1. This publication provides a guide for U.S. Army War College students to understand design, planning, and execution of cyberspace operations at combatant commands (CCMDs), joint task forces (JTFs), and joint functional component commands. It combines existing U.S. Government Unclassified and “Releasable to the Public” documents into a single guide.
…
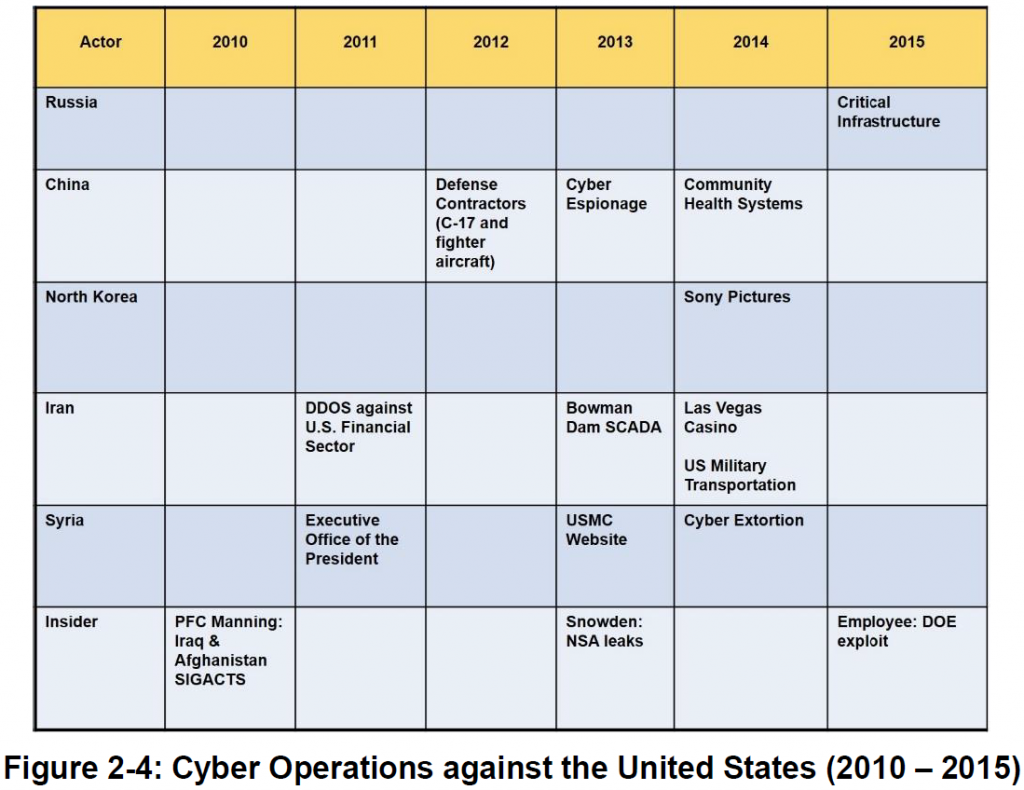
1. This guide follows the operational design methodology and the joint operation planning process (JOPP) and applies these principles to the cyberspace domain. Cyberspace is a global domain within the information environment consisting of the interdependent networks of information technology infrastructures and resident data, including the Internet, telecommunications networks, computer systems, and embedded processors and controllers. Cyberspace operations (CO) are the employment of cyberspace capabilities where the primary purpose is to achieve objectives in or through cyberspace. Commanders must develop the capability to direct operations in the cyber domain since strategic mission success increasingly depends on freedom of maneuver in cyberspace (see Figure 1-1).
2. The President and the Secretary of Defense (SecDef) provide strategic guidance to the joint force. This guidance is the common thread that integrates and synchronizes the planning activities and operations. It provides purpose and focus to the planning for employment of military force.
3. The commander and staff develop plans and orders through the application of the operational design methodology and by using JOPP. Operational design results in the commander’s operational approach, which broadly describes the actions the joint force needs to take to reach the end state. The commander and staff translate the broad operational approach into detailed plans and orders using JOPP.5 Planning continues during execution, with an initial emphasis on refining the existing plan and producing the operations order and refining the force flow utilizing employed assigned and allocated forces.
4. Commanders integrate cyberspace capabilities at all levels and in all military operations. Plans should address how to effectively integrate cyberspace capabilities, counter an adversary’s use of cyberspace, secure mission critical networks, operate in a degraded environment, efficiently use limited cyberspace assets, and consolidate operational requirements for cyberspace capabilities. While it is possible that some military objectives can be achieved by CO alone, CO capabilities should be integrated into the joint force commander’s plan and synchronized with other operations during execution.
…