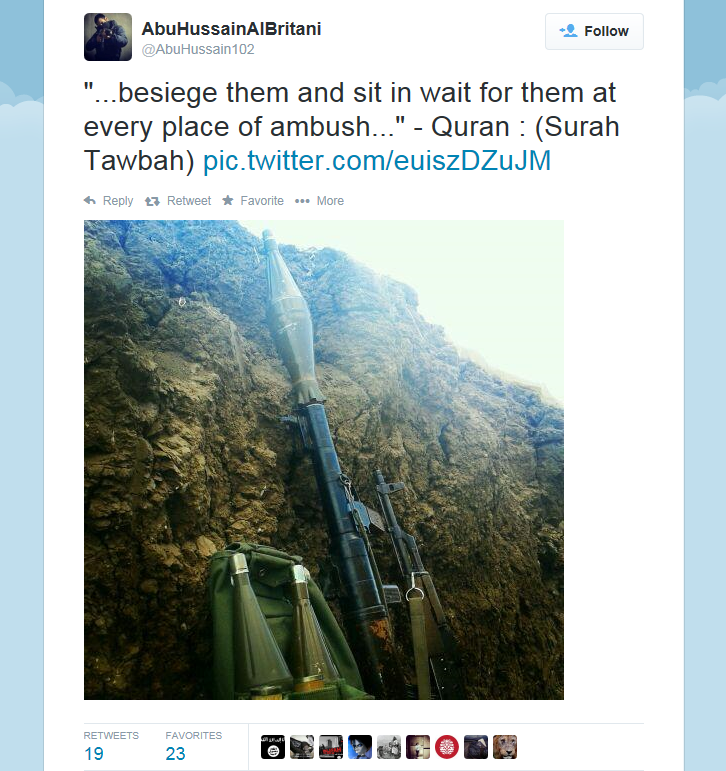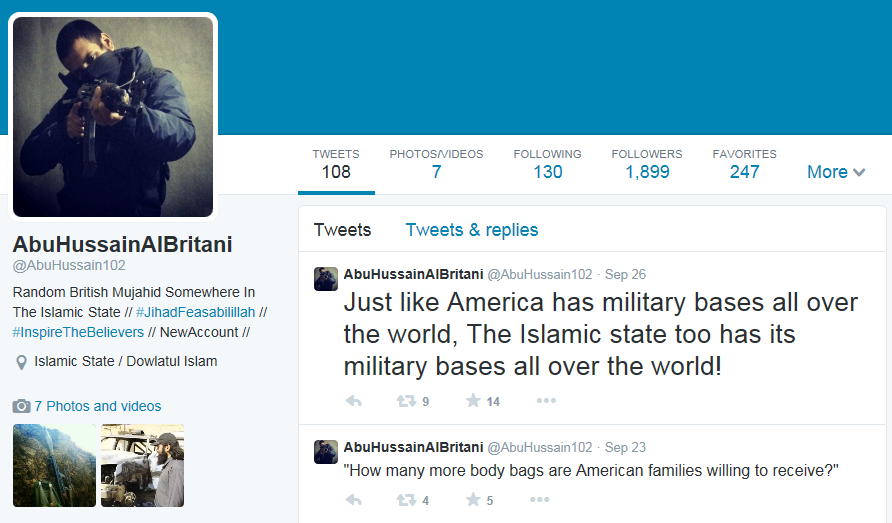
A Twitter account purporting to be operated by Junaid Hussain, also known as Abu Hussain Al Britani, who was sentenced to six months in prison in 2012 for hacking an email account associated with former Prime Minister Tony Blair and flooding the U.K. national anti-terror hotline with automated calls.
The FBI Cyber Division has issued a notification to private industry and law enforcement to be aware of the potential for retaliatory cyber attacks following recent U.S. military actions in the Middle East. While the FBI has “no information at this time to indicate specific cyber threats to US networks or infrastructure in response to ongoing US military air strikes against the terrorist group known as the Islamic State of Iraq and the Levant (ISIL)” the bulletin states that the FBI believes that “extremist hackers and hacktivist groups, including but not limited to those aligned with the ISIL ideology, will continue to threaten and may attempt offensive cyber actions against the United States in response to perceived or actual US military operations in Iraq or Syria.”
The bulletin titled “Threat of Cyberterrorist and Hacktivist Activity in Response to US Military Actions in the Middle East” was released last Wednesday and is based on “recent, nonspecific, and probably aspirational threats made on social media platforms to carry out cyber as well as physical attacks in response to the US military presence in the Middle East.” The bulletin, which was obtained by Public Intelligence, states that “Middle East-based hacktivist groups and extremist cyber actors have previously targeted US commercial and government Web sites in response to a range of US military actions and foreign policy positions” using tactics such as “Cross Site Scripting (XSS), Structured Query Language (SQL) Injection, and TCP/UDP Flooding for defacement and DDoS attacks.” According to the FBI, web site defacements “conducted by these actors will likely contain messages expressing support for ISIL, and/or contain imagery such as the black ISIL flag or graphic imagery, e.g., pictures or videos of ISIL executions.”
Previous examples of hacktivist attacks motivated by U.S. military actions are included in the bulletin including an incident in May 2014 in which the “Tunisian Hackers Team threatened Distributed Denial of Service (DDoS) attacks against the US financial sector unless US military forces were withdrawn from presumed-Islamic lands.” The bulletin also cites numerous threatening posts on Twitter and identifies several accounts that have expressed support for ISIL, some of which have even provided guidance on tools that could potentially be used in a cyber attack. One particularly interesting example cited in the bulletin is the case of Junaid Hussain, a British man who pleaded guilty in 2012 to charges related to the hacking of an email account connected with former Prime Minister Tony Blair. Hussain, who was just sixteen at the time the hacking occurred, was involved in the compromise of a Gmail account used by Blair’s adviser Katie Kay and later posted private contact information obtained from the account. As part of the hacking group TeaMp0isoN, Hussain also participated in an attack that flooded the the U.K.’s national anti-terror hotline with automated calls, including some prank calls that are still available on YouTube. After serving six months in a youth detention facility, Hussain was arrested on suspicion of “violent disorder” in late 2013 and while on bail fled to Syria with a 24-year-old rapper named Abdel-Majed Abdel Bary. He is now reportedly fighting with ISIL and goes by the name Abu Hussain Al Britani. A Twitter account reportedly operated by Hussain features a profile photo depicting him pointing an AK-47 at the camera and a bio that reads “random British mujahid somewhere in the Islamic State.”
Several recent law enforcement bulletins issued by the Department of Homeland Security and local fusion centers have warned about online threats made by supporters of ISIL. A joint DHS-FBI intelligence bulletin from August 22, 2014 obtained by Fox News warned that following the “start of US military air strikes on 8 August against the ISIL in Iraq, ISIL supporters launched a Twitter campaign threatening retaliatory violence against the Homeland and US interests overseas.” The bulletin went on to say that social media is increasingly being used by ISIL supporters to encourage violent attacks on U.S. interests. Another fusion center bulletin from early July, also obtained by Fox News, cited specific tweets threatening the lives of U.S. military personnel. One tweet from a British jihadist cited in the bulletin reportedly instructed supporters to use LinkedIn and Facebook to look up information on U.S. service members prior to staging attacks: “You could literally search for soldiers, find their town, photos of them, look for address in Yellowbook or something. Then show up and slaughter them.”
While no specific plots have been identified, online threats against U.S. service members are evidently credible enough to warrant a response from the U.S. Army. The Army Threat Integration Center (ARTIC) issued a special assessment on Thursday warning soldiers about the threat posed by the “Islamic State of Iraq and the Levant (ISIL), its supporters, those swayed by radical Islam, and lone offenders with the intent or inclination to act on ISIL’s behalf.” Given the “continued rhetoric being issued by ISIL’s media services and supporters through various social media platforms,” the assessment states that ARTIC is concerned of the possibility of attacks conducted against U.S. military personnel and their families:
Over the past year, ISIL has threatened violence against the United States and US interests overseas in response to ongoing counterterrorism pressure. Following the start of US air strikes in Iraq in early August 2014, and then Syria in late September 2014, ISIL supporters launched a Twitter campaign threatening retaliatory violence against the United States. Additionally, a recent audio message from an ISIL spokesman called, for the first time, for lone offender attacks in the Homeland in retaliation for US military operations in Iraq and Syria.
The assessment includes tips on basic home security precautions that service members should take to protect against an individual “conducting an attack while you or your family members are home.” These tips include using the “peephole before opening the door to anyone” and not opening the door to “solicitors or strangers.”