The following National Institute of Standards and Technology draft guide on cyber threat information sharing was released October 28, 2014 for public comment.
Guide to Cyber Threat Information Sharing (Draft)
- 73 pages
- October 2014
This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A-80 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A-130, Appendix III, Security of Federal Automated Information Resources.
…
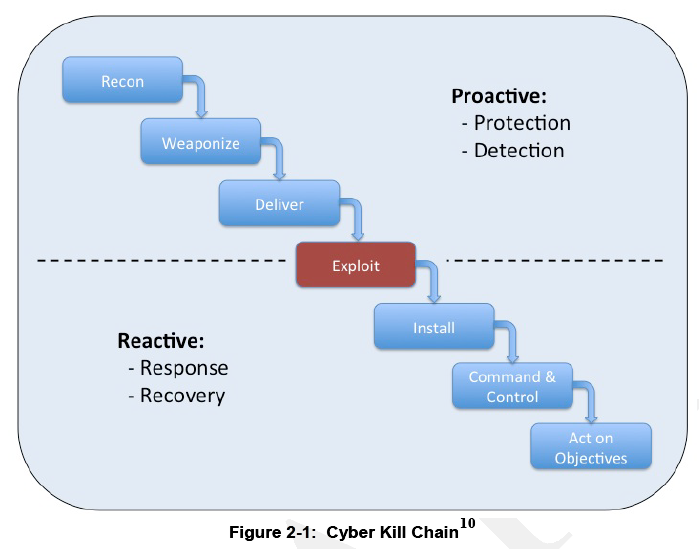
As the magnitude and complexity of cyberspace increases, so too does the threat1 landscape. Cyber attacks have increased in both frequency and sophistication resulting in significant challenges to organizations that must defend their infrastructure from attacks by capable adversaries. These adversaries range from individual attackers to well-resourced groups operating as part of a criminal enterprise or on behalf of a nation-state. These adversaries are persistent, motivated, and agile; and employ a variety of tactics, techniques, and procedures (TTPs) to compromise systems, disrupt services, commit financial fraud, expose sensitive information, and steal intellectual property. To enhance incident response actions and bolster cyber defenses, organizations must harness the collective wisdom of peer organizations through information sharing and coordinated incident response. This publication expands upon the guidance introduced in Section 4, Coordination and Information Sharing of NIST Special Publication (SP) 800-61, Computer Security Incident Handling Guide and explores information sharing, coordination, and collaboration as part of the incident response life cycle.
This publication assists organizations in establishing, participating in, and maintaining information sharing relationships throughout the incident response life cycle. The publication explores the benefits and challenges of coordination and sharing, presents the strengths and weaknesses of various information sharing architectures, clarifies the importance of trust, and introduces specific data handling considerations. The goal of the publication is to provide guidance that improves the efficiency and effectiveness of defensive cyber operations and incident response activities, by introducing safe and effective information sharing practices, examining the value of standard data formats and transport protocols to foster greater interoperability, and providing guidance on the planning, implementation, and maintenance of information sharing programs.
Implementing the following recommendations enables organizations to make more efficient and effective use of information sharing and collaboration capabilities throughout the incident response life cycle. Organizations should perform an inventory that catalogues the information an organization currently possesses, the information that it is capable of producing, and document the circumstances under which this information may be shared.
By conducting an information inventory, an organization gains a better understanding of where its critical information resides, who owns it, how must it be protected, and when it can be shared. When deciding what incident-related information to share with other organizations, the following factors should be considered:
• Risk of disclosure
• Operational urgency and need for sharing
• Benefits gained by sharing
• Sensitivity of the information
• Trustworthiness of the recipients
• Methods and ability to safeguard the information…