(U//FOUO) DHS has no indication that adversaries or criminals are planning cyber operations against US election infrastructure that would change the outcome of the coming US election. Multiple checks and redundancies in US election infrastructure—including diversity of systems, non-Internet connected voting machines, pre-election testing, and processes for media, campaign, and election officials to check, audit, and validate results—make it likely that cyber manipulation of US election systems intended to change the outcome of a national election would be detected.
(U//FOUO) We judge cybercriminals and criminal hackers are likely to continue to target personally identifiable information (PII), such as that available in voter registration databases. We have no indication, however, that criminals are planning theft of voter information to disrupt or alter US computer-enabled election infrastructure.
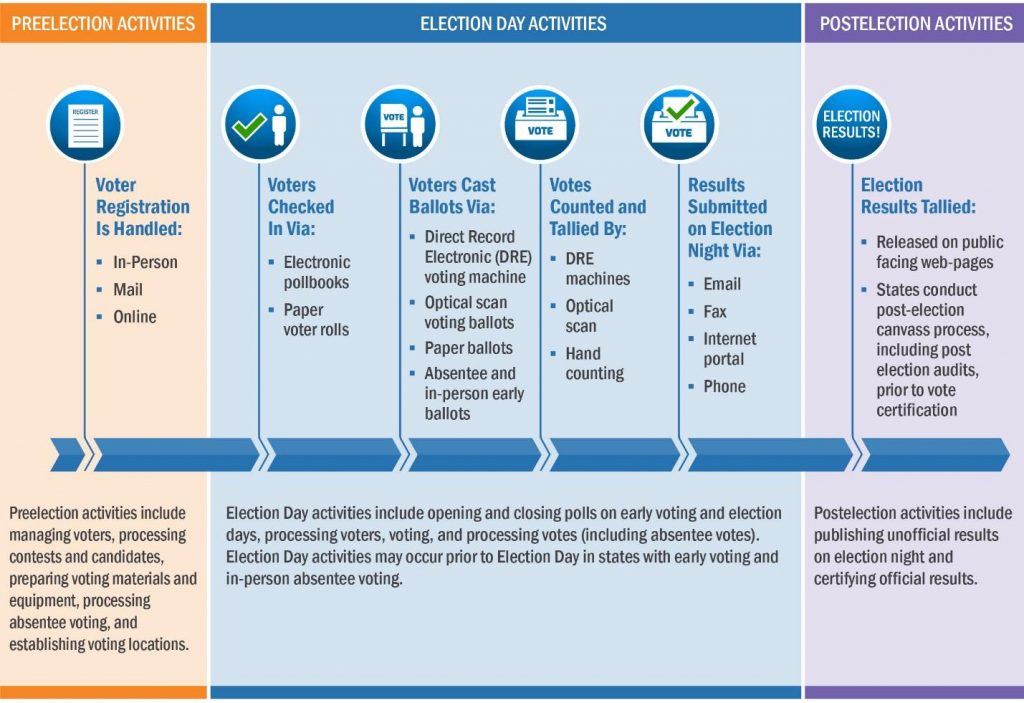
(U//FOUO) We assess multiple elements of US election infrastructure are potentially vulnerable to cyber intrusions. The risk to US computer-enabled election systems varies from county to county, between types of devices used, and among processes used by polling stations.
…
(U) US Computer-Enabled Election Infrastructure
(U) US election infrastructure is a diverse set of assets, systems, and networks, both public and private. Based on our analysis of each phase of the election process, the following election infrastructure represents the key computer-enabled assets, systems, and networks most critical to the security and resilience of the election process.
» (U) Electronic voting systems and associated infrastructure located at polling places during voting.
» (U) Information technology infrastructure and systems used to maintain voter registration databases.
» (U) Information technology infrastructure and systems used to manage elections, which may include systems that count, audit, and display election results on election night, as well as for post-election reporting used to certify and validate results.
(U//FOUO) No Indication of Cyber Operations to Change Vote Outcome
(U//FOUO) DHS has no indication that adversaries or criminals are planning cyber operations against US election infrastructure that would change the outcome of the coming US election. Multiple checks and redundancies in US election infrastructure—including diversity of systems, non-Internet connected voting machines, pre-election testing, and processes for media, campaigns and election officials to check, audit, and validate results—make it likely that cyber manipulation of US election systems intended to change the outcome of a national election would be detected.
» (U//FOUO) We assess that successfully mounting widespread cyber operations against US voting machines, enough to affect a national election, would require a multiyear effort with significant human and information technology resources available only to a nation-state. The level of effort and scale required to change the outcome of a national election, however, would make it nearly impossible to avoid detection. This assessment is based on the diversity of systems, the need for physical access to compromise voting machines, and the security and pre-election testing employed by state and local officials. In addition, the vast majority of localities engage in logic and accuracy testing, which work to ensure voting machines operate and tabulate as expected—before, during, and after the election.
» (U//FOUO) We judge, as a whole, voter registration databases are resilient to systemic, nationwide cyber manipulation because of the diverse systems and security measures surrounding them. Targeted intrusions against individual voter registration databases, however, are possible. Additionally, with illicit access, manipulation of voter data, or disruptions to their availability, may impact a voter’s ability to vote on Election Day. Most jurisdictions, however, still rely on paper voter rolls or electronic poll books that are not connected in real-time to voter registration databases, limiting the possible impacts in 2016.
» (U//FOUO) We assess the impact of an intrusion into vote tabulation systems would likely be contained to the manipulation of unofficial Election Night reporting results, which would not impact the certified outcome of an election, but could undermine public confidence in the results. In addition, local election officials, media organizations, and political campaigns carefully monitor local voting patterns, particularly in electorally significant jurisdictions, and are likely to detect and begin investigating potential anomalies quickly.