The Department of Homeland Security Office of Cyber and Infrastructure Analysis (DHS OCIA) produces cyberdependency papers to address emerging risks to critical infrastructure and provide increased awareness of the threats, vulnerabilities, and consequences of those risks to the Homeland. This note informs infrastructure and cybersecurity analysts about the potential consequences of cyber-related incidents in the Nuclear Reactors, Materials, and Waste Sector and its resilience to such incidents. This note also clarifies how computer systems support infrastructure operations, how cybersecurity incidents compromise these operations, and the likely functional outcome of a compromise.
For this note, infrastructure cybersecurity incidents are defined as actual and potential events that exploit cybersecurity vulnerabilities. Cyber attacks can disrupt or corrupt normal operating conditions in computer systems; networks; industrial control systems (ICS); or electronic devices that control, monitor, or support the function of infrastructure. Infrastructure is cyberdependent when it relies on computers or information technology to support its physical operations and essential functions.
This note focuses on the potential impacts of incidents on various types of Nuclear Reactors, Materials, and Waste Sector cyberdependent systems and functions. A cybersecurity incident at a Nuclear Reactors, Materials, and Waste Sector asset may have no effect on the infrastructure itself, yet still affect the Sector by the addition of new protective requirements. So many safeguards exist that cyber attacks against a nuclear power plant are not likely to succeed without the aid of authorized personnel within the restricted access areas. Analysis of complex, sophisticated, and distributed cyber attacks against multiple Nuclear Reactors, Materials, and Waste Sector assets is beyond the scope of and resources available for this note.
DHS OCIA developed this note with input from the Idaho National Laboratory and in coordination with the DHS National Protection and Programs Directorate (NPPD) Office of Infrastructure Protection and the DHS NPPD Office of Cybersecurity and Communication Industrial Control Systems Computer Emergency Response Team (ICS–CERT); National Infrastructure Simulation and Analysis Center (NISAC); the Nuclear Regulatory Commission (NRC); and representatives of the Nuclear Reactors, Materials, and Waste Sector Coordinating Council.
KEY FINDINGS
- Nothing suggests that a cyber attack executed through the Internet could cause a nuclear reactor to malfunction and breach containment.
- Nuclear power reactors have comprehensive safeguards that protect control system safety and security and prevent the misuse of portable media (e.g., Universal Serial Bus [USB] devices) and portable equipment (e.g., maintenance laptops) from circumventing these protections.
- The layered defense protecting critical digital assets in nuclear power plants are designed to prevent the possibility of anyone without unescorted access from initiating a cybersecurity incident affecting these systems. If preexisting undetected vulnerabilities or compromises in the digital equipment or software create a problem, alternative means are available for accomplishing safety and security functions.
- U.S. nuclear power reactor safety systems must have at least two independent systems to (1) keep the reactor coolant pressure boundary intact, (2) shut down and maintain the plant in a safe shutdown condition, and (3) ensure no radioactive release occurs in excess of federal limits.
- Multiple ways exist to read critical plant operational parameters. All operators are trained to rely on more than one indicator to make decisions in operating a plant. Even if authorized and knowledgeable individuals attempted to do harm, they would have to compromise several systems to sabotage the plant.
- If a single nuclear power reactor goes offline, the electric grid could manage the loss of supply in most circumstances. Under peak loads, the worst cascading effect might be rolling blackouts until the supply and demand balance.
POTENTIAL CONSEQUENCES OF CYBERSECURITY INCIDENTS
The protections achieved through compliance with regulations are expected to preclude any consequence from cybersecurity incidents in the Nuclear Reactors, Materials, and Waste Sector. If a cybersecurity incident should occur, the direct system and functional effects of such an incident would vary depending on the affected systems. In all cases, these incidents are expected to be recognized and addressed by back-up and mitigation procedures designed for safety and security. These back-up procedures aim for general safe operation of the plant, but serve as an additional layer of defense against harmful outcomes. If accidental introduction of malware occurs through improper procedures by well-intended personnel or through the use of compromised hardware or software, standard procedures can intervene to manage operational system failures and physical challenges, if the need arises.
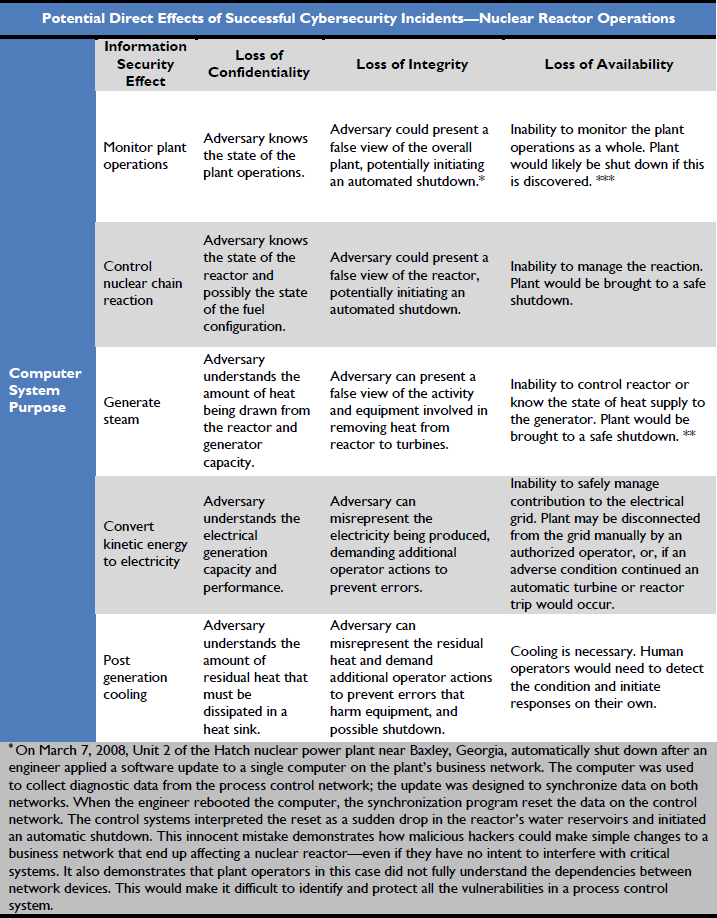
In Tables 1 through 5, OCIA identified functions in the Nuclear Reactors, Materials, and Waste Sector that are commonly cyberdependent and provided examples of potential impacts of successful cybersecurity incidents affecting these systems. As a rule, the cyberdefense-in-depth precludes unauthorized access to systems if there is a possibility that manipulation of the system could be used for sabotage. Included below are records of observed incidents in which cyber attacks or information security problems appeared to affect infrastructure systems. The effect of these incidents on plant operations is explained, and in addition, descriptions of infrastructure impacts caused by events other than a cybersecurity incident are included to provide examples of infrastructure failure and outcomes comparable to what could have been caused by a successful cybersecurity incident. This is useful for understanding the many practical obstacles between an initiating problem in a nuclear power plant and a negative outcome that might affect the public.
Table 1 identifies computer systems that support access control. Licensees use layered defenses with technical sensors and security staff to monitor various spaces within their complex. In a computer-supported system, authorized access points use access-control systems to manage the validation of credentialed and approved personnel’s access to sensitive spaces. Compromise of the computer systems that support these activities may prevent authorized personnel from accessing these spaces or may assist an adversary in gaining surreptitious access. Most, probably all access control systems are considered critical digital assets and are precluded from Internet access. The licensee determines which access control systems are critical digital assets, so a comprehensive statement cannot be made.
Access control management takes place for computer networks as well. The configuration of the network security architecture (see Figure 2) protects these critical digital assets from access through the Internet. These systems are on the network levels where equipment and operations important to safety and security are managed. Cybersecurity incidents here could be caused only by individuals who have unescorted access or equipment compromised before being connected to the network.
The licensee determines what access control systems are critical digital assets. If they are critical digital assets, only authorized workers would have access to the systems where they reside. This is an important feature of the current risk management.
…