The following CNSS publication was obtained from IDmanagement.gov.
Committee on National Security Systems
- 42 pages
- For Official Use Only
- May 23, 2012
Over the past ten years, the Federal Government has made concerted advances in the development and implementation of Identity, Credential, and Access Management (ICAM). This progress includes capabilities designed to promote interoperability, assured information sharing, and efficiencies of scale across all agencies within the Federal Government. Recently, several high-visibility events have focused attention on classified networks with a renewed emphasis on information protection within the information sharing paradigm. Organizations must strive to ensure responsible sharing and safeguarding of classified information by employing advanced capabilities that enable a common level of assurance in information handling and sharing while ensuring the interoperability required to satisfy mission requirements.
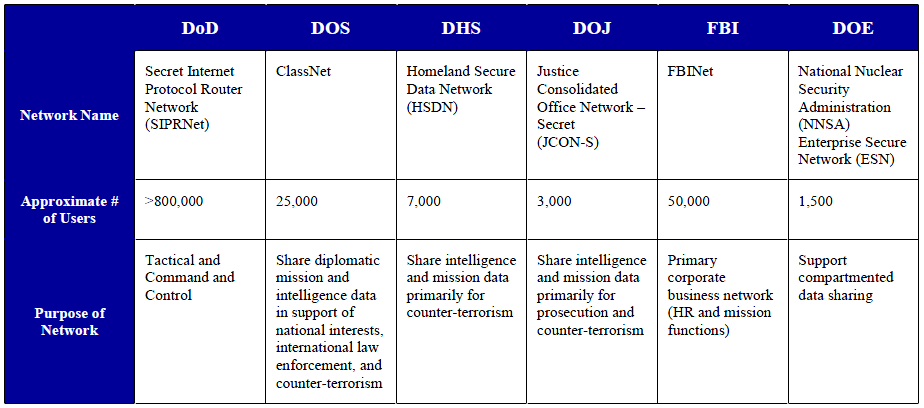
In response to these and other drivers, the National Security Systems (NSS)’s Identity and Access Management (IdAM) Working Group, the Federal Chief Information Officer (CIO) Council / ICAM Subcommittee (ICAMSC), and the National Security Staff / Information Sharing and Access (ISA) Interagency Policy Committee (IPC)’s Assured Secret Network Interoperability (ASNI) Working Group collaborated to evaluate the applicability of the Federal ICAM Roadmap and Implementation Plan (FICAM) to U.S. Secret networks and identify obstacles to the future interoperability of the Federal Secret Fabric. This document is based on analysis of the ICAM capabilities of six predominant Secret networks in use within the Federal Government:
- Department of Defense (DoD) Secret Internet Protocol Router Network (SIPRNet)
- Federal Bureau of Investigation (FBI) Network (FBINet)
- Department of Energy-National Nuclear Security Administration (DOE-NNSA) Enterprise Secure Network (ESN) Note: This analysis focuses on the DOE-NNSA ESN. Other networks at DOE were not included in this data.
- Department of Homeland Security (DHS) Homeland Secure Data Network (HSDN)
- Department of Justice (DOJ) Justice Consolidated Office Network – Secret (JCON-S)
- Department of State (DOS) ClassNet
This document represents a snapshot of the state of governance, policies, and implementation status of Secret networks as of December 12, 2011. There were several key findings as a result of this analysis:
- FICAM is applicable to Secret networks with some changes in the technical implementation to account for the unique requirements of classified networks
- The agencies evaluated have different levels of maturity in the implementation and realization of the FICAM vision, but all agencies recognize the need to move toward that vision
- Lack of authoritative policy and governance structures has led to divergent ICAM implementation approaches among many agencies
- Most agencies lack a common technical approach to ICAM implementation illustrated by the following:
- Currently, there is no common and interoperable credential employed on Secret networks
- There is no common way to capture, compile, and evaluate identity or resource attributes on Secret networks
- There is no common end-to-end approach (people, process, technology) to interoperability and information sharing between agencies – information sharing successes are mostly limited to mission-specific systems to meet specific mission needs
- There are ICAM requirements unique to classified networks that are not currently addressed in FICAM (i.e., physical protection of end points, cross-domain data transfer, etc.)
- In partnership with the Secret network community, additional work is needed to identify a viable roadmap and implementation plan for FICAM on Secret networks including provisions for:
- Developing Implementation Best Practices
- Incorporating Security and Privacy Needs within the ICAM Enterprise Architecture
- Aligning ICAM Architectures from multiple organizations, enclaves, and security domains
Together, the CNSS, ICAMSC, and the Program Manager for the Information Sharing Environment (PM-ISE) will continue to work to identify solutions to these obstacles and forge a path for implementation of robust and interoperable ICAM capabilities on the Federal Secret Fabric.
The CNSS, Information Security & Identity Management Committee (ISIMC), ICAMSC, and ASNI Working Group reviewed and approve the release of this document.