The following guide has three parts:
Download ZIP archive with all three documents (6.5 MB)
 Asymmetric Warfare Group
Asymmetric Warfare Group
- ATTACK THE NETWORK PART 1: OIL SPOT METHODOLOGY
- 5 pages
- For Official Use Only
- March 2009
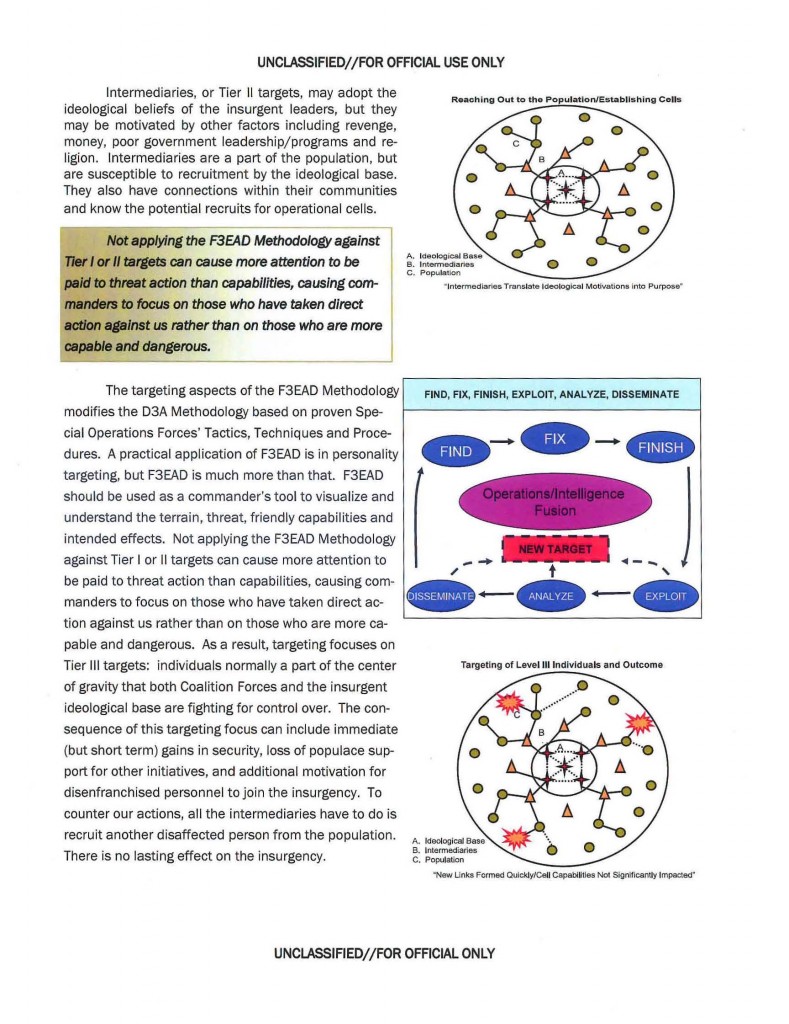
This document facilitates discussion, training and implementation of effective targeting methods at the Battalion and Brigade level. In this paper, the Oil Spot Strategy is discussed as a model for describing insurgent influence. This methodology can enable leaders to better understand the critical links within an insurgent cell and serve as a basis for understanding Attack the Network concepts.
…
 Asymmetric Warfare Group
Asymmetric Warfare Group
- ATTACK THE NETWORK METHODOLOGY: PART 2 CRITICAL VULNERABILITIES AND TARGETING
- 5 pages
- For Official Use Only
- March 2009
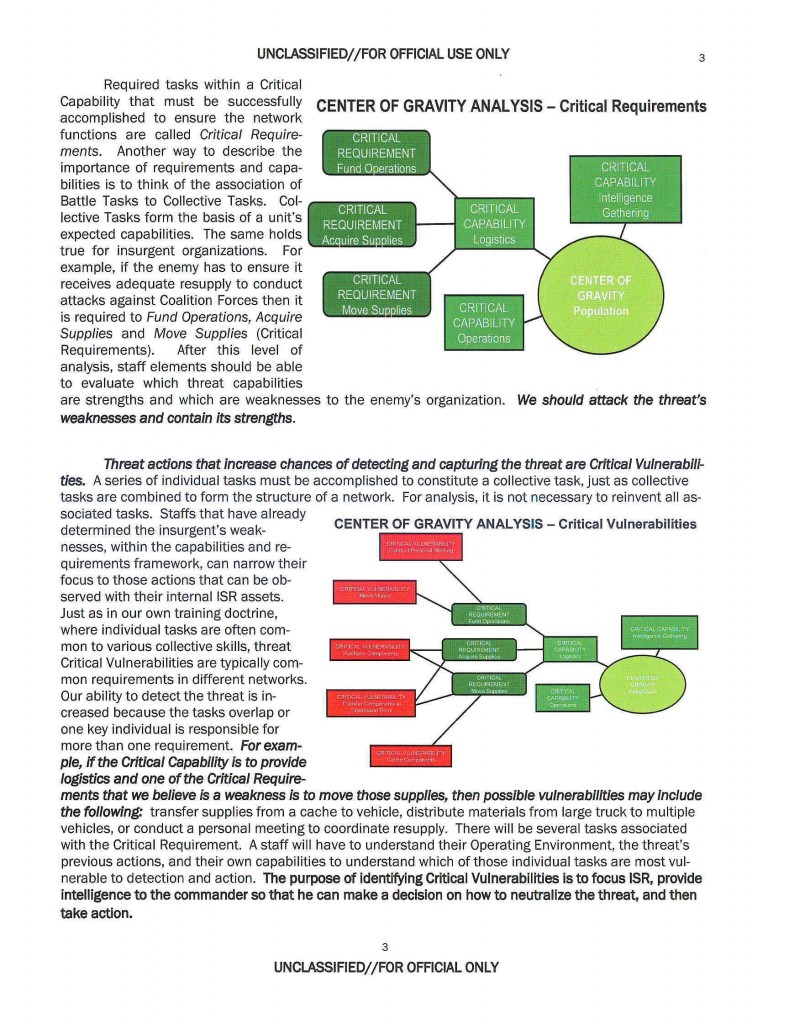
This document facilitates discussion, training, and implementation of effective targeting methods at the Battalion and Brigade level. This paper discusses the Center of Gravity analysis model for identifying threat networks, Critical Capabilities, and Critical Vulnerabilities; use of the methodology to determine the Intelligence Surveillance and Reconnaissance (ISR) focus; and as a basis for understanding Attack the Network concepts.
…
 Asymmetric Warfare Group
Asymmetric Warfare Group
- ATTACK THE NETWORK METHODOLOGY: PART 3 NETWORK MODELING AND ISR SYNCHRONIZATION
- 12 pages
- For Official Use Only
- April 2009
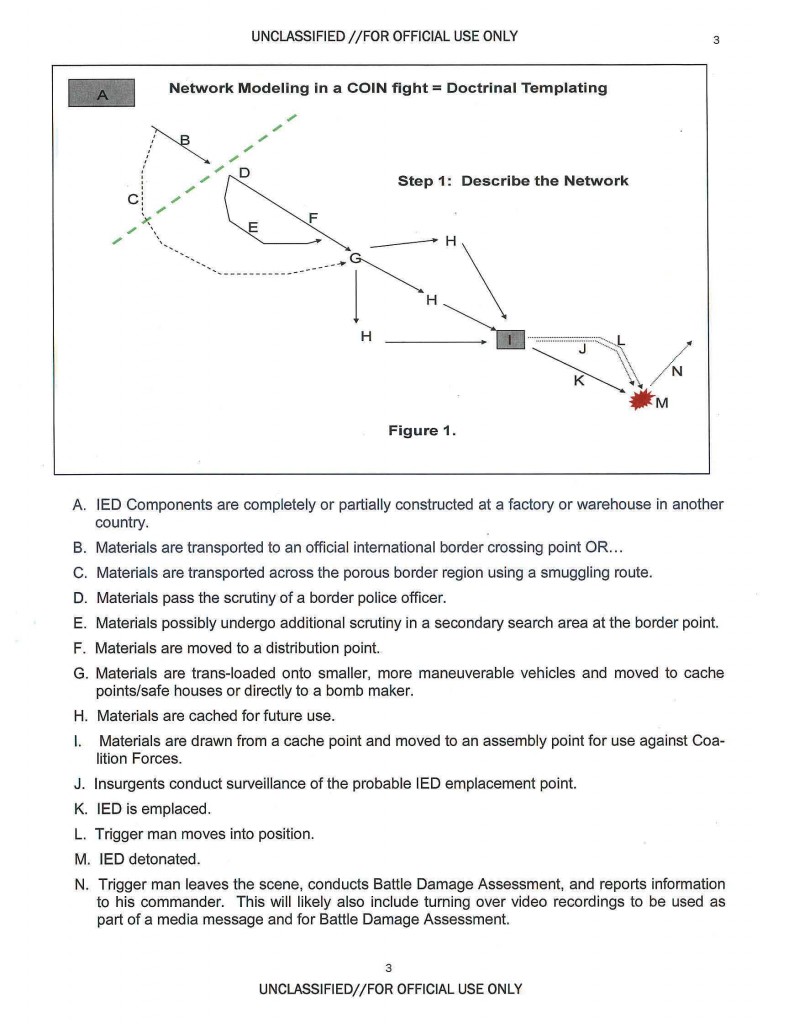
This document continues discussion on effective targeting methods (lethal and non-lethal) at the Battalion and Brigade level. It continues dialogue on Attacking the Network by further describing Center of Gravity and Critical Vulnerability analysis themes and their link to network modeling. This document also discusses the use of detailed, Observable Indicators to focus Intelligence Surveillance and Reconnaissance assets against the enemy’s vulnerabilities. A modified Intelligence Synchronization Matrix (ISM) ensures integration and synchronization to the friendly course of action in a Counter-Insurgency environment. Using doctrinal and situational templates and a modified ISM helps the S2 understand the insurgent networks operating in his Area of Interest, focus assets against the known or suspected Critical Vulnerabilities, and synchronize ISR to give the commander the information he needs at the Decision Points.
…