ISAF Security Force Assistance Guide
- 196 pages
- May 5, 2013
- 14 MB
This guide is designed to provide NATO partners and troop contributing nations (TCNs) participating as part of the International Security Assistance Forces (ISAF) a common understanding of Security Force Assistance (SFA) activities. It provides a summary of the ISAF SFA concept as well as guidance and information concerning SFA activities, countering the insider threat, mission critical tasks, and training requirements in support of Afghan National Security Forces (ANSF).
The current strategic environment is seen as one of persistent conflict in which Coalition strategic objectives require unified action to achieve unity of effort. These synchronization, coordination, and integration activities of both governmental and non-governmental organizations with military operations also require close relationships with Coalition partners, key friends and allies. Keys to achieving unity of effort are strengthening interagency coordination, working with international allies and partners, and synchronizing strategic communications by NATO and its partners.
In concept, military forces conduct SFA to facilitate a host nation’s (HN) ability to deter and defend against transnational and internal threats to stability. Respective Ministries of Defense also conduct SFA to: assist in a HN’s ability to defend against external threats; contribute to Coalition operations; or organize, train, equip, and advise another country’s security forces or supporting institutions.
As it relates to Afghanistan successful SFA requires that TCN commanders thoroughly understand the operational environment. Conditions of the operational environment affect what SFA commanders provide. Commanders must understand the conditions that make up the current situation, including the Afghan population, other regional actors, and Coalition forces. From this understanding, commanders visualize desired conditions that represent a desired end state. Commanders must understand the capacity and capabilities of the ANSF. The Government of the Islamic Republic of Afghanistan (GIRoA) helps to determine desired conditions associated with the ANSF. After envisioning a desired end state, commanders then conceptualize how to change the current situation to the desired end state.
Acknowledging the gap in SFA doctrine, and cognizant of the fact that Supreme Allied Command Transformation has been tasked to lead the development of a NATO SFA Concept, this guide provides SFA direction and information, specific to the ISAF mission as it relates to the ANSF.
…
Insider Threat Prevention Model
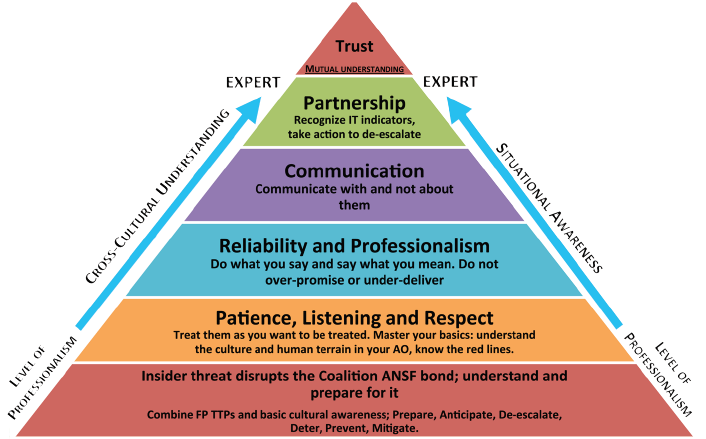
1.29 The insider threat prevention model (ITPM) is based on the combination of mastering force protection Tactics, Techniques, and Proceedures (TTPs) and the use of attribution, a concept in social psychology addressing the processes by which individuals explain the cause of behavior and events. This conceptual model consists of a set of five principles as depicted in Figure 1-2 and outlined in paragraphs below.
1.30 The Insider Threat Prevention Model consists of the following five principles:
a) IT disrupts the Coalition/ ANSF bond; understand and prepare for it. The first principle and foundation focuses on mastering the TTPs and the objective of understanding the Afghan culture necessary for countering the IT security problem.
b) Patience, Listening and Respect. This principle is key to IT prevention and is squarely based on common principles of human interaction centered on kindness, understanding and empathy.
c) Reliability and Professionalism. Reliability is a pre-cursor of trust and a leading indicator of professionalism.
d) Communication. Surveillance detection and information gained from interacting with Afghan partners will ultimately enhance IT prevention.
e) Partnership. The feeling of a partnership is the result of practicing the first four principles where partners see each other as fellow team members.
1.31 Insider Threat incidents can be caused by personal confrontations that involve cultural insensitivities. Instruction on conflict de-escalation and conflict resolution techniques should be a core part of pre-deployment training. Various cross-cultural conflict escalation scenarios should be utilized for role playing exercises. Effective integration of insider threat intelligence indicators into mission planning and execution reinforces ISAF force protection, limits casualties, and helps set conditions for future success. Similarly, security and small arms TTPs should be developed and routinely practiced for confronting an insider threat incident. Finally, conducting an assessment of the events that led up to the attack, what transpired during the attack and post-incident actions will provide vital lessons learned that can be utilized to restore relations, continue development, and regain combat effectiveness.