A biometric is a measurable physical characteristic or personal behavior trait used to recognize the identity or verify the claimed identity of an individual. Fingerprints are an example of a physical biometric characteristic. Behavioral biometric characteristics like handwriting are learned and acquired over time.
Biometrics is the process of recognizing an individual based on measurable anatomical, physiological and behavioral characteristics. Employing biometrics can help positively identify adversaries, allies and neutral persons. This is particularly useful when facing adversaries who rely on anonymity to operate.
Biometrics is not forensics even though the two can, and often are, employed in concert. Forensics involves the use of scientific analysis to link people, places, things and events while biometrics involves the use of automated processes to identify people based on their personal traits. Because of the interrelationship between biometrics and forensics, the Department of Defense (DOD) intends to develop a single concept of operation (CONOP) in the future describing how biometrics and forensics can be employed in a complementary manner.
This CONOP describes how DOD employs biometrics across the full range of military operations. It applies to all DOD organizations. This CONOP does not address the use of biometrics in DOD business functions not related to military operations.
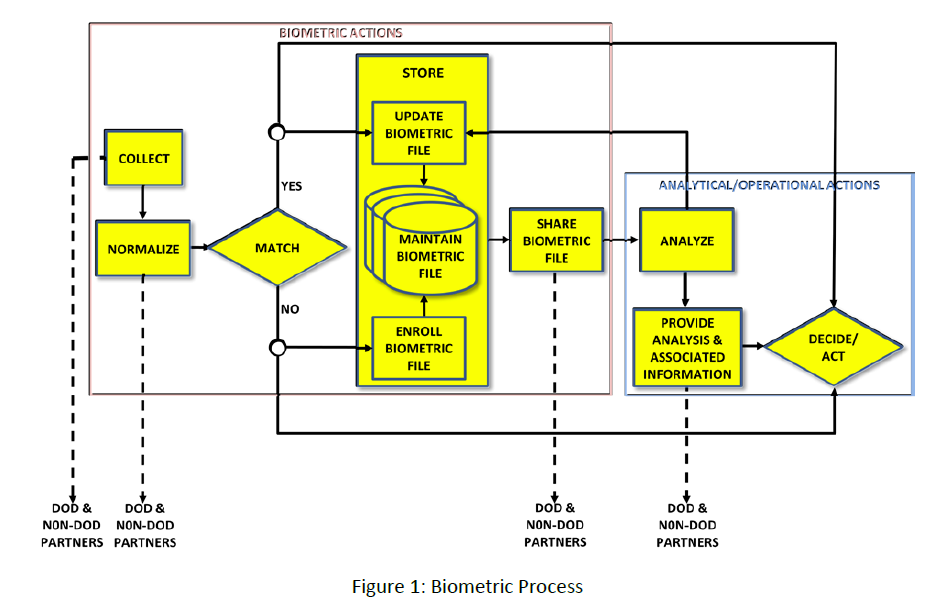
The DOD biometric process relies on five biometric actions and three analytical/operational actions:
1) Collect: Obtain biometric and related contextual data from an object, system, or individual with, or without, his knowledge.
2) Normalize: Create a standardized, high-quality biometric file consisting of a biometric sample and contextual data.
3) Match: Determine whether biometric samples come from the same human source based on their level of similarity.
4) Store: Maintain biometric files to make available standardized, current biometric information of individuals when and where required. Biometric files are initially enrolled and then subsequently updated as part of storing.
5) Share: Exchange standardized biometric files and match results among approved DOD, interagency and international partners in accordance with applicable laws, policies, authorities and agreements.
6) Analyze: To deliberately consider biometric and non-biometric information on an individual and reach logical conclusions. These conclusions can include his intent, affiliation(s), activities, location and behavioral patterns.
7) Provide: Exchange analysis and associated information on individuals among approved DOD, interagency and international partners in accordance with applicable laws, policies, authorities and agreements.
8) Decide/Act: Take action based on a biometric file’s match results and analysis of associated information.
By logically sequencing the biometric actions into the biometric process (Figure 1), the DOD can positively identify people and take appropriate action. This CONOP provides vignettes to illustrate this.
…
A.9 TRACK A HIGH-VALUE TARGET
While on patrol, a squad of Marines detects an improvised explosive device (IED). Explosive ordnance disposal technicians render the device safe, a forensics team manages to collect latent fingerprints and DNA samples, and the IED components are sent to a forward forensic facility for more analysis.
The latent fingerprints are formatted into a standardized electronic file, compared to samples on file and stored locally. There is no match at the local-trusted source and the data is enrolled into a biometric file. Both the electronic fingerprint file and DNA samples are transmitted to their respective authoritative source for further comparison. Acknowledgement of receipt is transmitted back to the local source. Matching at the authoritative source does not yield a DNA match and the sample is stored for further comparison. The fingerprint and DNA samples are also shared with coalition partners, revealing a fingerprint match to a suspected bomb-maker. Based on this identification, the coalition partner provides a facial photograph of the suspected bomb maker as well as other information gained from intercepted signals and captured documents.
Analysis of the shared biometric samples, signals and documents indicates the suspected bomb maker’s last reported location was outside the joint area of operations in a country providing sanctuary. This analysis, as well as the photograph provided by multinational partners, is sent to the DOD authoritative source to update the biometric file. An alert (prompt) containing pointers to information located in non-biometric reference data is disseminated to tactical users to facilitate future data comparisons on their local biometrics systems should they encounter the individual.
A series of raids on suspected insurgent locations provides more biometric samples that are matched to the suspected bomb maker. This match information, the biometric files and the associated information from the previous analysis that led to his being tied to the IED incidents are shared with interested parties for further analysis. Analysis of associated information indicates that the suspected bomb maker is moving within the area of responsibility and provides locations he will likely move to. Cameras are positioned around those locations and provide photographs that identify the suspected bomb maker using facial recognition. Once the suspected bomb maker is located, a tactical unit conducts a raid to apprehend him.
The raid force encounters six men at the site, all with authentic-looking identification in their possession. Pictures of the bomb-maker provided to the raid force are outdated and do not closely resemble any individual at the raid site but a field biometric test matches the suspected bomb-maker. Analysis of that biometric match result and associated information from the previous analysis that tied him to the IED incident enable the raid force leader to decide to detain that man. The other men are released after collecting their biometric samples and comparing them against available repositories to determine if they had been encountered previously. All collected samples and contextual information are updated in their respective biometric files and annotated to reflect that the raid force encountered them in the company of a known bomb-maker. Other information found at the scene is also collected by the raid force and subsequently stored in a repository of associated information for use in later analysis.
Tasks achieved using biometrics:
• Identify an unknown individual during tactical operations
• Locate a person of interest
• Track a person of interest
• Enable information assurance
• Share Identity Information