagency team. If this is your first exposure to
working with the interagency, it can be a daunting prospect. This
handbook is intended to provide you with a basic understanding of
the interagency environment as well as insights and best practices
that your team can put to use to counter irregular threats in the field
or at operational level.
For the purposes of this handbook, “irregular threat” operations, both
domestic and international, have been categorized into 10 broad areas:
yy Counter Trafficking in Persons (TIP)
yy Counter Weapons of Mass Destruction (WMD)
yy Counternarcotics
yy Counter-Threat Finance
yy Homeland Defense/Homeland Security (HLD/HLS)
yy Unconventional Warfare (UW)
yy Counterterrorism
yy Counter Cyberwarfare
yy Counterinsurgency (COIN)
yy Counter-Piracy