The following bulletin was originally published online by Houtkin Consulting.
APT Actors Increased Interest in the Aviation Industry
- 3 pages
- For Official Use Only
- July 10, 2013
(U//FOUO) Since June 2013, the FBI has observed advanced persistent threat (APT) actors’ increased interest in the aviation industry. APT actors have sent spear-phishing e-mails targeting individuals associated with the air travel industry. Some of the spear-phishing e-mails originated from a spoofed sender in an attempt to make the e-mail appear more legitimate. E-mail recipients should be aware of suspicious and potentially malicious e-mail attachments or links.
(U) Impact of APT Activity
(U//FOUO) Every organization is at risk of being the target of an APT attack. APT actors, who are semi-sophisticated and difficult to detect while on network systems, have already cost US entities hundreds of millions of dollars over the past decade as a result of harvesting enormous amounts of critical information including proprietary data, source code, negotiation tactics, and strategic operational plans. These actors have also breached networks containing sensitive national security information. Going forward, this activity can best be mitigated with paradigmatic shifts in cyber security.
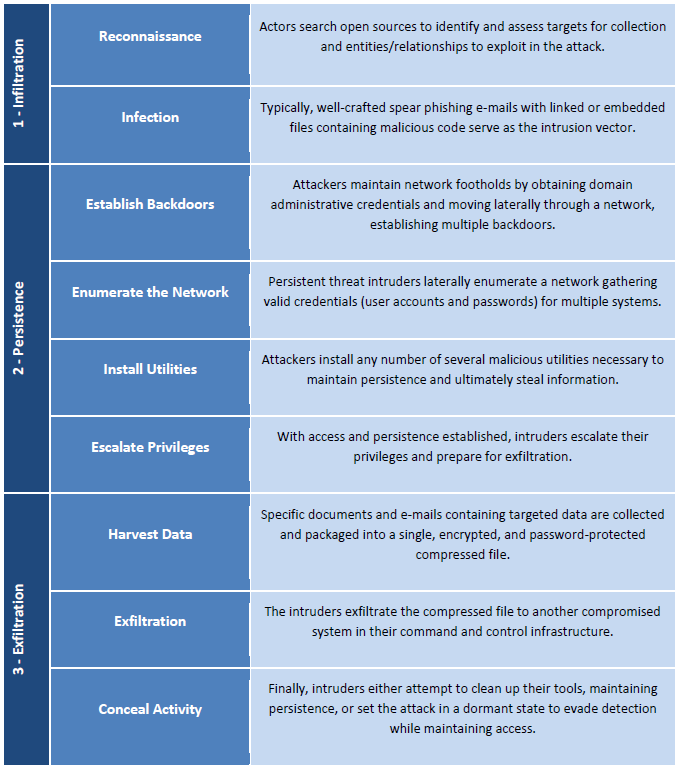
(U//FOUO) A general overview of the process by which APT actors compromise networks and systems is detailed in the table below, the vector of infection being most crucial:
(U) Defending Against APT Activity
(U) When weighing available options pertaining to the implementation of appropriate mitigation strategies, organizations must begin by asking themselves the following:
- (U) If proprietary data, personally identifiable information (PII), research and development-related data, e-mail, or other critical information were stolen, what would the current and future consequences be?
- (U) Has my organization evaluated data criticality based on risk? What must be protected in the organization?
(U) To mitigate the threat of APT activity, DHS’s United States Computer Emergency Readiness Team (US-CERT) recommends the following actions:
- (U) Audit what needs to be networked and remove (“air gap”) vital information from networked devices to ensure data protection.
- (U) Monitor for and report on suspicious activity, such as spear phishing e-mails, leading up to significant events and meetings.
- (U) Educate users about social engineering and e-mail phishing related to high-level events and meetings.
- (U) Measure expected network activity levels so that changes in patterns can be more easily identified.
- (U) Always treat unsolicited or unexpected e-mail containing attachments or links with caution, even (and perhaps especially) when the e-mail appears related to known events or projects.