With utilities in the U.S. and around the world increasingly moving toward smart grid technology and other upgrades with inherent cyber vulnerabilities, correlative threats from malicious cyber attacks on the North American electric grid continue to grow in frequency and sophistication. The potential for malicious actors to access and adversely affect physical electricity assets of U.S. electricity generation, transmission, or distribution systems via cyber means is a primary concern for utilities contributing to the bulk electric system. This paper seeks to illustrate the current cyber-physical landscape of the U.S. electric sector in the context of its vulnerabilities to cyber attacks, the likelihood of cyber attacks, and the impacts cyber events and threat actors can achieve on the power grid. In addition, this paper highlights utility perspectives, perceived challenges, and requests for assistance in addressing cyber threats to the electric sector.
There have been no reported targeted cyber attacks carried out against utilities in the U.S. that have resulted in permanent or long term damage to power system operations thus far, yet electric utilities throughout the U.S. have seen a steady rise in cyber and physical security related events that continue to raise concern. Asset owners and operators understand that the effects of a coordinated cyber and physical attack on a utility’s operations would threaten electric system reliability–and potentially result in large scale power outages. Utilities are routinely faced with new challenges for dealing with these cyber threats to the grid and consequently maintain a set of best practices to keep systems secure and up to date.
Among the greatest challenges is a lack of knowledge or strategy to mitigate new risks that emerge as a result of an exponential rise in complexity of modern control systems. This paper compiles an open-source analysis of cyber threats and risks to the electric grid, utility best practices for prevention and response to cyber threats, and utility suggestions about how the federal government can aid utilities in combating and mitigating risks.
Among the findings of this paper, several key elements are:
- Growth of networks and communication protocols used throughout ICS networks pose vulnerabilities that will continue to provide attack vectors that threat actors will seek to exploit for the foreseeable future. The interoperable technologies created for a shift toward a smart grid will continue to expand the cyber attack landscape.
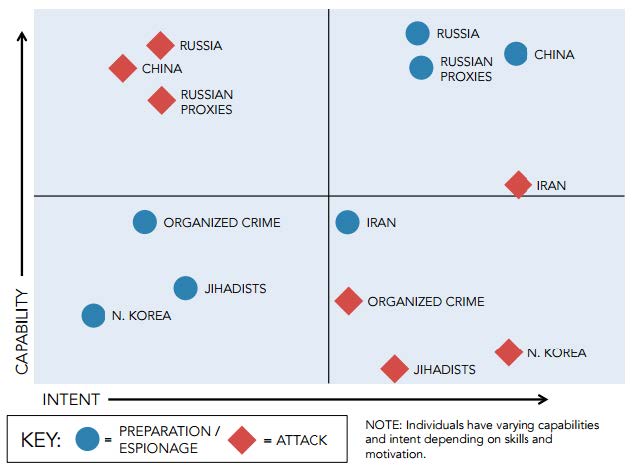
- Threat actors on multiple fronts continue to seek to exploit cyber vulnerabilities in the U.S. electrical grid. Nation-states like Russia, China, and Iran and non-state actors, including foreign terrorist and hacktivist groups, pose varying threats to the power grid. A determined, well-funded, capable threat actor with the appropriate attack vector can succeed to varying levels depending on what defenses are in place.
- Utilities often lack full scope perspective of their cyber security posture. Total awareness of all vulnerabilities and threats at all times is improbable, but without enough cyber security staff and/or resources utilities often lack the capabilities to identify cyber assets and fully comprehend system and network architectures necessary for conducting cyber security assessments, monitoring, and upgrades.
- Some utilities require financial assistance in creating or shaping their cyber strategy, both to meet regulatory standards and for business security. While regulatory requirements for the bulk electric system are clear about what compliance outcomes utilities should achieve, utilities desire guidance about how to best achieve cyber security outcomes, as well as how to develop active defenses capable of addressing a highly targeted cyber attack.
- The assortment of regulatory standards and guidelines applicable to utilities regarding cyber security practices produces varied methods of adoption. This causes some overlap and confusion in jurisdictional applicability (federal vs. state) and has produced a wide range of differing practices by utilities in meeting standards, making an evaluation of industry-wide best practices difficult.
- Utilities expect more qualitative, timely threat intelligence from existing federal information sharing programs. Utilities also seek clarity about the conditions of information sharing programs based on new national cyber security policy (CISA 2015).
…
1.2. Reported Cyber Attacks Involving U.S. Utilities
It is likely that many more cyber incidents occur than are reported. Known attacks against the energy sector often follow a phased pattern that focuses on discovery, capture, and exfiltration of data, which generally does not produce tangible or immediately detectable consequences. However, if an attacker’s goal is to “degrade, disrupt, deny, [or] destroy” utility operations, prior reconnaissance and established access provide launch points for destructive payloads (malware). No lasting damage–physical, cyber-physical, or otherwise–to U.S. utilities as a result of a cyber attack has yet been reported publicly, but known cyber attacks and campaigns targeting U.S. electric utilities have been highly publicized.
In early 2014, ICS-CERT released information about an unnamed public utility that was compromised via remote access. Not only was the control system configured for remote access, “the software used to administer the control system assets was accessible via Internet facing hosts.” Intrusion activity prior and related to this threat was also discovered. Researchers also found that though the remote access point was password-protected, the password was weak. Brute forcing techniques, or ‘trial-and-error until solved’ attempts to discover the password were found to be a threat to the access point. No long term costs or damage have been attributed to this attack, but an onsite cyber security assessment conducted by ICS-CERT as a result of the event likely resulted in recommendations for the utility’s future control system administration.
Conversely, the Havex campaign uses spam email to distribute a remote access Trojan (RAT) tool to targets and in the past used watering hole attacks deployed from compromised ICS/supervisory control and data acquisition (SCADA) vendor websites. Since around 2013 a group known as ‘Dragonfly’ and ‘Energetic Bear’, thought to be a state-sponsored organization is responsible for Havex and targets energy sector companies (and other sectors) in the U.S. among other countries. By targeting electric grid operators, equipment vendors, and relevant software providers, the attackers were able to spread malware that “instruct infected machines to download and execute additional components.” Though no reports have yet emerged confirming exploit or damage of Havex in infected systems, the malware’s complexity and range of access thus far could produce future effects if not properly mitigated.
Another incident to which ICS-CERT responded was found to have been ongoing since 2011 but with no detectable “attempts to damage, modify, or otherwise disrupt the victim systems’ control processes.” The threat, known as BlackEnergy, is a Trojan-based hacking campaign that exploits human-machine interface (HMI) software often used by utilities in grid control among other systems. While General Electric (GE), manufacturer of an HMI believed to be the target of the BlackEnergy campaign released a patch for its HMI software in response to the incident, future vulnerability based on this attack vector depends in part on awareness, detection and defense in depth.iii The BlackEnergy malware is described as “highly modular” with functionality varying in deployment to different victims, making it difficult to determine its future impact in the electricity industry. ICS-CERT published a Traffic Light Protocol (TLP) Amber-designated version of this information, a limited-release sharing mechanism by which companies affected by and/or requiring the information to mitigate a related cyber threat can receive and share the information internally on a need-to-know basis.
A now-dated but well documented attack on a California independent system operator (ISO) responsible for electricity distribution across the state which occurred in 2001 highlights a lack of cyber security consideration in planned system maintenance. Taking advantage of poor security configuration, attackers compromised two web servers under development to access the ISO’s network. The attack was halted before attackers were able to access grid-connected systems, but took nearly three weeks to detect and was eventually assessed to be of Chinese origin. The servers that exposed the utility’s network were not firewalled and appear to have been an overlooked threat, the result of a time-sensitive business operations priority.
…