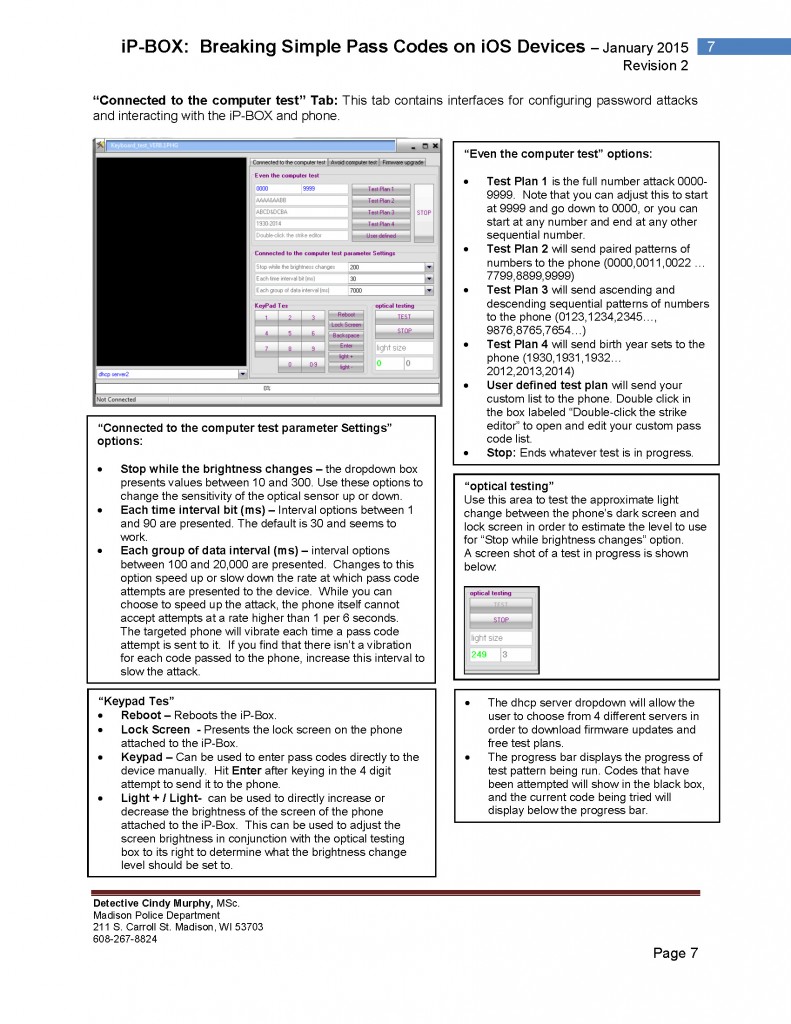
There is a new ‘black box’ that originates from phone unlocking, hacking and repair market called the iP-BOX, which can be used to defeat simple 4 digit pass codes on potentially any iOS device, including all versions of iOS1 through iOS8. Although for iOS8.1 and above, the exploit being used by the device may have been patched by Apple, there are still reports of success on iOS8.x.x devices, and the manufacturer of the iP-BOX reports that these devices are supported with an add on PCB card used in conjunction with the iP-BOX.
When used to break iOS pass codes for evidentiary purposes, the iP-BOX should be considered an advanced mobile device forensics tool, and is not recommended for those who are not familiar with hardware and software troubleshooting, mobile device forensics process and practices. This is not a simple plug and play solution for breaking pass codes, and the software and iP-BOX settings may need to be set up slightly differently for each phone. It is essential to know what version of iOS (the operating system on the device, not the hardware version) is running on the phone prior to beginning the pass code attack. Free tools such as iFunbox2014 can be used to determine the version of iOS running on the device prior to beginning the attack, so that you have a clue as to what settings to use on the phone and the device. There are variations in setup of the iP-BOX attack for each version of iOS, as described on page four of this document.
There is minimal documentation available for the device, and much of the available documentation is in Chinese. This document is intended to assist forensic examiners in learning basic operation of the iP-BOX device, as well as to provide information about how the device operates. It is not intended to endorse use of the device, as that decision will be made based upon your own agencies policies and procedures, as well as legal authority to break pass codes on a case by case basis. It is also not intended as a comprehensive description of testing of the device – the software is updated frequently, and resulting changes in the operation of the device and software may mean that future versions deviate somewhat from what is described here. Additionally, some testing has been done regarding what communications occur when the device is attached to the software via a computer with an internet connection. This testing has only been done with version 6.3 of the software at this point, and so users in Law Enforcement positions or in situations involving sensitive information should test the current version of the software/device prior to its use, and should be sure their use of the device is in accordance with their agencies policies, procedures, and with their legal authority in each specific case.
iP-BOX Components and Overview: The iP-Box kit consists of the box itself, iPhone cables, a USB cable, an optical sensor. The associated iP-BOX software/firmware updates can be obtained via the manufacturer’s site or GSM Forum with a valid user account1. The device can be operated either in a standalone fashion after firmware updates and password attacks (referred to as “tests” in the iP-BOX software and documentation) are set up via the software, or it can be connected to a computer during operation.
Basically, the iP-BOX operates by sending pre-defined pass code lists to the targeted iOS device. Each attempt takes approximately 6 seconds to perform, and so the dictionary containing all numbers between 0000 and 9999 would take between 6 seconds and approximately 17 hours to complete. Custom dictionaries can cut down on the amount of total time used to attack the pass code, and may be utilized before a full attack if desired. The images below show the box set up to operate in stand-alone mode on a pass code protected iPhone 4S. The optical sensor has been attached to the screen, and the appropriate iPhone cable has been connected to the phone. In the image on the left the test is in progress, and in the image on the right, the test has completed successfully, and the password has been broken and was found to be 8664.
…