This TC serves as a guide to describe the fundamentals of how to incorporate IO at the tactical and operational level. Appendixes A through F offer tactics, techniques, and procedures (TTP) Special Forces (SF) Soldiers can use to analyze and plan information operations. This TC implements Army and joint IO doctrine established in FM 3-13, Inform and Influence Activities, and Joint Publication (JP) 3-13, Information Operations.
This TC reinforces the definition of IO used by Army forces: IO employs the core capabilities of electronic warfare (EW), computer network operations (CNO), Military Information Support operations (MISO), military deception (MILDEC), and operations security (OPSEC), in concert with specified supporting and related capabilities, to affect or defend information and information systems and to influence decisionmaking. This TC is specifically targeted for SF; however, it is also useful to Army special operations forces (ARSOF) and the Army in understanding how SF employs IO.
…
IO should be viewed as an element of combat power, focused when and where it best supports the operation. As with other elements of combat power, there is no universal formula for the application of IO. Mission, enemy, terrain and weather, troops and support available-time available, and civil considerations are the major determinants.
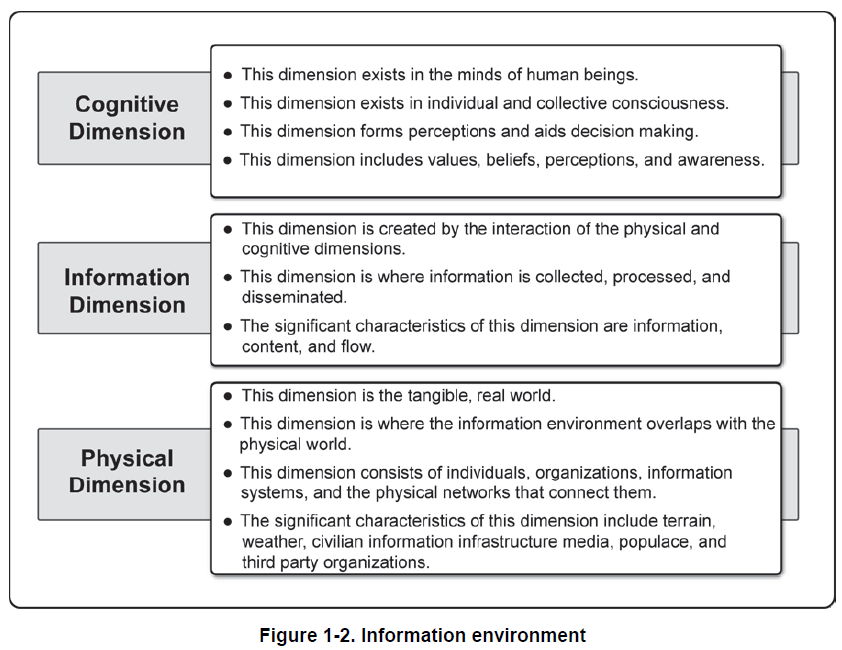
The purpose of IO is to achieve and maintain information superiority or advantage over the adversary at a particular time and place. To achieve an information advantage, an SF unit must understand the characteristics of the information environment in its operational area. The unit must also understand how adversary and third-party organizations use information to achieve their objectives.
INFORMATION SUPERIORITY
1-9. Information superiority is the purpose of IO. It is also the reason why a commander allocates resources to IO. Information superiority should not be treated as a doctrinal catch-phrase. Just as each mission’s end state is different, so is information superiority. For example, during combat operations, information superiority can be gaining surprise over the enemy or preventing the enemy from employing its reserve forces. During counterinsurgency operations, information superiority can be gaining populace support for friendly operations or preventing enemy freedom of flow. In each case, information superiority is defined specifically for the mission in terms of what advantage is sought for the friendly force.
1-10. To achieve information superiority, an SF unit uses information to actively attack the adversary and to shape the information environment to the force’s own advantage. This duality of operations—attacking the adversary and shaping the information environment—is analogous to “fires and maneuvers,” where fires equate to attacking the adversary’s ability to use information, and maneuvers are actions to seize and retain information nodes to gain a positional advantage in the information environment. To be effective, an information operation balances lethal and nonlethal activities to attack the adversary with those that shape the information environment. Through a combination of both, an SF unit seeks information superiority over its opponent.
1-11. An SF unit will rarely achieve absolute and universal information superiority. The actions of opposing forces, as well as the information content and flow in the operational area, are not static. Therefore, information superiority is a localized and transitory condition over the adversary. SF units seek information superiority at certain times and places, usually at or before the decisive point of the operation. Chapter 3 provides additional information.
…
MILITARY DECEPTION
2-11. JP 1-02 defines MILDEC as actions executed to deliberately mislead adversary military decision makers as to friendly military capabilities, intentions, and operations, thereby causing the adversary to take specific actions (or inactions) that will contribute to the accomplishment of the friendly mission.
2-12. MILDEC is more of a process or way of thinking than a capability with tangible assets and resources. It may be executed using a unit’s own troops and equipment. An effective deception does not have to be elaborate or complex; however, any time deception is part of an operation, it is the main effort for the information operation and should be included in the defined operational advantage (information superiority) provided for the mission.
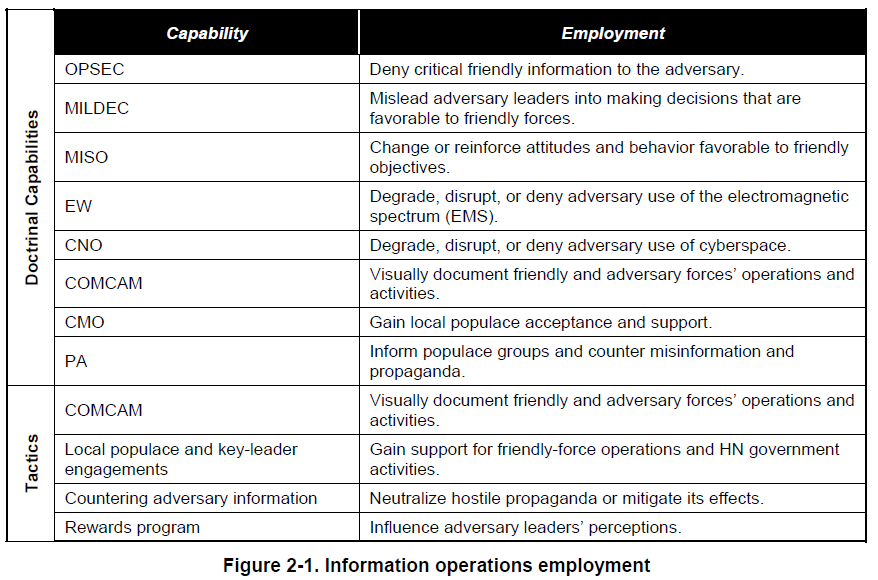
2-13. MILDEC is a method, not a result. MILDEC is not conducted merely to deceive an adversary. Deception is used only to support the mission. Figure 2-5 shows ways to employ MILDEC.
2-14. MILDEC actively targets adversary leaders and decisionmakers in support of specific battles and engagements. It creates an exploitable advantage by misleading or confusing the adversary’s decisionmaker. Distorting, concealing, or falsifying indicators of friendly intentions, capabilities, or dispositions that the adversary will see and collect can mislead or confuse the adversary. MILDEC is conducted at all levels—strategic, operational, and tactical—and must be carefully coordinated to deconflict operations between the HQ and subordinate units.
2-15. Deception in support of OPSEC is conducted to reinforce unit OPSEC and is planned using the OPSEC plan as the basis for the deception. A deception in support of OPSEC uses false information about friendly forces’ intentions, capabilities, or vulnerabilities to shape the adversary’s perceptions. It targets the adversary’s intelligence, surveillance, and reconnaissance abilities to distract the adversary’s intelligence collection away from, or provide cover for, unit operations. A deception in support of OPSEC is a relatively easy form of deception to use and is very appropriate for use at battalion-level and below. To be successful, a balance must be achieved between OPSEC and MILDEC requirements.
2-16. Camouflage, concealment, and decoys are normally individual or unit responsibilities and governed by SOP. These actions may be taken for their own ends. They can also play a role in a larger MILDEC or deception in support of OPSEC operations where camouflage, concealment, and decoys comprise just a few of many elements that mislead the adversary’s intelligence, surveillance, and reconnaissance abilities. Merely hiding forces may not be adequate, as the adversary may need to “see” these forces elsewhere. In such cases, cover and concealment can hide the presence of friendly forces, but decoy placement should be coordinated as part of the deception in support of OPSEC.
2-17. The uncertainties of combat make decisionmakers susceptible to deception. The basic mechanism for any deception is either to increase or decrease the level of uncertainty (commonly referred to as ambiguity) in the mind of the deception target. Both MILDEC and deception in support of OPSEC present false information to the adversary’s decisionmaker to manipulate their uncertainty. Deception may be used in the following ways:
Ambiguity-decreasing deception. This type of deception presents false information that shapes the adversary decisionmaker’s thinking so he makes and executes a specific decision that can be exploited by friendly forces. This deception reduces uncertainty and normally confirms the adversary decisionmaker’s preconceived beliefs so the decisionmaker becomes very certain about his COA. By making the wrong decision, which is the deception objective, the adversary could misemploy forces and provide friendly forces an operational advantage. For example, ambiguity-decreasing deceptions can present supporting elements of information concerning a specific adversary’s COA. These deceptions are complex to plan and execute, but the potential rewards are often worth the increased effort and resources.
Ambiguity-increasing deception. This deception presents false information aimed to confuse the adversary decisionmaker, thereby increasing the decisionmaker’s uncertainty. This confusion can produce different results. Ambiguity-increasing deceptions can challenge the enemy’s preconceived beliefs, draw enemy attention from one set of activities to another, create the illusion of strength where weakness exists, create the illusion of weakness where strength exists, and accustom the adversary to particular patterns of activity that are exploitable at a later time. For example, it can cause the target to delay a decision until it is too late to prevent friendly-mission success. It can place the target in a dilemma for which there is no acceptable solution. It may even prevent the target from taking any action at all. Deceptions in support of OPSEC are typically executed as this type of deception.
…
INFORMATION OPERATIONS OBJECTIVES
3-29. IO objectives describe the effects that will achieve information superiority. IO objectives do not stand alone, but support the commander’s operational intent. As such, an IO objective is a statement of what IO will do to attack the adversary or shape the environment to achieve information superiority. For example, if information superiority for an operation is “prevent target from moving from Objective Black prior to attack,” then IO objectives could be “disrupt adversary communications within Operational Area Blue to prevent early warning,” “deceive adversary decisionmakers on Objective Black to prevent relocation of C2,” or “influence local populace in Operational Area Blue to support friendly-force operations with preventing populace reporting of friendly-force activities.”
3-30. For each mission or COA considered, IO planners develop IO objectives based on the tasks for IO identified during mission analysis. Depending upon the complexity or duration of the mission (for example, a tactical direct-action mission versus a long-term FID defense mission) there may be only one IO objective or there may be numerous IO objectives developed for each phase of the overall operation. Generally, regardless of the mission, no more than five objectives are planned for execution at any one time in the operation.
3-31. When possible, IO objectives should be observable (the desired effect is detectable), achievable (assets and time are available to accomplish the objective), and quantifiable (the desired effect can be measured). The effects describe a physical or cognitive condition either in the information environment (focus on information content and flow) or against adversary forces (focus on cognition and behavior). IO objectives should not specify ways or means (that is, IO capabilities).
3-32. There is no doctrinal format for an IO objective. One possible format uses target, action, purpose, effect:
Target describes the object of the desired effect.
Action describes the capability or cognitive function of the target.
Purpose describes what will be accomplished for the friendly force.
Effect describes the outcome (for example, destroy, degrade, disrupt, or deceive).