Building Security Measures May Impact Emergency Response to Attacks by Violent Extremists
- 1 page
- For Official Use Only
- December 6, 2013
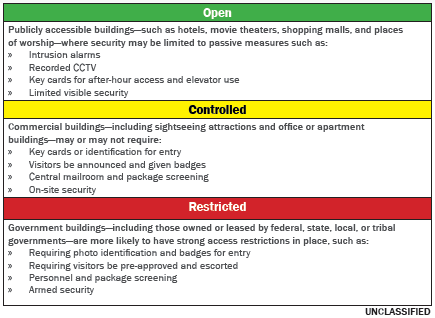
(U//FOUO) Facility security measures, such as interior control points or exterior barriers, may require first responders to adjust normal protocols and procedures to operate rapidly during emergencies. The timeline below is an overview of attacks and plots against US-based facilities with varying levels of security. The diversity of tactics and targets used underscores the need for interagency exercises and training that incorporates multiple scenarios to account for building security measures likely to be encountered.
(U) First Responder Response Considerations:
(U//FOUO) Conducting periodic exercises with building authorities and interagency partners will help responders tailor a coordinated response to the unique security characteristics of the site
and increase efficiency during an emergency. Engagement with partners may address a number of issues including:»» (U//FOUO) Building emergency response plans that identify the key staff members to assist and advise first responders as well as their roles and responsibilities during crisis;
»» (U//FOUO) Interior building control points which may limit responder access to areas and affect the rapid deployment of tools and equipment;
»» (U//FOUO) Building access control systems: the availability of master keys or swipe cards to provide full access and/or entry into restricted areas;
»» (U//FOUO) The existence of exterior building security measures which may affect the placement of response vehicles or the ability to ventilate building and rescue victims;
»» (U//FOUO) Closed circuit television (CCTV) monitors to maintain situational awareness and to assist with accountability and evacuation of building occupants; and
»» (U//FOUO) Suspicious activity reporting training to building staff and tenants to help identify and disrupt potential preoperational activity or actual attacks.