
A graphic from the 2017 National Counterterrorism Center handbook on indicators of mobilization to violence among homegrown violent extremists depicts a man watching a video of Anwar al-Awlaki.
The National Counterterrorism Center (NCTC) has released a 2017 version of their handbook for spotting indicators of mobilization to violence among homegrown violent extremists (HVEs). The guide was originally intended for distribution among public safety personnel and is not intended for public release, but has since appeared on several publicly accessible law enforcement mailing lists and conference websites. In 2014, the NCTC’s Office of National Intelligence Management formed an Interagency Analytic Focus Group with members from the Department of Homeland Security, Department of Energy, FBI, NSA, as well as representatives of state and local law enforcement. The focus group “collaboratively developed the list of behavioral indicators and ranked them into three tiers of diagnosticity,” eventually developing a list to distribute to law enforcement personnel. The 2017 handbook released by NCTC is a version of that list updated with new indicators observed since the handbook was last published.
Intended to provide “a roadmap of observable behaviors that could inform whether individuals or groups are preparing to engage in violent extremist activities,” the handbook is a slick 36-page publication with colorful graphics depicting dozens of behavioral indicators that an HVE is mobilizing to violence. These behaviors are divided into three groups based on their overall diagnostic capacity. Group A includes indicators that are “very diagnostic on their own” and thus require little else to indicate mobilization to violence. These indicators include “preparing or disseminating a last will or martyrdom video/statement” as well as “planning or attempting to travel to a conflict zone to fight with or support an FTO.” Group B includes indicators that are “moderately diagnostic, more so when observed with other indicators.” These include more common activities that may not directly indicate an imminent threat of violence, such as “posting terrorist icons/flags/prominent figures to social media” and “expressing acceptance of violence as a necessary means to achieve ideological goals.” Group C includes indicators that are even more common and thus are “minimally diagnostic on their own,” requiring the “presence of other indicators to gain diagnosticity.” This group includes “unusual purchase of military style tactical equipment” and “blaming external factors for failure in school, career, or relationships.”
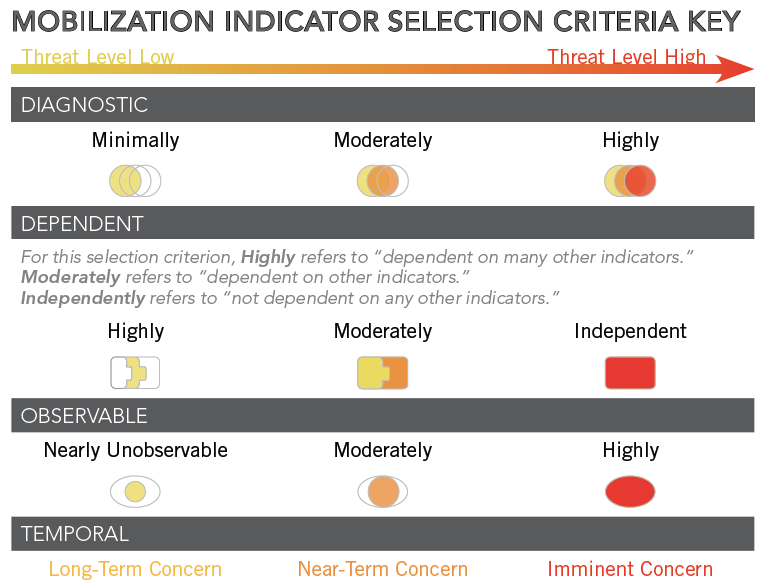
A graphic depicting the scale of threat levels assigned to various behavior indicators of mobilization to violence among HVEs.
The guide also introduces a scale for evaluating the overall threat level of indicators by ranking: how diagnostic they are in positively identifying mobilization to violence; how dependent they are on other indicators to positively diagnose mobilization; how easily observable the indicators are; as well as whether the indicators present a long-term, near-term, or imminent concern. For example, someone “disseminating a last will or martyrdom video/statement” is ranked as highly diagnostic, independent of other indicators, and observable, presenting an imminent concern. An indicator like “surveilling potential targets” is moderately diagnostic and observable, but is highly dependent on other indicators and only presents a near-term concern.
While some of the initial indicators in Group A seem plainly apparent as being indicators of mobilization towards violence, many indicators in the Group B and C are broad and at times confusing in their origin. One indicator in Group C is “inappropriate use of what an individual perceives as ‘doctrine’ to manipulate the behavior of parents, co-workers, close friends and family.” The guide offers examples of this indicator including “criticism of parents’ clothing choices, reading material choices, musical preferences, religious practices, interfaith friendships.” Another broad indicator in Group B is “use of encrypted media applications to engage with unknown overseas individuals.” Several indicators in Group C also relate to communications privacy, such as “utilizing communication security techniques” and “discussing operational security.” Many of these indicators are rated as being dependent upon other evidence “pointing to terrorism and intent to take violent action” and the guide makes clear that “many of these signals or indicators—some of which might involve constitutionally protected activities—may be insignificant on their own.” If any public safety personnel receiving the guide “reasonably believes” based on the information contained in the guide “that an individual may be mobilizing to violence “they are encouraged to “inform LE agencies with investigative authorities via mechanisms like E-Guardian or Suspicious Activity Reporting.”
