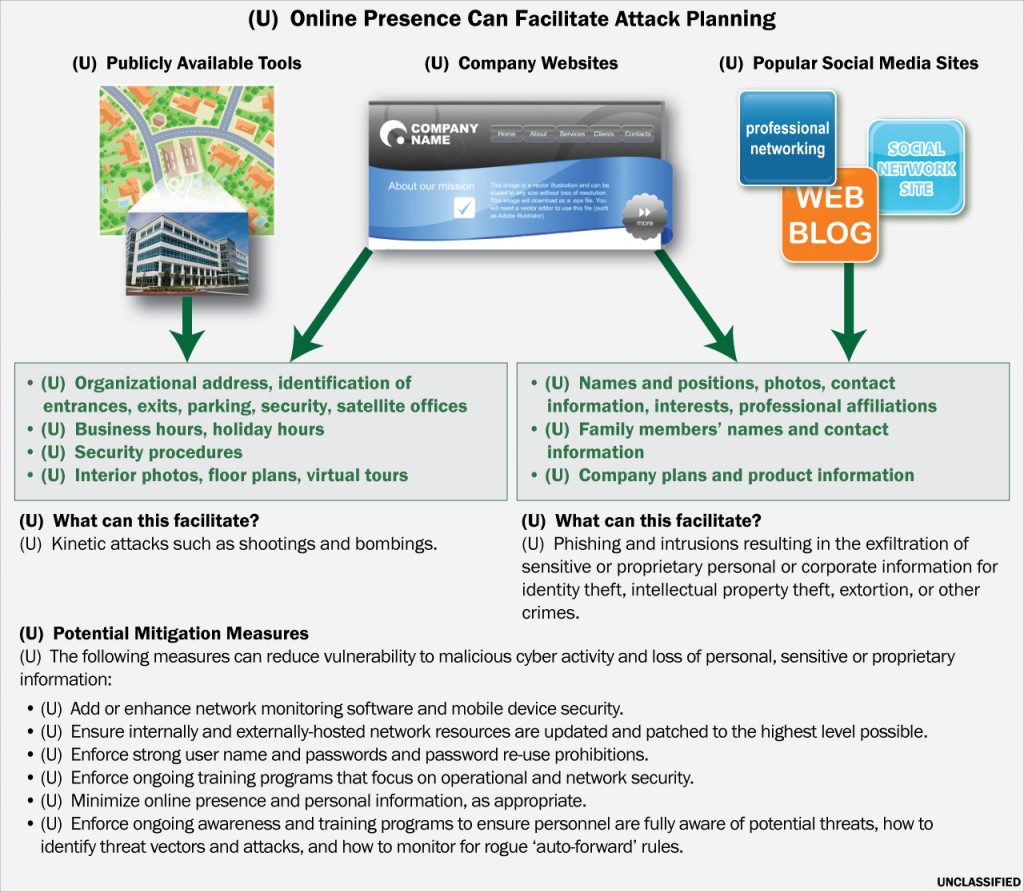
A graphic created by the Department of Homeland Security and Federal Bureau of Investigation detailing ways in which public tools available via the internet can be used to facilitate “attack planning.”
Public Intelligence
The Department of Homeland Security and FBI are warning law enforcement and security personnel around the country that online tools, search engines and corporate websites are a potential source of information for “malicious actors” seeking to plan terrorist attacks.
In a bulletin issued in late April, DHS and FBI state that malicious actors can “leverage the Internet to gain information against a potential target to support pre-operational planning efforts for kinetic or cyber attacks.” This includes using “Internet search engines for information such as maps, company photographs or blueprints, and gain additional details from social media sites and Web blogs.” A helpful infographic included in the bulletin describes how company websites and online maps can provide addresses, information on entrances, exits, parking, security and business hours. By combining information from a company’s website with social media, the bulletin suggests that businesses can be targeted for phishing attacks and computer network intrusions that could result in the “exfiltration of sensitive or proprietary personal or corporate information for identity theft, intellectual property theft, extortion, or other crimes.”
To mitigate vulnerabilities related to “internet attack planning,” DHS and FBI recommend minimizing “online presences” and protecting personal information, as well as conducting “ongoing training programs that focus on operational and network security.” A graphic accompanying the bulletin titled “Online Presence Can Facilitate Attack Planning” implies that public web presences via websites, blogs and social media increase an organization’s risk of being struck by violent criminal actions including “shootings and bombings” or cyber attacks.
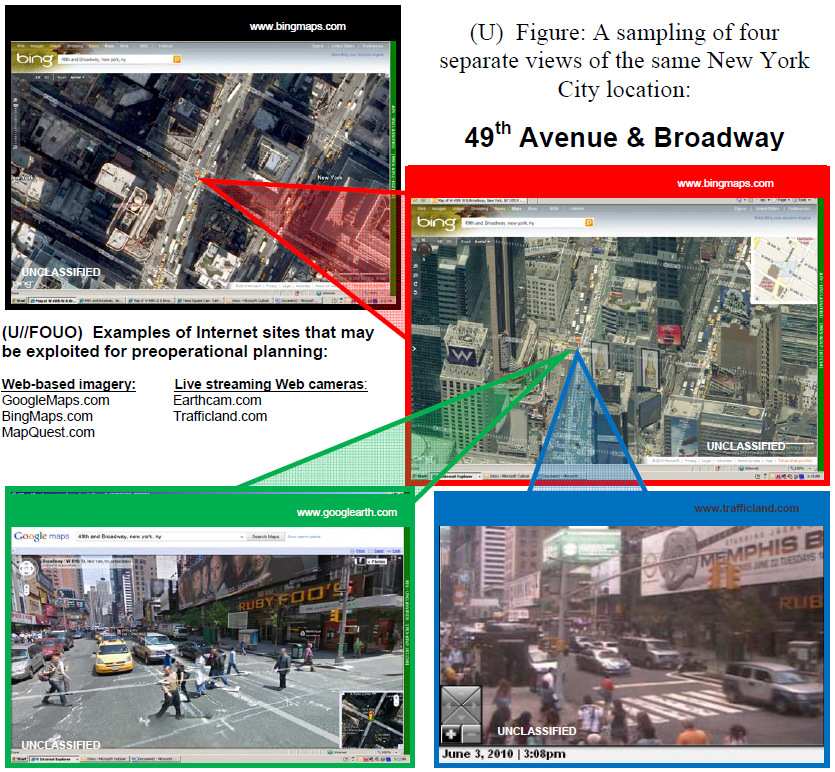
An image from a 2010 report from the Department of Homeland Security and National Counterterrorism Center showing how internet sites can be “exploited for preoperational planning.”
DHS expressed similar concerns in a 2010 report authored with the National Counterterrorism Center (NCTC) titled “Internet Sites Allow Detailed Surveillance and Pre-Attack Planning.” The report warns of “increasing sophistication” of commercially available internet tools that “may allow terrorists to study security measures in place and the relationship between the target and surrounding area using various viewing angles, to choose ingress and egress routes, and to monitor attack progress and results.” It claims that “video obtained through live Web-based camera feeds combined with street-level and direct overhead imagery views from Internet imagery sites allow terrorists to conduct remote surveillance of multiple potential targets without exposing themselves to detection.” To substantiate this position, the report cites the use of “a mapping capability operated by Google” by Iraqi insurgents as early as 2006 to plan rocket attacks on U.S. facilities. While online tools, in isolation, can only provide so much information, the report warns that “combining the use of multiple Internet tools can provide detailed, real-time information on potential attack locations” enabling potential terrorists to minimize their “physical presence during the target selection and surveillance phases” and limiting “law enforcement’s ability to detect and disrupt any plot.”
Last November, the NCTC released a document to law enforcement describing how urban explorers, “hobbyists who seek illicit access to transportation and industrial facilities in urban areas” including rooftops, utility tunnels and bridges, could unwittingly be “aiding terrorists” by providing detailed photos and videos of their exploration. This media “could be used by terrorists to remotely identify and surveil potential targets” which could “aid terrorists in pinpointing locations in dense urban environments.” One scenario described in the document involves urban explorers discovering and documenting the use of a bridge’s “ladders, crosswalk scaffoldings, trap doors, scuttles, and hatches” and reveal methods of accessing “structural components, including caissons (the structures that house the anchor points of a bridge suspension system), to identify weaknesses.”
