 The Silicon Valley High Technology Task Force, also known as the Rapid Enforcement Allied Computer Team (REACT), is a partnership of 17 local, state, and federal agencies, with the Santa Clara County District Attorney’s Office designated as the lead agency. The REACT Task Force is one of five in the State of California and authorized under California Penal Code 13848. All Agents of the React Task Force are either California Peace Officers and/or U.S. Federal Agents.
The Silicon Valley High Technology Task Force, also known as the Rapid Enforcement Allied Computer Team (REACT), is a partnership of 17 local, state, and federal agencies, with the Santa Clara County District Attorney’s Office designated as the lead agency. The REACT Task Force is one of five in the State of California and authorized under California Penal Code 13848. All Agents of the React Task Force are either California Peace Officers and/or U.S. Federal Agents.
REACT was established in 1997 by the California State Department of Justice, in response to both public and industry concerns over the spread of new types of crime directly tied to our increasingly computer-oriented economy and widespread use of the Internet. High tech companies and industry councils provide specialized training, liaison personnel and internal support for task force investigations.1
Notable Activities
On October 5, 2009, the Rapid Enforcement Allied Computer Team (REACT) received a report of an unknown suspect making a threat via the Internet to attack his school with explosives. The threat stated the following:
“Today at 11:30 est I will attack my school with grenades and other forms of violence. Those bastards will pay. Watch here – cnn.com/live.news.”
The suspect attempted to post this threat in a user’s forum of an online computer game on October 5. The company hosting the forum, located in the Bay Area, intercepted the threat before it was posted. The company then immediately reported this incident to local law enforcement. It, in turn, referred the matter to REACT, which specializes in high-tech crimes. Task Force Agent Matt Broad conducted extensive investigation and traced the posting to a male juvenile living in the area of Rocky Mount, North Carolina. The suspect attended a continuation school for troubled youth. Despite the threat, no attack occurred at the school.
REACT then assisted the Rocky Mount Police Department which continued the investigation in North Carolina. On October 15, the suspect was arrested and his residence was searched via a search warrant. No destructive devices or related materials were located during the search. There were, however, written drawings depicting explosions found in the suspect’s possession. The suspect was detained for making a false report of a destructive device and was later released to the custody of his mother pending a juvenile hearing, scheduled for October 27th, 2009, in North Carolina.2
On April 23, 2010 REACT agents served a search warrant at the home of Gizmodo editor Jason Chen, who was suspected of potentially committing a felony in acquiring a reportedly stolen copy of a prototype version of the next generation Apple iPhone. The REACT task force has been criticized for using a warrant, as a subpoena is required to obtain information from journalists who are conveying information to the public. According to Threat Level blog at Wired.com, “federal Privacy Protection Act prohibits the government from seizing materials from journalists and others who possess material for the purpose of communicating to the public. The government cannot seize material from the journalist even if it’s investigating whether the person who possesses the material committed a crime. Instead, investigators need to obtain a subpoena, which would allow the reporter or media outlet to challenge the request and segregate information that is not relevant to the investigation.” The article also describes the search warrant incident in greater detail:
On Friday, officers from California’s Rapid Enforcement Allied Computer Team in San Mateo, California, appeared at the home of Gizmodo editor Jason Chen while he was not there and broke open the front door.
Chen and his wife discovered the officers when they returned from dinner around 9:45 that evening. According to an account he posted online, Chen noticed his garage door was partly open, and when he tried to open it completely, officers came out and told him they had a warrant to search the premises. The warrant had been signed just hours earlier, at 7:00 p.m., by a San Mateo County Superior Court judge. It allowed the police to search Chen, his residence and any vehicle in his control.
The officers were in the process of cataloging the items they had already taken from the premises and told Chen they had been in his home a “few hours already.” According to California law, a search warrant may be served between 7 a.m. and 10 p.m. unless otherwise authorized.
The officers told Chen he could request reimbursement for the damage to his front door.
Jennifer Granick, civil liberties director for the Electronic Frontier Foundation, said Chen is protected from a warrant by both state and federal laws.
The federal Privacy Protection Act prohibits the government from seizing materials from journalists and others who possess material for the purpose of communicating to the public. The government cannot seize material from the journalist even if it’s investigating whether the person who possesses the material committed a crime.3
Involvement of Private Businesses
A number of private companies serve on a “Steering Committee” which is of unknown relation to the Task Force and its operations. In fact, REACT does not make the members of its steering committee public and only limited examples are known. According to the REACT Task Force’s most recent public report, the Steering Committee is to be “comprised of representatives from participating agencies, local high technology industry, and other interested parties. The steering committee shall, at a minimum, meet quarterly to review task force activities, and provide advice, recommendations, strategic input and direction for task force consideration.”
All publicly known examples of Steering Committee members are private corporations and many of them have interests that are directly affected by the Task Force’s activities. In 2006, REACT broke up a counterfeiting ring that was selling pirated copies of Norton Antivirus, which is produced by steering-committee member Symantec. Likewise, piracy investigations have been undertaken by the REACT Task Force on behalf of Microsoft and Adobe. 4
Following the raid on Gizmodo editor Jason Chen, many have questioned what role may have been played by Apple Inc., which is also on the the REACT Task Force Steering Committee. On April 27, 2010 the Threat Level blog reported that representatives of Apple may have traced the iPhone back to Chen’s original source and confronted the individual at his home.5 This confrontation allegedly occurred prior to the REACT raid at Chen’s home, calling the Task Force’s motives further into question.
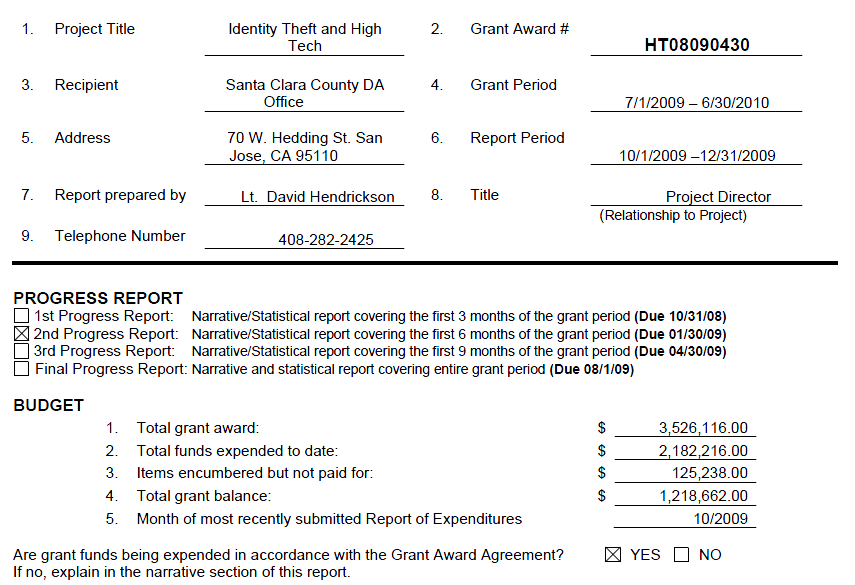
2009 Budget Grants
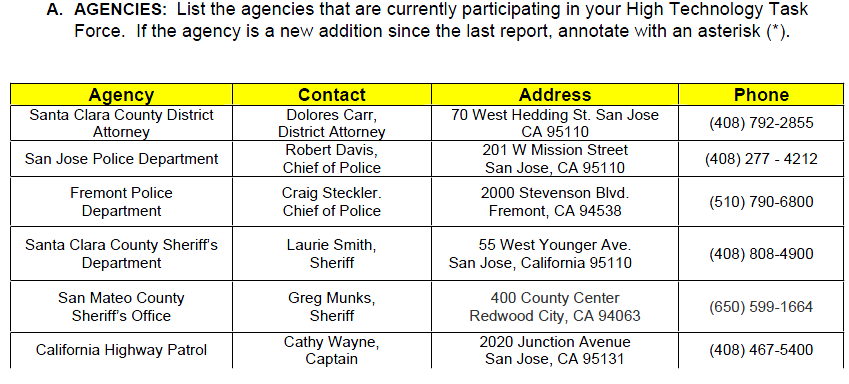
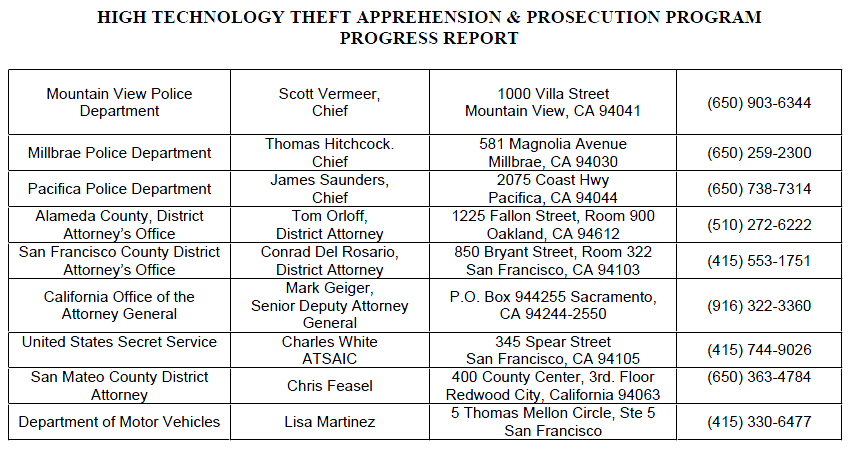
Participating Agencies
- Atherton Police Department
- California Highway Patrol
- Federal Bureau of Investigation
- Freemont Police Department
- Mountain View Police Department
- Pacifica Police Department
- San Francisco County District Attorney’s Office
- San Jose Police Department
- San Mateo County Sheriff’s Department
- Santa Clara County District Attorney’s Office
- Santa Clara County Sheriff’s Department
- United States Secret Service
- Department of Motor Vehicles
- Millbrae Police Department
Corporate Steering Committee
- Adobe Systems Incorporated6
- American Express7
- Apple Inc.8
- Applied Materials Inc.9
- BayTSP10
- Bechtel11
- Cadence Design Systems, Inc.12
- Cisco Systems Inc.13
- Creative Security Company14
- eBay, Inc.15
- Google Inc.16
- Hitachi17
- KLA-Tencor Inc.18
- Microsoft Corporation19
- Oracle20
- Palm21
- PG&E22
- Prosper23
- Seagate24
- Sony Computer Entertainment25
- Symantec Corp.26
- Synopsys27
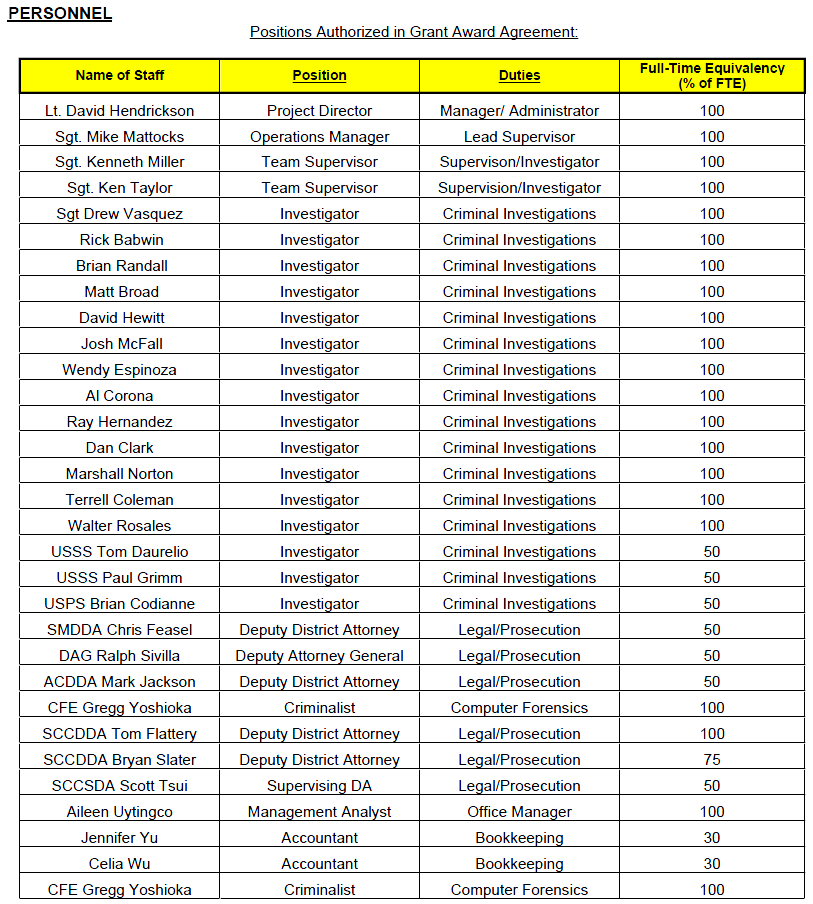
Current Members
- Lt. David Hendrickson, Project Director, Manager/ Administrator
- Sgt. Mike Mattocks, Operations Manager, Lead Supervisor
- Sgt. Kenneth Miller, Team Supervisor, Supervison/Investigator
- Sgt. Ken Taylor, Team Supervisor, Supervision/Investigator
- Sgt Drew Vasquez, Investigator, Criminal Investigations
- Rick Babwin, Investigator, Criminal Investigations
- Brian Randall, Investigator, Criminal Investigations
- Matt Broad, Investigator, Criminal Investigations
- David Hewitt, Investigator, Criminal Investigations
- Josh McFall, Investigator, Criminal Investigations
- Wendy Espinoza, Investigator, Criminal Investigations
- Al Corona, Investigator, Criminal Investigations
- Ray Hernandez, Investigator, Criminal Investigations
- Dan Clark, Investigator, Criminal Investigations
- Marshall Norton, Investigator, Criminal Investigations
- Terrell Coleman, Investigator, Criminal Investigations
- Walter Rosales, Investigator, Criminal Investigations
- USSS Tom Daurelio, Investigator Criminal Investigations
- USSS Paul Grimm, Investigator, Criminal Investigations
- USPS Brian Codianne, Investigator, Criminal Investigations
- SMDDA Chris Feasel, Deputy District Attorney, Legal/Prosecution
- DAG Ralph Sivilla, Deputy Attorney General, Legal/Prosecution
- ACDDA Mark Jackson, Deputy District Attorney, Legal/Prosecution
- CFE Gregg Yoshioka, Criminalist, Computer Forensics
- SCCDDA Tom Flattery, Deputy District Attorney, Legal/Prosecution
- SCCDDA Bryan Slater, Deputy District Attorney, Legal/Prosecution
- SCCSDA Scott Tsui, Supervising DA, Legal/Prosecution
- Aileen Uytingco, Management Analyst, Office Manager
- Jennifer Yu, Accountant, Bookkeeping
- Celia Wu, Accountant, Bookkeeping
- CFE Gregg Yoshioka, Criminalist, Computer Forensics
Former Members
Contact Information
South Headquarters:
Telephone: (408) 282-2420
Fax: (408) 282-2421
REACT TASK FORCE
950 South Bascom Ave #3011
San Jose, CA 95128
San Jose FBI
(408) 494-7186
North Field Office:
Telephone: (650) 655-1060
Fax: (650) 655-1077
Share this:
Source notes:
- About us. REACT Task Force. http://www.reacttf.org/10701.html [↩]
- REACT Nabs Suspect who made on-line terrorist threat. Sccvote.gov http://www.sccvote.org/portal/site/da/agencyarticle?path=%252Fv7%252FDistrict%2520Attorney%252C%2520Office%2520of%2520the%2520%2528DEP%2529&contentId=572e5d228b284210VgnVCM10000048dc4a92____ [↩]
- Kim Zetter. Expert: Invalid Warrant Used in Raid on iPhone Reporter’s Home. Wired. http://www.wired.com/threatlevel/2010/04/iphone-raid/ [↩]
- John Cook. What is Apple Inc. role in task force investigating iPhone case? Yahoo! News. April 27, 2010. http://news.yahoo.com/s/ynews/ynews_ts1795 [↩]
- Evan Hanson. Apple May Have Traced iPhone to Finder’s Address. April 27, 2010. http://www.wired.com/threatlevel/2010/04/dude-apple/ [↩]
- 2008 High Technology Crime In California: Annual Report to the Governor & Legislature. Public Intelligence. https://publicintelligence.net/2008-high-technology-crime-in-california-annual-report-to-the-governor-legislature/ [↩]
- Ibid. [↩]
- Mary Duan. Valley REACTs to Craigslist counterfeits. Silicon Valley Business Journal. http://sanjose.bizjournals.com/sanjose/stories/2009/05/18/story2.html [↩]
- 2008 High Technology Crime In California: Annual Report to the Governor & Legislature. Public Intelligence. https://publicintelligence.net/2008-high-technology-crime-in-california-annual-report-to-the-governor-legislature/ [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- John Letzing. Apple has sat on steering committee for task force. MarketWatch. http://www.marketwatch.com/story/apple-has-sat-on-steering-committee-for-task-force-2010-04-27 [↩]
- 2008 High Technology Crime In California: Annual Report to the Governor & Legislature. Public Intelligence. https://publicintelligence.net/2008-high-technology-crime-in-california-annual-report-to-the-governor-legislature/ [↩]
- Mary Duan. Valley REACTs to Craigslist counterfeits. Silicon Valley Business Journal. http://sanjose.bizjournals.com/sanjose/stories/2009/05/18/story2.html [↩]
- Ibid. [↩]
- 2008 High Technology Crime In California: Annual Report to the Governor & Legislature. Public Intelligence. https://publicintelligence.net/2008-high-technology-crime-in-california-annual-report-to-the-governor-legislature/ [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- Ibid. [↩]
- 2008 High Technology Crime In California: Annual Report to the Governor & Legislature. Public Intelligence. https://publicintelligence.net/2008-high-technology-crime-in-california-annual-report-to-the-governor-legislature/ [↩]