The following guide was produced by the CNA Corporation under grant from the Department of Justice’s Bureau of Justice Assistance.
Managing Large-Scale Security Events: A Planning Primer for Local Law Enforcement Agencies
- 225 pages
- May 2013
- 11.8 MB
Large-scale events provide local governments with a number of valuable opportunities, including increasing revenue, revitalizing a city, and providing an increased sense of community. With these benefits comes greater responsibility for local law enforcement to ensure the public’s safety.
When law enforcement executives are tasked with managing a large event, they can maximize their efforts by learning from other agencies and adopting proven practices. Too often, however, past lessons learned are not documented in a clear and concise manner. To address this information gap, the U.S. Department of Justice’s Bureau of Justice Assistance worked in partnership with CNA to develop this Planning Primer.
This Planning Primer synthesizes salient best practices pertaining to security planning for a large-scale event, specifically pre-event planning, core event operations, and post-event activities. The Planning Primer includes detailed information on 18 core operational areas that law enforcement executives can give to lead law enforcement planners as supplemental guidance. This guidance can be used as a foundation for coordinating area-specific operational plans and can be modified to accommodate event security requirements and existing protocols. Furthermore, supplementing each operational area presented in the Planning Primer are actionable templates, checklists, and key considerations designed to facilitate the planning process (see Appendix A: Planning Toolkit).
…
Determine Authorities of Participating Agencies
Authority for event security planning and operations is often the responsibility of the local law enforcement agency that has operational control over the jurisdictional area; however, other agencies inside and outside of law enforcement will likely serve key functions critical to successful security operations. Neighboring law enforcement agencies (including those with events in their jurisdiction) and other mutual aid partners should be brought to the table early to engage in the planning process. If grant funds are used to support personnel costs, these funds are typically administered by the lead agency; there must be an open and transparent process for those funds to be distributed among mutual aid partners to cover personnel and security event expenses and to related events in neighboring jurisdictions. The local police department should serve as the lead liaison between local response partners and all other partners for the purpose of developing the components of, and implementing the event security plan. In this role, the local police department will identify key stakeholders (which may include agencies outside of law enforcement) that will have authority over security-related operations. Activities that are typically outside of the local police department’s purview tend to include: communications, fire/emergency medical services/public health response, transportation management, tactical/explosive support, consequence management, emergency management, and recovery. It will be the police department’s responsibility to coordinate the inputs of these stakeholders into the event security operations plan.
…
Anticipate Crowd Behaviors and Actions
Prior to the event, understand the nature of the audience attracted by a particular event. Work with event planners and interagency partners to gather intelligence on expected demonstration groups, including their size, typical behaviors, and any adversary groups. Information on demonstrators is primarily obtained through criminal intelligence gathering, which is detailed in Section 3.8 – Intelligence/Counterterrorism/Counter Surveillance.
Common demonstrator tactics that police should be aware of include the following:
• Blocking roads, streets, and intersections;
• Heaving barricades, rocks, and sticks;
• Wearing masks or other protective equipment to block effects from chemical irritants;
• Spitting or yelling in police officers’ faces; or
• Breaking windows or vandalizing property…
Determine Officer Dress
Officer dress can impact public perceptions and actions. For example, officers in full riot gear may encourage demonstrators to be more aggressive. Determine how crowd control officers should dress and any equipment needs (e.g., helmets, shields, chemical irritants).
Determine if a common uniform or an officer’s personal uniforms should be used. A common uniform can be valuable in providing a unified front for crowd control operations. Conversely, the local agency can allow visiting officers to wear their department’s uniform, which can be a cost-effective approach to showing a wide-range of force.
…
Control Demonstrator Activities
Consider the following strategies for controlling demonstrator activities during a large-scale security event:
• Pre-designate parade and march routes to better manage traffic interruptions of planned demonstrations.
• Prior to the event scan the area to remove objects that could be thrown at officers or used to damage property.
• Pre-position officers out of sight in hatch/riot gear.
• Designate space for demonstrators to sleep and set up their base of operations to consolidate demonstrators to one location and allow police to maintain better awareness of demonstrator activities.
• Evaluate the need for and layout of a free speech platform.…
Leverage Video Surveillance Technologies
Use video surveillance—in the form of wireless and wired cameras, high-definition backpack cameras, and cameras on cellular phones—to provide law enforcement with real-time information sharing and situational awareness. Such mechanisms improve commanders’ ability to make well-informed decisions in real time (e.g., by zooming in on suspicious objects or persons) and to deploy field forces appropriately.
After appropriate video technology is selected, make sure that all event personnel are trained on how to use it. In addition, tests and exercises should be conducted to validate that technologies are operational. Finally, establish back-up plans, such as replacement technologies or technicians on standby to fix broken equipment, in the case that technologies fail during the event.
Conduct Traditional and Non-Traditional Crime Analysis
Traditional crime analysis activities can bolster the effectiveness of video surveillance technologies, police departments can conduct commonly used analysis strategies to identify threats, such as monitoring calls for service, license plate readers, and intelligence databases/watch lists (e.g., National Crime Information Center, local police department command center, and NSSE watch lists). Use more novel crime-intelligence strategies—such as social media monitoring (e.g., Facebook, Twitter, and Open Stream) or cellular network technologies—to compile and disseminate useful security information.
Use Intelligence Sources with Mobile Technologies
Deploy intelligence sources and intelligence officers to gather real-time intelligence on the suspicious persons or activity, intent, tactics, and challenges related to demonstrator groups. Intelligence sources can use text messages and cellular phones to communicate intelligence to command staff for operational responses. Consider using mobile technologies that also allow intelligence sources to send photos and allow commanders to track their locations. Intelligence sources can also receive covert responses from its command post through text messages.
…
Conduct Arrests Quickly
Event-related arrest plans and procedures may have to be modified and amended in real-time. For example, during the 2012 DNC, CMPD learned that if it modified its arrest process to moving the arrest scene to another location, it could open roads and deescalate the original site. Future host departments should consider immediately transporting arrested individuals to an off-site location for processing to effectively diffuse potentially violent situations during arrests.
…
Learn Airspace Security Plans and Protocols
Become familiar with event airspace security plans that will outline airspace control measures, restrictions (including temporary flight restrictions), detection/monitoring, operations communications and coordination, and an integrated air defense plan that includes the use of military aviation support. During the event, identify who will handle dispatch of air missions and resource requests at the event’s designated interagency operations center, in the event of overlapping security operations.
…
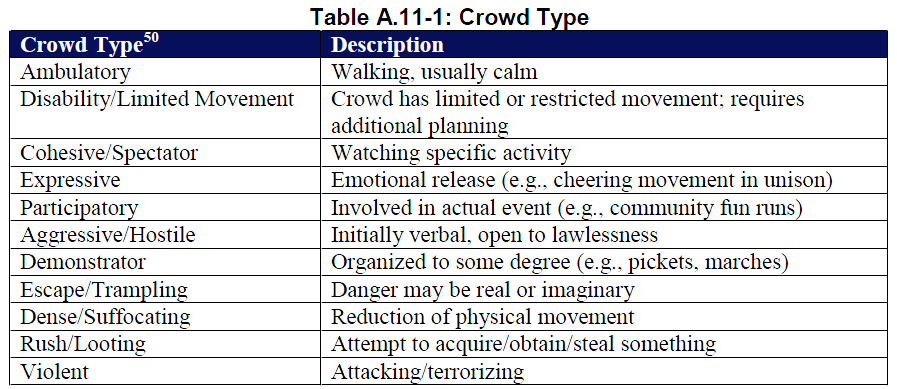
Considerations for Managing Crowds
In the planning process for a forthcoming event, organizers must have an understanding of both individual and crowd dynamics, as well as how these elements interrelate. While this is a preliminary guide to crowd control problems that organizers most frequently encounter, planners need to expand upon the particular issues for each crowd and venue. All of this information will assist in predicting potential problems that agencies can then address in the planning process.
General Issues for Consideration
1. Major crowd issues that the planning process should address include:
• Size – Maximum numbers permitted are often established by regulation for safety reasons.
• Demographics – Consider the composition of the audience, including the age and gender mix. If you identify in advance that young children will constitute a high proportion of the audience, consider additional facilities, such as childcare, family bathrooms, and rental strollers. Audiences made up of young children or elderly people tend to require additional medical facilities, and children and the elderly are more susceptible to crush injury than teens or adults.2. Different kinds of events may attract certain types of spectators that require special attention. Consider the following:
• Rock concerts, in contrast to other types of concerts, may experience a higher number of incidences with drug and alcohol abuse, underage drinking, and possession of weapons.
• Religious and “faith healing” events may attract a significant number of ill and infirm people, which may increase the need for on-site medical care.
• Events for senior citizens may also require higher levels of health services.
• Certain sports events may attract over-reactive and violent supporters.
• Cultural events may require special arrangements, including the provision of interpreter services; special food services; and multilingual signposting, brochures, and announcements.
• For outdoor concerts or events, consider:
− Control and distribution of spectators in the field;
− Suggested minimum space allocation of 4 to 5 square feet per person on grounds with no seats; and
− Some form of sectoring and barrier management by security.Crowd Issues
1. Crowds are complex social structures.
Crowd roles:
• Active Core: carry out action of crowd
• Cheerleaders: provide oral support for leaders
• Observers: follow actions but rarely take partSignificance of crowds:
• Increase the probability of a dangerous occurrence
• Increase the potential number of victims
• Make communication slower and more difficult
• Make changes in action slower and more difficult
• Diffuse responsibility (someone else will do it)2. Panics and Crazes
Panic in a group is the flight from a real or perceived threat from which escape appears to be the only effective response. What appears to be panic is usually the result of poor inputs (especially communications, or the lack of) and previous knowledge and experience.
Craze in a group is the temporary, short-lived competitive rush by a group toward some attractive object. A craze tends to occur on entering an event, and may be exacerbated by the lack of information.
3. De-individualization
De-individualization is a loss of self-awareness and evaluation apprehension in group situations that foster anonymity. Behavior may include:
• Mild lessening of restraint (e.g., screaming during a concert);
• Impulsive self-gratification (e.g., theft, vandalism, molestation); or
• Destructive social explosions (e.g., group violence, rioting and torturing).4. Defusing
The tedium that may be created by waiting and/or by the perception that other gates are being opened first, or later arrivals are being admitted first, can create problems. The following can help defuse the situation: appropriate music, the use of humor, food and beverage services moving through the group, cheerful security staff moving through the group, and good communication that includes a public address system.
…