(U//FOUO) The Department of Homeland Security (DHS) assesses that given the high value of patient information and proprietary data on the black market, the Healthcare and Public Health Sector will continue to be one of the primary targets for malicious cyber actors. Stolen health data sells on the black market for more than 10 to 20 times the price of stolen credit card data. DHS assesses that growth in the medical device market over the next 4 years will result in more devices connected to the Internet, and an increase in the number of cyber-related incidents that target those devices. This is partly because manufacturers do not place enough emphasis on the security of medical devices.
…
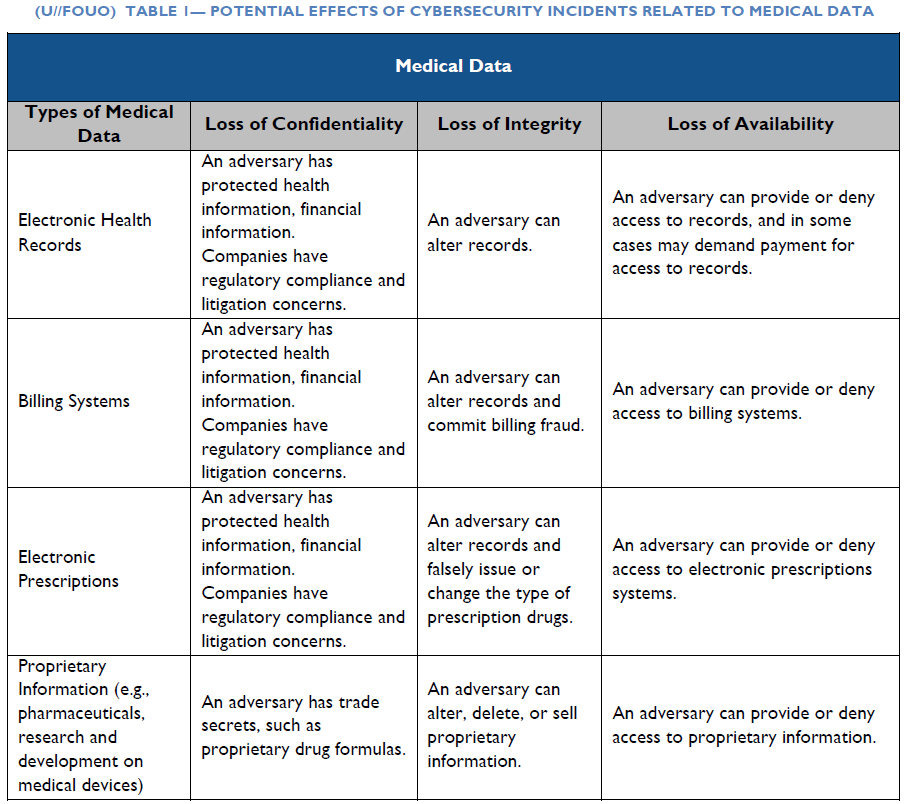
(U) CYBER INCIDENTS AFFECTING MEDICAL DATA
(U//FOUO) Electronic Health Records can contain personal data such as names, birth dates, addresses, Social Security numbers, insurance policy numbers, diagnosis codes, billing information, employment information, and income. Criminal and nation-state cyber actors use malware to exfiltrate personally identifiable information (PII), protected health information, and intellectual property data from healthcare companies for illicit financial gain, stock manipulation, or industrial espionage. Malicious cyber actors sell stolen electronic health records on the black market for more than 10 to 20 times the price of stolen credit card data.24,25 Malicious cyber actors can use this data to open new credit accounts, access an individual’s personal financial accounts, falsify medical identities to buy prescription drugs or medical equipment, or file fraudulent claims with insurers.
(U//FOUO) Some methods of attack used by malicious cyber actors against the Healthcare and Public Health Sector include ransomware or distributed denial-of-service attacks (DDoS). New ransomware variants display increasingly advanced function and capabilities such as targeted delivery techniques, obfuscation mechanisms, persistence capabilities and backup system deletion tools that likely constitute a high threat to the Healthcare and Public Health Sector.
(U//FOUO) According to a Federal Government official, advanced persistent threat malware infected eighty percent of U.S. healthcare network systems in late August 2015. DHS Industrical Contorl Systems Cyber Emergency Response Team (ICS-CERT) uncovered a total of 1.66 gigabytes of data staged for exfiltration. One system contained 290 malware samples, with 76 samples being unique.26
(U//FOUO) On June 23, 2016, the criminal hacker group known as Armada Collective sent an email to a U.S. healthcare company based in Rhode Island threatening to conduct a DDoS attack if the company failed to pay a ransom in Bitcoin. As of mid-October 2016, State officials reported the company did not pay the ransom and a DDoS attack did occur.27
(U//FOUO) A ransomware attack in March 2016 compromised a U.S.-based hospital using an outdated server vulnerability, according to a state government official with direct access to the information. The cyber actors used administrator-level access to locate and encrypt more than 100,000 files on 4,000 systems, including 600 servers. This attack denied hospital personnel access to sensitive files for two days, according to the same reporting.28
(U) On February 5, 2016, malicious cyber actors encrypted access to patient medical records and other essential computer systems at a Los Angeles, California hospital. Hospital administrators paid the cyber actors a ransom of $17,000 to regain access to their computer systems.