The following document was filed with the U.S. Patent and Trademark Office in 2006.
TrapWire Pre-Attack Terrorist Detection System For Protecting Critical Infrastructure
- 7 pages
- 2004
- 3.83 MB
The prevention of terrorist attacks on critical infrastructure requires the ability to detect various discreet but identifiable indicators of pre-attack preparations. Only by uncovering such attack preparations can we take actions designed to deter or intercept a terrorist strike before it begins. While international terrorist organizations are using increasingly sophisticated methods, their modus operandi does contain a critical vulnerability: meticulous pre-attack preparations require the terrorists to approach a target facility on multiple occasions to identify physical and procedural vulnerabilities, probe for weaknesses and conduct practice missions. For example, the terrorists planning the Khobar Towers attack in Saudi Arabia reportedly surveilled the facility on 40 occasions.
Terrorists will typically surveil multiple facilities prior to selecting an appropriately vulnerable target. Therefore, as the number of facilities on the Trap Wire network increases, so does the probability of detecting pre-attack preparations. Trap Wire is specifically designed to exploit this vulnerability by combining deep counterterrorism experience, proven counter-surveillance techniques, unique sensor systems, and data mining capabilities to detect attack preparations and allow security personnel to deter or intercept terrorist operations.
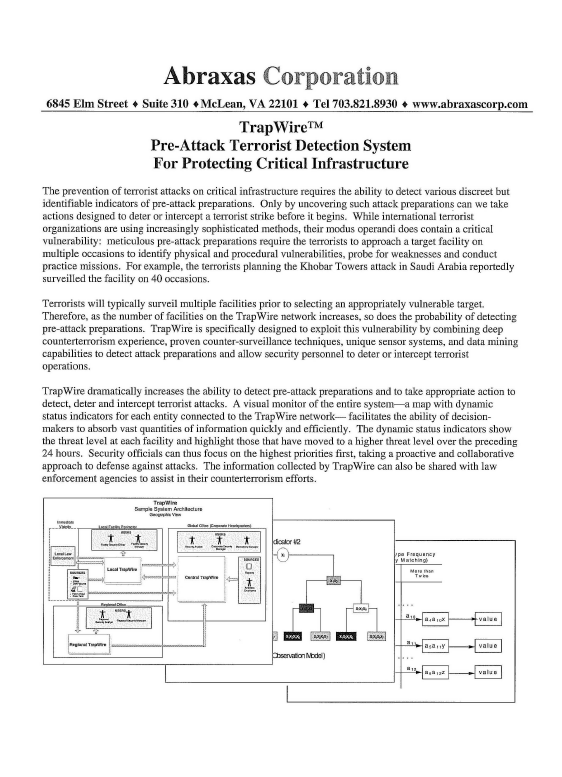
Trap Wire dramatically increases the ability to detect pre-attack preparations and to take appropriate action to detect, deter and intercept tenorist attacks. A visual monitor of the entire system-a map with dynamic status indicators for each entity connected to the Trap Wire network- facilitates the ability of decisionmakers to absorb vast quantities of information quickly and efficiently. The dynamic status indicators show the threat level at each facility and highlight those that have moved to a higher threat level over the preceding 24 hours. Security officials can thus focus on the highest priorities first, taking a proactive and collaborative approach to defense against attacks. The information collected by Trap Wire can also be shared with law enforcement agencies to assist in their counterterrorism efforts.
…
The basic premise behind the TrapWire system is as follows: Through the systematic reporting of suspicious events and the correlation of those events with other event reports for that facility and for related facilities across the network, terrorist surveillance operations can be identified, appropriate countermeasures can be employed to deter attacks, and steps can be taken to apprehend the perpetrators.
The TrapWire system provides the following capabilities:
• A mechanism for a facility’s personnel to record suspicious activity data in a structured format;
• A mechanism to identify and link related events following human review;
• The ability for a facility’s Chief Security Officer (CSO) to identify threat trends at his/her facility (increasing or decreasing) and to drill down into the specific event reports that generated those threats;
• Alerts to the CSO of events that do not affect the threat score but may nevertheless be of interest;
• The ability to notify a facility of a changing threat level within its industry or geographical location;
• A mechanism to correlate external events such as watch list events for suspected terrorists or stolen vehicles with other observed event data already within the system;
• The ability to correlate events occurring at different facilities by related individuals, and to notify all affected facilities of the increased threat to their facility based on this related activity;
• A mechanism to reduce the system-calculated threat level at a facility, based upon the time since the last threatening event; and
• Notifications, alerts, and possible action recommendations based on a particular site’s security plan, implemented via a set of rules that act upon event information.