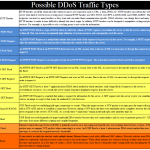
Scams, malware campaigns and attacks will continue to grow in scale and complexity as the 27 July opening ceremony in London draws near. Event organizers, sponsors and British authorities continue to increase their physical and cybersecurity awareness as the event approaches. Information systems supporting the Games, transport infrastructure, law enforcement communications, financial operations and similar will become prime targets for criminals. A collective of approximately eighty-seven UK banks exercised their ability to withstand cyber attacks last November. Olympic organizers anticipated cyber threats and began testing their cybersecurity posture during ‘technical rehearsals’ by running scenarios from their Technology Operations Center (TOC) situated on Canary Wharf. The TOC will be manned with over one hundred personnel continuously monitoring critical applications, such as the Commentator Information System, organizers’ intranet, and a telecom infrastructure encompassing 900 servers, 1,000 network and security devices, and 9,500 computers. In addition, British law enforcement organizations have been collaborating with the U.S. Secret Service and other industry experts to understand attack vectors, detection methods and mitigation strategies to combat the threat. However, the cyber implications are more expansive than localized attacks against systems and encompass globally distributed Olympic-themed malware, spam campaigns and scams.
Read more →