MULTI-SERVICE TACTICS, TECHNIQUES, AND PROCEDURES FOR THE JOINT APPLICATION OF FIREPOWER
- FM 3-09.32
- 148 pages
- Distribution authorized to the DOD, DOD contractors, Australia, Canada, Czech Republic, Denmark, France, Germany, Italy, Netherlands, Norway, Poland, Portugal, Spain, Sweden, and the United Kingdom only to protect technical or operational information from automatic dissemination under the International Exchange Program or by other means.
- December 2007
JFIRE is a pocket-size, quick-reference guide for requesting fire support in accordance with approved joint tactics, techniques, and procedures (TTP). JFIRE contains calls for fire, joint air attack team (JAAT) techniques, a format for joint air strike requests, close air support (CAS) coordination and planning procedures, communications architecture, and weapons data.
Scope
JFIRE applies to the tactical and special operating forces of the Army, Navy, Marine Corps, and Air Force. It is a United States (US) unilateral-only document, but includes some North Atlantic Treaty Organization (NATO) formats where appropriate. Information in JFIRE has been extracted from existing Service directives. It is primarily intended for use by members of battalion and squadronlevel combat units.
…
5. Unmanned Aircraft Systems Considerations
UASs consist of one or more unmanned aircraft (UA), a control station, datalinks, and payloads. The capability of UASs to support or execute CAS varies greatly between systems. For example, US Air Force (USAF) MQ-1 and MQ-9 are armed with air-to-surface weapons, have radio communications aboard the UA, and are flown by rated aviators trained in CAS procedures. Other systems may not be similarly equipped or flown by CAS-qualified crews but may be employed for situational awareness, target marking, or as an observer for Types 2 or 3 control by the controlling JTAC. (See appendices A and B for more information on UASs.) The following UAS CAS considerations are intended for use with CAS-capable UAS and CAS-qualified UAS operators only:
a. Threat: Unmanned aircraft are unlikely to survive in a heavily defended environment. Consideration must be given to enemy air-to-air and surface-to-air weapons with the ability to engage a UA at its operating location and altitude. UAs are not normally equipped with warning receivers or countermeasures and depend on threat avoidance for mission survivability. Datalinks may be susceptible to jamming or interference.
b. Weather: UAs are susceptible to turbulence, icing, and visible precipitation. Electro-optical (EO) / IR sensors and laser designators / range finders / target markers require unobstructed LOS to the target. Intervening haze, clouds, or blowing dust may interfere with or prevent mission accomplishment. On the other hand, synthetic aperture radar (SAR) and inertially aided munitions (IAMs) are unaffected by haze, cloud cover, or dust. High winds aloft may make it difficult for the UA to maintain station in a highly restricted location or may unacceptably delay transit between target areas.
c. Signature: UAs vary in visual, radar, IR, and acoustic signature and in system ability and crew proficiency to manage the signature. For example, when minimum noise is desired to avoid tipping off a target, it may be possible to modulate power and trade altitude for airspeed in order to reduce the noise signature while approaching closer to a target. On the other hand, it may be desirable to announce presence in order to stimulate a desired response or intimidate the target.
d. Deconfliction: While UASs presently lack the ability to see and avoid other aircraft, there are other means to integrate UASs (e.g., voice radio; tactical datalinks; identification, friend or foe [IFF]). Formal and informal airspace control measures apply to UASs. UAs may hold overhead or offset from a target. Relatively slow airspeeds can permit a UA to operate in a smaller segment of airspace than other aircraft. Depending upon performance capabilities of the specific UAS and communications with the crew, it may take several minutes to reposition the UA or change altitude blocks. JTACs must trade off the best position for the UASs to employ sensors / weapons against the desired target(s) with the ability to best employ other assets. Consideration should also be given to the “lost link” profile autonomously flown by UA if the control datalink is lost. Upon initial check-in, the JTAC should query the UAS operator for the currently programmed lost-link profile. If unacceptable due to airspace limitations or other reasons, the JTAC should direct a new lost-link profile and receive verification that the UA has been programmed.
e. Communication and Situational Awareness: Some UAs have onboard radios and / or secure voice providing the ability to communicate with the UAS pilot as with any manned aircraft. In addition, some UASs have secure chat and voice over Internet Protocol, as well as additional air and ground situational awareness displays. Providing the ground scheme of maneuver to the supporting UAS can significantly increase the crew’s situational awareness and subsequent mission support.
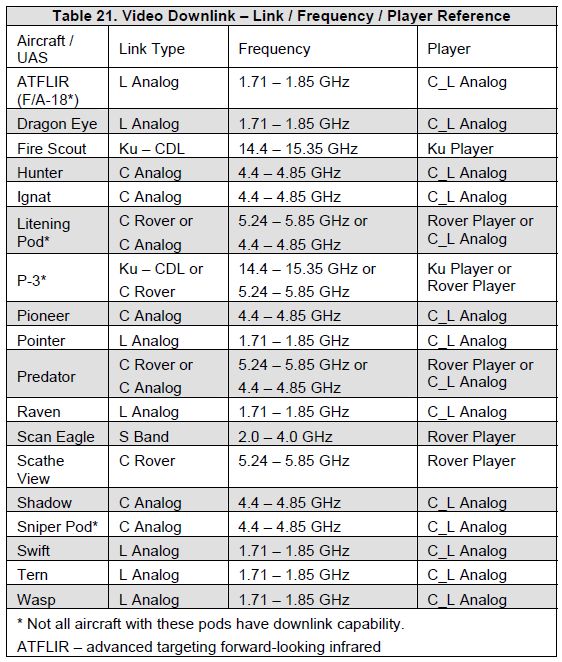
f. Video Downlink (VDL) and Machine-to-machine Datalinks: Some UASs can accept and provide machine-to-machine digital targeting information and many UASs provide LOS video downlinks to users with compatible video receivers. This can significantly reduce voice traffic and reduce information transfer errors. (See table 21 VDL – Link / Frequency / Player Reference on p.77 for more information.)
g. Tactics: UASs employ using a variety of tactics ranging from a wheel to a variant of an IP-target run-in. UA performance characteristics and sensor and weapons capabilities, along with the environmental and tactical situation, influence the selection of tactics, ranges, altitudes, and timing considerations.
…