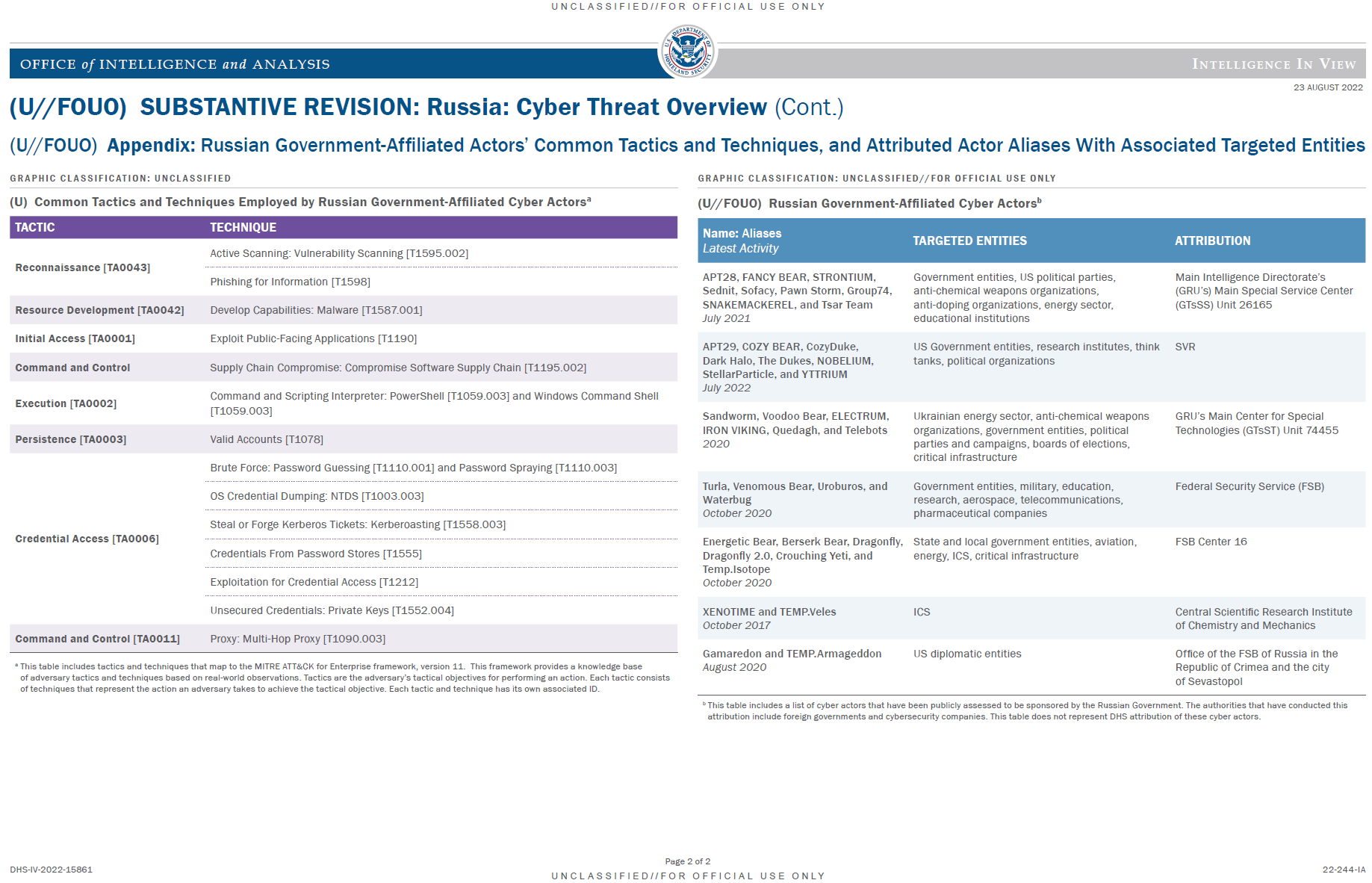
(U//FOUO) This Intelligence In View provides federal, state, local, and private sector stakeholders an overview of Russian Government-affiliated cyber activity targeting the United States and Russian regional adversaries, including disruptive or destructive cyber activity, cyber espionage in support of intelligence collection, and malign foreign influence in service of Russian political agendas. This In View also provides examples of malware and tools used by Russian Government-affiliated cyber actors.
(U) CYBER THREAT TO THE HOMELAND
(U) Russia likely will remain a significant threat to US networks, data, and critical infrastructure as it refines and employs its sophisticated cyber espionage, influence, and attack capabilities, particularly in response to international pressure following its unprovoked attack on Ukraine. Russia has previously targeted critical infrastructure in the United States and allied countries to improve—and in some cases demonstrate—its ability to inflict damage during a crisis. Russia’s use of destructive malware against Ukrainian infrastructure highlights the potential for such attacks to unintentionally spill over to other countries and threatens the availability of US critical assets and data. Russia will likely use these tools to compromise infrastructure and networks, acquire intellectual property and other proprietary data, undercut public trust in US institutions, and sow discord in the Homeland.
(U) TARGETING AND ATTACKS
(U) The Russian Government almost certainly considers cyber attacks an acceptable option to deter adversaries and control escalation. We have not yet observed Russian Government-affiliated actors conducting a destructive or disruptive cyber attack against the United States. However, Russian Government-affiliated cyber actors have targeted US industrial control system (ICS) and operational technology networks with malware, which, if successful, would provide the Russian Government with the option to conduct disruptive or destructive cyber attacks against US ICS. Russian Government-affiliated cyber actors have targeted a number of US industries and use a range of techniques to gain initial access to target networks. These actors have also demonstrated the ability to maintain persistent, undetected, long-term access in compromised environments—including cloud environments—by using legitimate credentials. This access can enable cyber disruptions that could be used at a foreign policy level to shape other countries’ decisions, as well as a deterrence and military tool.
(U) ESPIONAGE
(U//FOUO) Russian Government-affiliated cyber espionage is a persistent threat to federal, state, and local governments, as well as entities in the energy, aviation, transportation, healthcare, and telecommunications industries. Russian Government-affiliated cyber espionage actors support the Kremlin’s intelligence requirements, build cyber attack capabilities, and provide Moscow with an asymmetric response to perceived transgressions by the West.
(U) INFLUENCE
(U) Russian Government-affiliated malign influence actors operate a network of state media outlets and covert online journals to amplify topics Russia perceives as divisive in the United States—such as vaccines, refugees and migrants, and mass shootings—likely to weaken US sociopolitical cohesion and undercut confidence in Western liberal democratic institutions. Moscow has used hack-and-leak operations to influence US elections—such as the leaking of 20,000 internal Democratic National CommitteeUSPER e-mails during the 2016 presidential election—and to highlight perceived injustices—as with the targeting of the US Anti-Doping AgencyUSPER—resulting in the release of medical records of US athletes in retaliation for the banning of Russian athletes from the 2016 Summer Olympic Games. Moscow will continue to seek new methods of circumventing US social media companies’ anti-disinformation activities to further expand its narratives globally.
…