Presented to the CDCA Small Business & Industry Outreach Initiative Symposium
Presented to the CDCA Small Business & Industry Outreach Initiative Symposium
- 24 pages
- For Official Use Only
- January 28, 2010
Opening Statements
▼Never before has it been possible for one person to potentially affect an entire Nation’s security.
▼In 1999 (10 years ago), two Chinese Colonels published a book called “Unrestricted Warfare” that advocated “not fighting” the U.S. directly, but “understanding and employing the principle of asymmetry correctly to allow us [the Chinese] always to find and exploit an enemy’s soft spots.”
▼The idea that a less-capable foe can take on a militarily superior opponent also aligns with the views of the ancient Chinese general, Sun Tzu. In his book “The Art of War,” the strategist advocates stealth, deceptionand indirect attackto overcome a stronger opponent in battle.Cyberspace is a Domain -The Principles of War Apply
…
According to the S.773 Bill (Cybersecurity Act of 2009) the term „Cyber‟ means:
- any process, program, or protocol relating to the use of the Internet or an intranet, automatic data processing or transmission, or telecommunication via the Internet or an intranet; and
- any matter relating to, or involving the use of, computers or computer networks.
Cyber Crosses All Domains –Sea –Air -Land -Space
…
▼In lieu of a Concise Definition
- Cyber Warfare, warfare conducted in Cyberspace, is essentially any act intended to compel an opponent to fulfill our national will, executed against the software, hardware, and firmware controlling processes within an adversary’s system.
▼Electronic Warfare
- An Overlapping Discipline (e.g. 802.11 Wireless, EMP)
- Actions involving the use of the electromagnetic spectrumor directed energy to control the spectrum
▼Information Operations (IO) / Computer Network Operations (CNO)
- Computer Network Attack –Exploitation –Defense (CNA/CNE/CND)
The Nucleus of Cyber Warfare Strategy
▼Core elements required to create a highly effective Cyber Warfare Strategy:
- Intelligence Fusion and Collaboration
−Combine intelligence from multiple sources in order to achieve inferences.
- Cyber Surveillance and Target Acquisition
−Ability to detect system compromise and assist in determining who was behind the attack.
- Adaptive Cyber Attack Countermeasures
−Capability to counterattack an incoming threat thereby destroying/altering its ability in such a way that the intended effect on the target is significantly impeded.
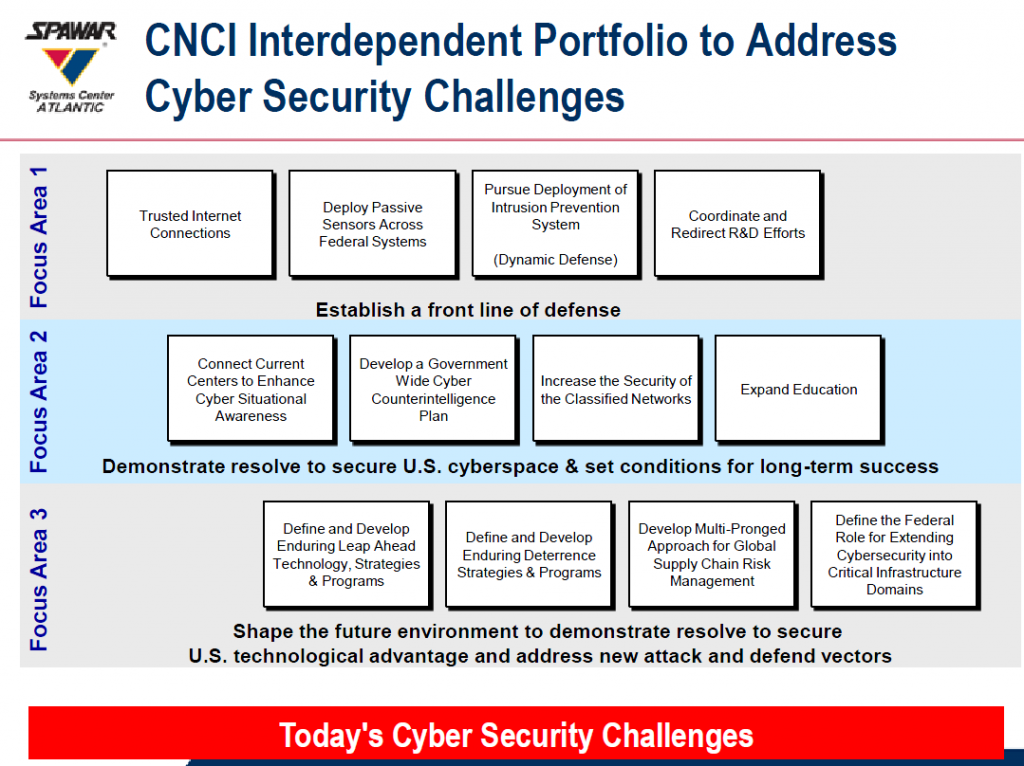
▼The President’s Comprehensive National Cybersecurity Initiative (CNCI)
- Establish a front line of defense
- Demonstrate resolve to secure U.S. Cyberspace & set conditions for long-term success
- Shape the future environment to demonstrate resolve to secure U.S. technological advantage and address new attack and defend vectorsCustomer
…