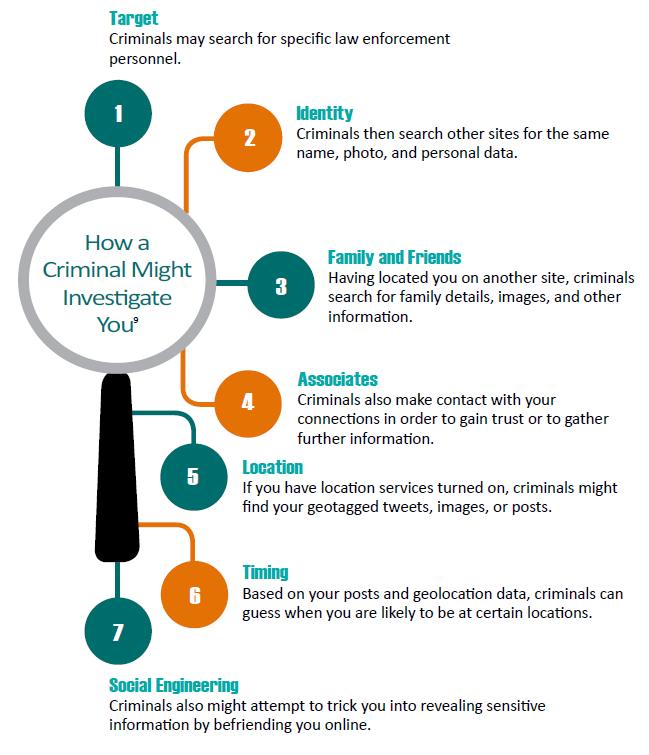
Internet connectivity has become a large part of nearly everyone’s daily routine. Whether through personal or professional use, this technology has been engrained in our society. With this connectivity, the amount of personal information made available to the general public has dramatically increased an individual’s digital footprint. This personal information is enticing to those with malicious intent and can easily be acquired and used to target law enforcement personnel and their families. For example, the 2014 fatal shooting of Michael Brown by a police officer in Ferguson, Missouri, brought widespread media coverage, and the actions surrounding the event led to the compromise of personal information of law enforcement personnel in Ferguson and the surrounding area.
Another recent case example involved more than 30 Minnesota police officers whose personal information was exploited by a hacker group affiliated with ISIS. The information included home and e-mail addresses and personal phone numbers. The names of the officers were posted along with a photo of masked ISIS fighters holding automatic weapons.
Personal information is increasingly distributed online by the media, the public, law enforcement agencies, and even law enforcement personnel themselves. It is imperative that law enforcement personnel understand the importance and consequences of their online activities and be proactive in monitoring and limiting their digital footprint. What may seem like an innocent upload or shared post can have a significant effect not only on law enforcement personnel but on their departments, families, and friends. Law enforcement should take the steps now to protect themselves and their family members before becoming a victim.
There are multiple areas in which personal information can be both collected and exposed on the Internet. Data brokers5 such as PiPl®, Spokeo®, and White Pages® routinely compile comprehensive information from government and public records, such as court filings, real property, telephone directories, recorded liens and mortgages, marriage and death records, retailers, and social media platforms. In many cases, the information collected by these brokers may be out of date or inaccurate, adding additional safety concerns. The information from these brokers is sold or provided for free to anyone with an Internet connection.
Law enforcement personnel can easily make themselves, their families, coworkers, and agencies vulnerable by oversharing their personal information. One area of great concern is social media. With more than 1.6 billion active Facebook® users and more than 7,200 tweets being sent every second, it is critical for law enforcement personnel to understand best practices for keeping their personal information safe and secure. In general, individuals should follow strict privacy settings, maintain strong passwords, and utilize secure networks.
…
…
Protecting Personal Information
The amount of personal information available online is astounding, and the process of redacting or removing that information is difficult and time-consuming. While there are resources to help educate and assist law enforcement personnel and their families in accomplishing this task, there is no single solution. One way to begin removing personal information is to identify and verify the sites where personal data is provided and follow their opt-out procedures. These procedures can vary significantly: some require letters, some require photo identification, and others simply require completing an online form. Once the request to opt out has been identified and completed, individuals should ensure that their information has been removed. This is a continuous process in which individuals should routinely track their digital footprints and review the amount of information available on themselves and their families.
Many social media platforms have customizable privacy settings. Users should explore these settings and determine best practices for keeping their information secure. For example, Twitter®’s privacy settings allow users to disable location information related to their tweets as well as control who views their tweets. This is just one example of how individuals can keep their information secure.
Privacy settings often change with software and “app” updates, potentially exposing personal information during upgrades or when new features are added. It is imperative to recheck configuration settings after every operating system upgrade and installation to review what personal information (e.g., location and contacts) certain applications have access to when they are installed or upgraded.
Law enforcement personnel should ensure that their mobile devices are secure. If a device has not been made secure, the data on the device could put law enforcement personnel, their families and friends, and their agencies at risk. Contacts, messages, photos, social media feeds, location data, and more can be derived from these devices, with devastating results if they are compromised. Simple solutions such as password protection, two-factor authentication, connecting to secure networks, allowing auto-updates for “apps” and software, and turning off Wi-Fi and Bluetooth when not in use can help prevent personal information from being compromised.
Physical security of mobile devices and personal networks is just as important. Law enforcement personnel and their family members should remain vigilant of those attempting to gain access, take preventive measures such as securing home Wi-Fi, and be conscious of those attempting to “shoulder surf” or use other observation techniques to collect information. Law enforcement personnel should also ensure that devices are protected with biometrics or a password, such as the pattern lock screen on Android devices or Touch ID on iPhones, and enable the lost device or remote tracking/wiping feature(s) and the automatic updates for apps and software on the device.
Law enforcement personnel should also be cognizant in securing internal and external storage devices (hard drives, thumb drives, memory cards, etc.). These devices can be secured either physically or through digital encryption.
In 2015, the International Association of Chiefs of Police (IACP) Computer Crime and Digital Evidence Committee (CCDE)created a resource pertaining to officer safety and mitigating the risks of doxing. This video provides guidance for law enforcement personnel who are attempting to protect their personal information.