Army Field Manual Interim 2-22.9
- 161 pages
- For Official Use Only
- December 5, 2006
Chapter 2
Fundamentals2-1. OSINT operations are integral to Army intelligence operations. Directly or indirectly, publicly available information forms the basis of all intelligence operations and intelligence products. The availability, depth, and range of publicly available information enable intelligence organizations to satisfy many intelligence requirements without the use of specialized human or technical means of collection. OSINT operations support other intelligence, surveillance, and reconnaissance (ISR) efforts by providing foundational information that enhances collection and production. As part of a multidiscipline intelligence effort, the use and integration of OSINT ensures decisionmakers have the benefit of all available information.
DEFINITION
2-2. The National Defense Authorization Act for Fiscal Year 2006 states, “Open source intelligence is produced from publicly available information that is collected, exploited, and disseminated in a timely manner to an appropriate audience for the purpose of addressing a specific intelligence requirement.” Expressed in terms of the Army intelligence process, OSINT is relevant information derived from the systematic collection, processing, and analysis of publicly available information in response to intelligence requirements. Two important terms in these complementary definitions are––
- Open Source, which is any person or group that provides information without the expectation of privacy––the information, the relationship, or both is not protected against public disclosure.
- Publicly Available Information, which is data, facts, instructions, or other material published or broadcast for general public consumption; available on request to a member of the general public; lawfully seen or heard by any casual observer; or made available at a meeting open to the general public.
OPEN SOURCE INTELLIGENCE DISCIPLINE
2-3. The source, the information, and the collection means rather than a specific category of technical or human resources distinguish OSINT from other intelligence disciplines (see Figure 2-1). Open sources broadcast, publish, or otherwise distribute unclassified information for public use. The collection means (techniques) for gathering publicly available information from these media of communications are unintrusive. Other intelligence disciplines use confidential sources or intrusive techniques to collect
private information. Confidential sources and private information are––
- Confidential Source, which is any person, group, or system that provides information with the expectation that the information, relationship, or both, are protected against public disclosure.
- Private Information, which is data, facts, instructions, or other material intended for or restricted to a particular person, group, or organization. There are two subcategories of private information: classified information and controlled unclassified information.
- Classified information requires protection against unauthorized disclosure and is marked to indicate its classified status when in documentary or readable form.
- Controlled unclassified information requires the application of controls and protective measures, for a variety of reasons (that is, sensitive but unclassified, or for official use only), not to include those that qualify for formal classification.
…
F-6. Intelink-SBU is responsible for providing virtual private network desktop client configuration management, application support, and product updates. This system displays the DOD Warning Banner as a part of the logon process. Access to the Intelink-SBU virtual private network from any system will be restricted to authorized users. No temporary, seasonal, or liaison personnel shall be authorized to use an Intelink-SBU virtual private network client installed on an Army information system. Personnel using a NIPRNET LAN connected and supported Intelink-SBU systems will possess access credentials equivalent to their position and authorizations for use of those NIPRNET systems. This requirement is waiverable only when access to Intelink-SBU is from a standalone (dedicated) system used for Intelink-SBU connectivity only, and the individual is authorized an Intelink-SBU account. Many Intelink-SBU users who do not possess or hold an appropriate clearance are often assigned open source tasks on the Intelink SBU network as the best operational use of these personnel and as a training vehicle available to those personnel pending their clearance approvals.
OPEN SOURCES AND INFORMATION
2-5. Open sources and publicly available information may include but are not limited to––
- Academia. Courseware, dissertations, lectures, presentations, research papers, and studies in both hardcopy and softcopy on economics, geography (physical, cultural, and political-military), international relations, regional security, science, and technology.
- Governmental, Intergovernmental, and Nongovernmental Organizations (NGOs). Databases, posted information, and printed reports on a wide variety of economic, environmental, geographic, humanitarian, security, science, and technology issues.
- Commercial and Public Information Services. Broadcasted, posted, and printed news on current international, regional, and local topics.
- Libraries and Research Centers. Printed documents and digital databases on a range of topics as well as knowledge and skills in information retrieval.
- Individuals and Groups. Handwritten, painted, posted, printed, and broadcasted information (for example, art, graffiti, leaflets, posters, and websites).
…
INTELLECTUAL PROPERTY
2-27. AR 27-60 prescribes policy and procedures for the acquisition, protection, transfer and use of patents, copyrights, trademarks, and other intellectual property by the Department of the Army (DA). It is Army policy to recognize the rights of copyright owners consistent with the Army’s unique mission and worldwide commitments. As a general rule, Army organizations will not reproduce or distributed copyrighted works without the permission of the copyright owner unless such use is within an exception under US Copyright Law or required to meet an immediate, mission-essential need for which noninfringing
alternatives are either unavailable or unsatisfactory.2-28. According to the US Copyright Office, “fair use” of a copyrighted work for purposes such as criticism, comment, news reporting, teaching, scholarship, or research, is not an infringement of copyright. Implicit with fair use is the documentation and citation of the source of the copyrighted information. The following are four factors in determining fair use:
- Purpose and character of the use. In the context of fair use, intelligence operations are similar in purpose and usage to non-profit news reporting and research organizations.
- Nature of the copyrighted work (see Appendix D).
- Amount and substantiality of the portion used in relation to the copyrighted work as a whole. There is no specific number of words, lines, or notes that may safely be taken without permission. Usually, the amount or portion of copyrighted material is limited to quotations of excerpts and short passages; and summary of a speech or article, with brief quotations.
- Effect of the use upon the potential market for or value of the copyrighted work. The effect on the market or value of copyrighted material relates to reproduction and dissemination of products provided by the owner beyond that authorized the owner’s “Terms of Use” or described in contracts and licenses with the US Government.
…
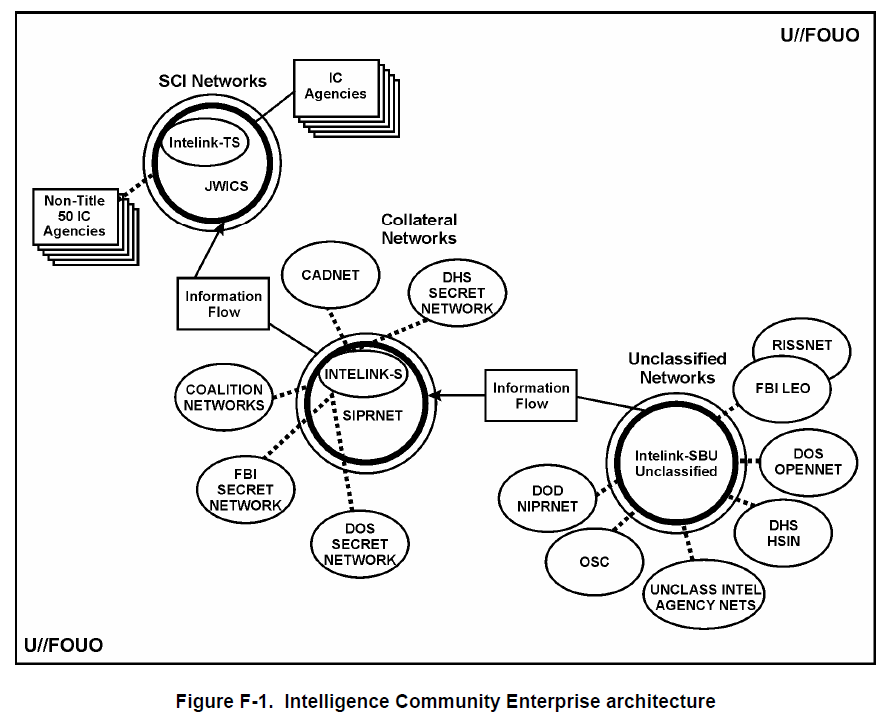
F-2. Intelink-SBU is a private electronic network that provides the information technology infrastructure enabling protected intranet research for the sharing of sensitive and unclassified information within the Intelligence Community components, its customers, and affiliates. It was developed at Director of Central Intelligence direction under authority contained within the National Security Act of 1947 (as amended) and Executive Order 12333 to support the National Intelligence effort through full and free exchange of information across all agencies and departments of the Federal Government.
F-3. Additionally, Intelink-SBU provides protected and monitored access to the public Internet in order to provide Intelink-SBU users a single point of access to unclassified intelligence information. It provides a central point of access for Regular Army, Army Reserve, and Army National Guard units around the World to share common mission tools and practices. Intelink-SBU provides the one venue that the Army contributes resources to support. Intelink-SBU provides unique OPSEC tools and techniques that, if not available on one network, would cost the DOD and the Army millions of dollars to replicate.
F-4. This Intelink-SBU system is not directly connected to the public Internet. Access to Intelink-SBU services is implemented through multiple virtual private networks. Users gain access to the public Internet through Intelink-SBU provided proxy-based firewalls. The Intelink-SBU boundary devices include firewalls and the virtual private network tunnel boxes, including the desktop-tunnel endpoint devices.
F-5. Intelink-SBU users can view current and historical open source content, shared by Intelink-SBU participants or purchased by a participant from a commercial vendor. This is more of a rear-only view into Intelink-SBU. Participants appear as an Intelink-SBU network (intelink.gov) on the Internet, instead of using their organization’s network name, such as a “.mil” site. Participation in the Intelink-SBU network is via a standalone (dedicated) host or network connected host.
- Standalone (Dedicated) Host. The use of a standalone, dedicated laptop or desktop platform is the preferred option to support the Intelink-SBU environment within an Army organization with the least amount of residual operational risk to the supporting network. The installation firewall will deny all traffic to the Intelink-SBU client and permit by exception only the destination Intelink-SBU IP address inbound or outbound to the Intelink-SBU client. The system will only be used for the Intelink-SBU virtual private network connection. Use of the open Internet for web-surfing, connection to local or web email, or other unapproved applications will not be installed or authorized.
- Network Connected Host. Users are required to access the local host through existing authentication methods, traditionally through input of a user name and password, before they can access the local system; and then shall use a separate user name and password to access the Intelink-SBU account. The local host identified for Intelink-SBU connectivity will have a statically assigned IP address for the desktops to attribute security auditing and reviews. User activity on the Intelink-SBU server is seen as an intranet user on the Intelink-SBU network, and all user activity is logged and accountable to that user. When using desktop virtual private network software, all existing local network devices (for example, printers, network file servers, local email services) become unavailable.