1.0 PURPOSE
The purpose of this white paper is to provide an in-depth examination of ABI-like analytic techniques that were developed, refined and employed to successfully support multiple, high-level, but dissimilar interagency law enforcement investigations over an extended period of time. The premise of this paper is that, as the Intelligence Community developes a strategy, framework and roadmap for enterprise-wide adoption of ABI, lessons learned from the law enforcement community are worthy of examination and possible incorporation into the IC strategy for ABI.
This paper consists of the following components:
THE CASE – why lessons learned in an interagency law enforcement context are applicable to ABI
INFORMATION SHARING, INTERAGENCY COOPERATION AND OSINT – how and why ABI-like processes for exploiting and integrating information from multiple sources were developed and implemented, as well as examples
CLOSING THOUGHTS – the value of DOMEX and TEO
2.0 THE CASE
As the concept of Activity-Based Intelligence (ABI) moves from a tactical/operational focus to the development of an enterprise-wide, strategic-level approach and the community begins to lay out a roadmap for ABI, it is imperative that we identify and, where appropriate, incorporate experience and lessons learned from multiple mission areas. And, given that ABI is evolving out of intelligence support to military and law enforcement operations, an examination of some of those lessons learned might enhance and further the development of that roadmap and, ultimately, ABI processes and methodologies in a broader sense.
The methodologies described herein were developed primarily for intelligence support to high-level, interagency law enforcement operations. All of the cited examples are highly sanitized, but drawn from real investigations and operations. And, while all began as single-agency investigations – some of which were civil and not criminal in nature, the cited examples eventually evolved into cooperative, interagency investigations and operations. Many of these investigations produced actionable intelligence for other elements of the Intelligence Community and some proved to be directly actionable by military units overseas.While the practice of ABI in these examples was done manually for the most part, it shares a great deal in common with the practice of ABI as it exists today and as it is evolving. Verifiable and provable information from the public domain (OSINT) was integrated into intelligence products generally without regard for the source. Law enforcement data provided rich detail, while OSINT gave that data context and, to a great extent, led to the discovery of previously unidentified information (aliases, addresses, personal and business relationships, etc.) about target organizations and individuals that could be used to revisit other sensitive and classified sources. Furthermore, given advancements in technology, all are suitable for automation in the ABI context.
…
3.1 Development of the Processes. Illicit activities frequently are not susceptible to collection by traditional or technical means, but, in the digital age, they do leave footprints if one knows where to look. And, given the nature of the global security environment and the overlap of threats, activities and operations, intelligence activities at all levels demand a different mindset and innovative approaches, focusing on elements of information and analytic practices not routinely incorporated into traditional “all-source” analysis. To best illustrate the application of these approaches, domestic law enforcement operations and overseas military and intelligence operations in the prelude to and aftermath of 9/11 clearly demonstrated a significant overlap between a broad range of criminal activities, insurgency and terrorism, as well as the value of information sharing and interagency coordination.
The examples provided below, although sanitized, are drawn from almost 15 years of trial and error, experimentation, and continuous refinement of processes in an interagency environment:
Law enforcement investigations of Mexican methamphetamine Drug Trafficking Organizations (DTO) in the early 1990s identified the emergence of individuals with ties to radical Islamic groups as suppliers of precursor chemicals to major Mexican DTOs.
Although this phenomenon initially appeared in the U.S. Southwest, follow-on enforcement programs and associated investigations documented the fact that the diversion of precursor chemicals by individuals and organizations with ties to radical Islamic groups was a well-financed and well-coordinated nationwide phenomenon with broad international reach.
Progressive, iterative integration of interagency information with information from the public domain revealed sources and means of financing for multiple networks of small businesses that facilitated a wide range of criminal activities, including: diversion of precursor chemicals, money laundering, illegal alien smuggling, drug trafficking, arms trafficking and material support to terrorism and documented even more extensive associations with radical Islamic groups.
The progressive integration and analysis of interagency and public domain information revealed not only details of target networks, but also connections to other, similar networks via identification of sources and means of financing and a variety of other, less visible but identifiable links.
By the late 1990s, individuals and organizations with direct and indirect ties to radical Islamic groups had established themselves as the preeminent nationwide suppliers of precursor chemicals, especially pseudoephedrine, to Mexican methamphetamine DTOs.
Several investigations involving the diversion of precursor chemicals – a civil offense, evolved into federal counterterrorism investigations, one of which – a chemical diversion investigation – culminated in the arrest of the so-called “Lackawanna Six” in 2003.
Associated Document and Media Exploitation (DOMEX) missions uncovered a number of actionable international connections, elements of which were coordinated with the Intelligence Community (IC) and the Department of Defense (DoD).
Analysis of law enforcement information and subsequent coordination with DoD revealed details of an extensive stateside criminal network associated with radical Islamic groups that is involved in organized retail theft, drug trafficking and the purchase and transportation of used automobiles to the Middle East. Some of the automobiles purchased and transported by this network were used or intended for use as VBIEDs in Iraq.
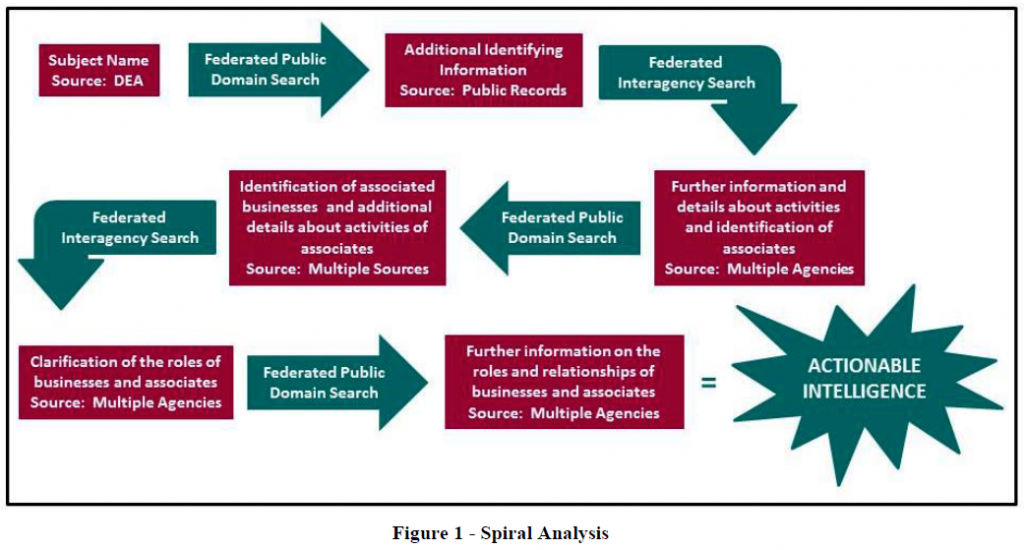
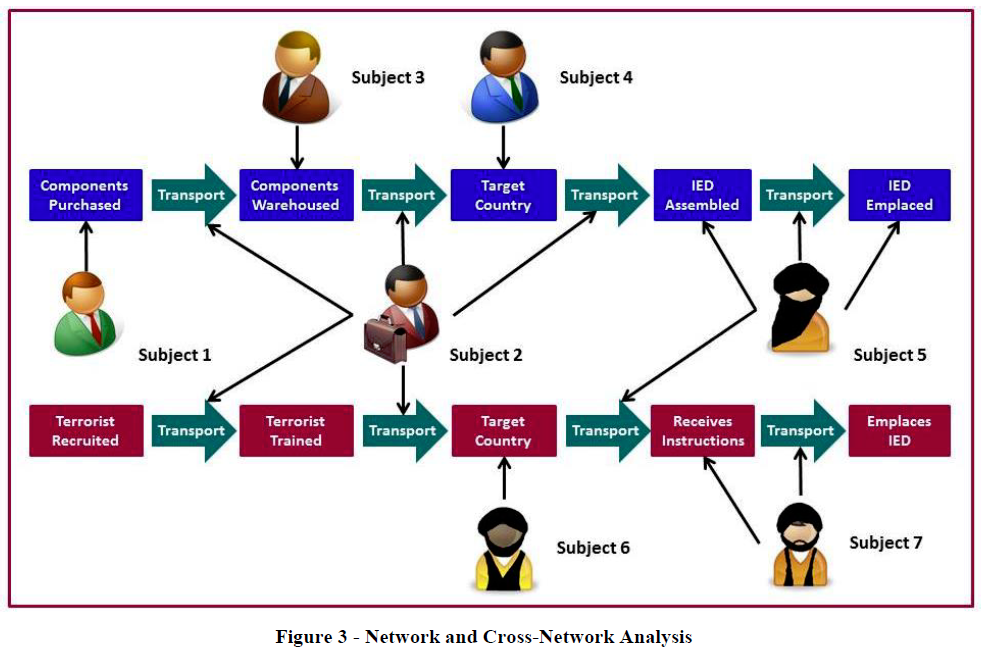
One of the most potentially exploitable commonalities of criminal, insurgent and terrorist groups and other non-state actors is their dependence upon financial support from a broad variety of state and non-state sources. All use a multitude of means to move and dispose of funds and support operations in multiple locations. Much of the information necessary to identify those transactions resides with law enforcement sources and within the public domain. Intelligence support to interagency investigations and operations in this environment led to the development and refinement of approaches like Spiral Analysis, Counter-Threat Finance Analysis, Network and Cross-Network Analysis, and Event-Based Pattern/Trend Analysis.
…