The 71st Bilderberg Meeting will take place from 12 – 15 June 2025 in Stockholm, Sweden. As ever, a diverse group of political leaders and experts from industry, finance, academia and the media has been invited.
United States
U.S. Senate Homeland Security Committee Interim Report on July 13th, 2024 Trump Assassination Attempt

On July 13, 2024, Thomas Matthew Crooks bought 50 rounds of ammunition on his way to Butler, Pennsylvania, drove to former President Donald Trump’s campaign rally at the Butler Farm Show grounds, and climbed onto the roof of the American Glass Research (AGR) building less than 200 yards away from where the former President was speaking, where at 6:11 pm, he fired eight rounds from an AR-15 semiautomatic rifle, killing one person and injuring three others including the former president. That day, he was able to fly a drone 200 yards from the site, use a rangefinder capable of gauging the distance to the former president less than an hour before he began speaking, and bring two explosive devices within proximity of the site of the rally. The United States Secret Service’s (USSS’) planning, communications, intelligence sharing, and related security failures in advance of and during July 13 directly contributed to Crooks’ ability to carry out the assassination attempt and kill and injure people in Butler, PA that day.
Australia, Canada, France, Internal Revenue Service, United Kingdom
Joint Chiefs of Global Tax Enforcement Crypto Assets Risk Indicators for Financial Institutions

The J5, a collaborative partnership among tax authorities and law enforcement from five countries, has identified several risk indicators that financial institutions should be aware of. Risk indicators play a pivotal role in enhancing the ability of financial institutions to detect and report money laundering and illicit activities involving crypto assets. To counteract these risks, timely identification allows institutions to intervene and to report to the relevant authorities contributing to the overall integrity of the financial system and ensure compliance with anti-money laundering (AML) regulations.
Bilderberg Participant Lists
2024 Bilderberg Meeting Participant List
The 70th Bilderberg Meeting will take place from 30 May – 2 June 2024 in Madrid, Spain. As ever, a diverse group of political leaders and experts from industry, finance, academia, labour and the media has been invited.
United States
U.S. House Financial Surveillance Report: How Federal Law Enforcement Commandeered Financial Institutions to Spy on Americans

The Committee on the Judiciary and its Select Subcommittee on the Weaponization of the Federal Government are charged by the House of Representatives with upholding fundamental American civil liberties. As a part of this mission, the Committee and Select Subcommittee have uncovered startling evidence that the federal government was engaged in broad financial surveillance, prying into the private transactions of American consumers. This financial surveillance was not predicated on any specific evidence of particularized criminal conduct and, even worse, it keyed on terms and specific transactions that concerned core political and religious expression protected by the Constitution.
Iran, U.S. Army
Asymmetric Warfare Group Iran Quick Reference Guide

Since its inception in 1979, the Islamic Republic of Iran has repeatedly disrupted the stability of the Middle East and fostered terrorist threats throughout the world. Iran exploited the power vacuum which followed the Iraq War in 2003 and Arab Spring in 2011 to significantly extend its regional influence, primarily through the establishment of proxy groups and new relationships with existing regional terrorist groups. International sanctions against Iran, levied in response to Iran’s support for terrorism and nuclear activities, constrained Iran’s actions, but did not end them, nor did they stop Iran from enhancing its conventional military enterprise.
Federal Bureau of Investigation
(U//FOUO) FBI Domestic Terrorism Reference Guide: Sovereign Citizen Violent Extremism

Sovereign citizens are US citizens who claim to have special knowledge or heritage that renders them immune from government authority and laws. Although the ideology itself is not illegal, sovereign citizen violent extremists express their anti-government or anti-authority violent extremist beliefs through the use or threat of force or violence, while sovereign citizen criminals use these beliefs to justify non-violent activities, such as fraud and theft. Sovereign citizen violent extremists or sovereign citizen criminals may attempt to frame legal encounters with government officials as negotiable commercial transactions, or claim legal immunity based on “common law rights of man.”
Department of Justice
Department of Justice Critical Incident Review Active Shooter at Robb Elementary School

On May 24, 2022, a mass shooting at Robb Elementary School in Uvalde, Texas, shook the nation. With just two days left in the school year, a former student armed with an AR-15 style assault rifle took the lives of 19 students and two teachers, physically injured at least 17 others, and left countless families, friends, and a community grief-stricken for their unimaginable loss. In the aftermath of the tragedy, there was significant public criticism of the law enforcement response to the shooting. At the request of then Uvalde Mayor Don McLaughlin, the U.S. Department of Justice (DOJ) announced on May 29, 2022, that it would conduct a Critical Incident Review (CIR) of the law enforcement response to the mass shooting. Recognizing that “[n]othing can undo the pain that has been inflicted on the loved ones of the victims, the survivors, and the entire community of Uvalde,” the Attorney General stated that the goal of the CIR was to “assess what happened and to provide guidance moving forward.”
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 8 January 9, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 7 January 8, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 6 January 5, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 5 January 5, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 4 January 5, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 3 January 5, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 2 January 4, 2024
United States
Virginia Guiffre v. Ghislaine Maxwell Unsealed Jeffrey Epstein Documents Batch 1 January 3, 2024
U.S. Army
(U//FOUO) U.S. Army Threat Integration Center (ARTIC) Report: Indications of Extremism in the Military 2017-2019

Due to indications of an increase in extremist activity by former and current military personnel, evidenced by a spike in open source reporting, the ARTIC has produced this report examining 22 cases of current and former DoD members expressing support for and or allegedly affiliated with extremist groups while serving in or having recently separated from the military from 2017 – 2019. For the purposes of this report, the ARTIC considered an organization to be “extremist” if its core ideology espouses racially motivated hatred, such as Neo-Nazism, white supremacism, or black separatism, and or religious hatred, such as espoused by al-Qa’ida or the Islamic State of Iraq and Syria. The majority of the information within this report was obtained via open sources. Due to the nature of open source reporting, and the possibility of ongoing investigations involving DoD personnel within this report, some of the allegations presented may prove to be unfounded.
Department of Homeland Security
DHS Public-Private Analytic Exchange Program Report: Combatting Illicit Activity Utilizing Financial Technologies and Cryptocurrencies Phase II

Phase 2 of the research serves to build upon the foundation laid in Phase 1. The Phase 2 research further explores: the criminal groups utilizing digital assets in illegal activities; how these criminal groups are conducting illicit activity and recruiting members; cryptocurrency ATMs and Point-of-Sales illicit uses; generative AI applications in cybercrime; darknet market use of digital assets; the evolving use of cryptocurrencies (especially the year to date change); criminal activity’s impact on government and private sector; and additional policy recommendations. Although illicit use can never be completely eliminated, it can be mitigated by increased consumer knowledge, proactive law enforcement investigations, and better practices and regulations issued by key stakeholders.
Department of Homeland Security
DHS Public-Private Analytic Exchange Program Report: Combatting Illicit Activity Utilizing Financial Technologies and Cryptocurrencies Phase I

Private and public sector analysts and subject matter experts working in the cyber financial landscape gathered through a series of meetings to examine the use of financial technologies and cryptocurrencies by illicit actors. The key research points investigated include discovering the most common illicit finance activities, the most exploited elements of financial technologies, the legal vulnerabilities that allow exploitation, pseudo-anonymity in online transactions, weaknesses in Know-Your-Customer laws, and the risks of use associated with other emerging blockchain applications (i.e. NFTs). The research gathered from investigating these areas led to the development of suggested, effective changes to reduce illicit activity in this space and identifying the key stakeholders to implement these changes. This paper seeks to provide guidance in navigating cryptocurrencies, emerging digital payment solutions, and other blockchain applications to both consumers and stakeholders to minimize the illicit use of these platforms. While illicit use cannot be eliminated altogether, it can certainly be reduced with better consumer knowledge and better practices/regulations issued by key stakeholders.
Michigan
(U//FOUO) Michigan High Intensity Drug Trafficking Area Threat Assessment 2023

The threat from the production, use, and trafficking of illegal drugs throughout the State of Michigan continues to be of great concern. In 2022, the demand and availability of some commonly used drugs increased while others slightly decreased compared to 2021. Also, several drugs showed an increase in use, while others showed a slight decrease throughout the state during the 2022 reporting period. According to drug teams’ survey responses on the most significant threat in their area of responsibility (AOR), as well as contributing factors such as availability and seizures, the drug threat ranking has remained the same from the previous reporting period.
National Counterterrorism Center
(U//FOUO) NCTC Report: Terrorist and Militant Attacks on Electricity Infrastructure Continue at High Rate
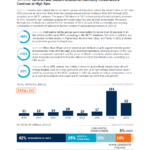
Terrorist and militant attacks on electric power infrastructure outside the United States in 2021 and 2022 occurred at more than three times the average annual number of attacks from 2015 through 2020, according to an NCTC database. The peak of 101 attacks in 2021 at least partly reflected incidents attributed to ISIS’s “economic war” campaign, judging from press reporting and terrorist social media. We expect the high rate of attacks to continue for the remainder of 2023 because of the accessibility and ongoing vulnerability of electricity infrastructure and the number of well-publicized attacks in 2021-22.
Department of Homeland Security
(U//FOUO) CISA Report: Continuity of the Economy Response

The key finding of the COTE response is that, broadly, COTE plan requirements included in the FY 2021 NDAA are addressed through existing authorities, policies, plans, and frameworks. Creation of a COTE plan with a singular economic focus, coupled with new response frameworks, has the potential to create confusion and duplicate existing response and recovery mechanisms. However, the fundamentally important concept of economic recovery and response detailed in the COTE requirement should be deeply integrated within existing incident response frameworks to avoid creating an additional layer of potentially divergent planning and response activities operating in parallel to already established procedures. In lieu of developing a standalone COTE plan, the federal government should continue to refine and strengthen existing authorities, policies, plans, and frameworks for Federal Mission Resilience and domestic incident preparedness, response, and recovery. This COTE response provides several specific recommendations for how the federal government can continue to enhance the ability to maintain and restore the U.S. economy in response to a significant event.
Intelligence Fusion Centers, New Mexico
(U//LES) New Mexico Fusion Center Bulletin: Peace in Ukraine Protest

Peace In Ukraine protest is scheduled to take place March 18, 2023 at San Mateo and Gibson in Albuquerque at 1400 hrs.. This protest is hosted by the Party for Socialism and Liberation. There are no known numbers at this time, however based on historical events with PSL, they tend to have 50-150 people show up depending on the cause.
China, Department of Homeland Security
(U//FOUO) DHS Report: Chinese Municipal Government Publishing Anti-US Social Media Content With Limited Reach

A People’s Republic of China (PRC) municipal government-controlled media outlet is very likely directing a cluster of English-language, coordinated inauthentic Twitter accounts that posted content denigrating the United States (see graphics). The cluster of accounts, which we have dubbed SPICYPANDA, has been active from at least January 2021 and has published sophisticated content, but it failed to grow a follower base thus far. DHS attributed SPICYPANDA to the municipal media entity Chongqing International Communications Center (CICC) based on its leadership’s creation of SPICYPANDA’s anti-US messaging campaign, its overt ties to a website promoted by the accounts, and its Western social media messaging accolades and capabilities.
Federal Bureau of Investigation
(U//FOUO) FBI Domestic Terrorism Reference Guide: Anarchist Violent Extremism

Anarchist violent extremists are anti-government/anti-authority violent extremists who consider capitalism and centralized government to be unnecessary and oppressive, and who further their political or social goals wholly or in part through illegal activities involving threat or use of force or violence in violation of criminal law. In support of their goals of eliminating capitalism and the current form of the US Government, anarchist violent extremists oppose economic globalization; political, economic, and social hierarchies based on class, religion, race, gender, or private ownership of capital; and external forms of authority represented by centralized government, the military, and law enforcement. Anarchist violent extremists believe the abolition of capitalism and the state would restore equality and encourage the need for mutual cooperation.








