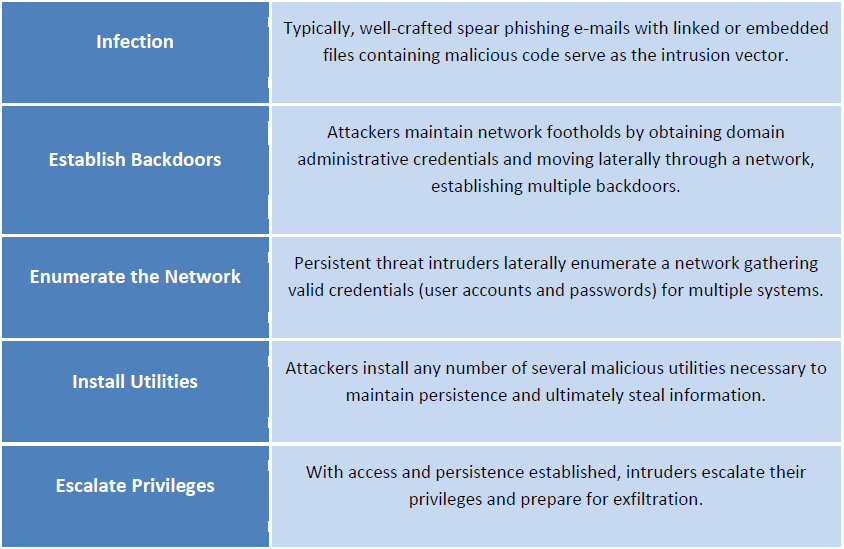
A portion of a table from the FBI Cyber Division July 8 bulletin “APT Actors Increased Interest in the Aviation Industry” describes the advanced persistent threat cycle.
Public Intelligence
Since June, advanced persistent threat (APT) actors have been targeting the aviation industry and attempting to extract confidential information by sending “spear-phishing” emails designed to trick recipients into opening malicious attachments or follow links to infected websites. According to an FBI Cyber Division bulletin from July 8, “individuals associated with the air travel industry” have received an increased number of spear-phishing emails often using spoofed senders “in an attempt to make the e-mail appear more legitimate.”
APT actors conduct targeted attacks seeking “precise information rather than monetary gain” which separates them from hacktivists or cyber criminals. Most APT activity is thought to originate from China, leading some to say that APT is basically a euphemism for China’s state-sponsored cyber espionage activities. However, the FBI bulletin never mentions a particular country in relation to the recent targeting of the aviation industry, saying that while “the activity cannot often be definitively linked to any particular nation state, the sophistication, resources, and types of information sought suggests governmental support.”
The bulletin goes on to describe APT actors as “semi-sophisticated and difficult to detect while on network systems.” They harvest “enormous amounts of critical information including proprietary data, source code, negotiation tactics, and strategic operational plans” which has reportedly cost the U.S. “hundreds of millions of dollars over the past decade.” APT actors have also “breached networks containing sensitive national security information” according to the bulletin.
While the bulletin does not provide much in the way of defensive measures, such as physically separating or “air gapping” certain systems from networked devices, the idea of mitigating data loss is emphasized. Private sector recipients of the bulletin are encouraged to ask themselves, “If proprietary data, personally identifiable information (PII), research and development-related data, e-mail, or other critical information were stolen, what would the current and future consequences be?” Employees of targeted industries should be aware of “unsolicited or unexpected e-mail containing attachments or links with caution, even (and perhaps especially) when the e-mail appears related to known events or projects.” The bulletin adds that APT activity will only eventually be mitigated by “paradigmatic shifts in cyber security.”
