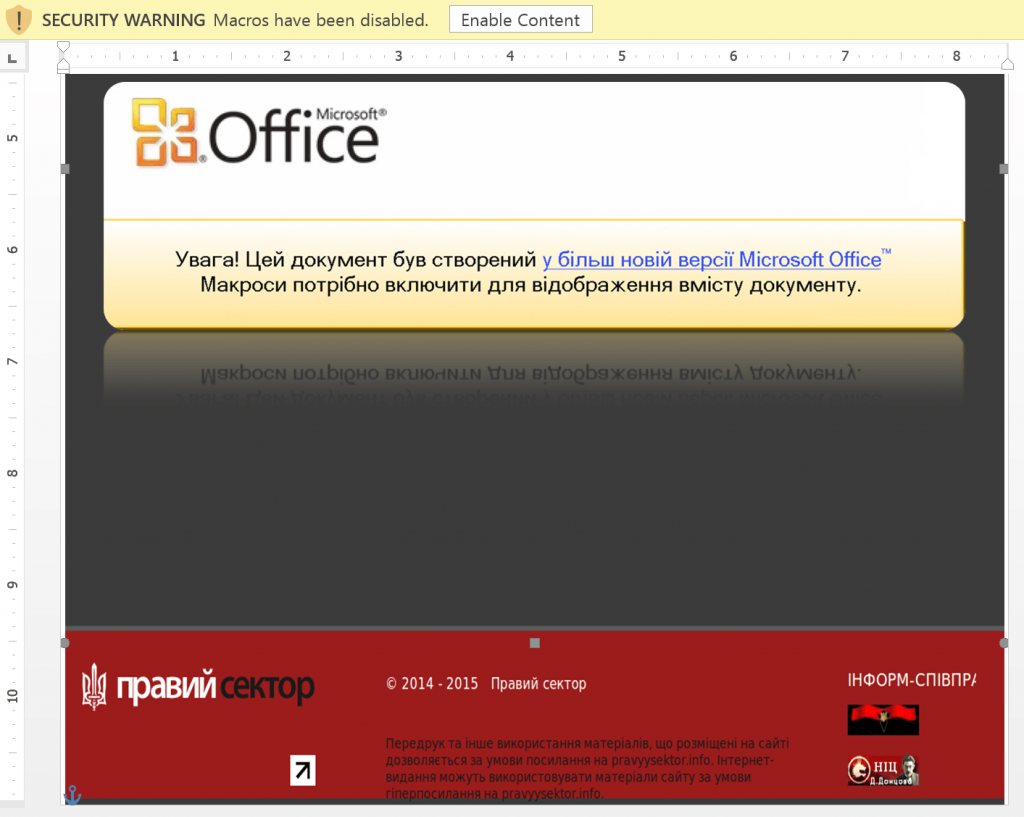
A screenshot released by the security company Kaspersky shows a malicious Microsoft Word document similar to one used by hackers in an December 2015 attack against the Ukrainian energy sector. The attack disrupted more than 200,000 customers and affected dozens of substations.
A Department of Homeland Security assessment released in April states that critical infrastructure throughout the U.S. faces “immeasurable vulnerabilities and attack vectors” due to the increasingly prominent role of information and communication technology (ICT) in critical infrastructure sectors. The strategic risk assessment, authored by the Office of Cyber and Infrastructure Analysis within DHS, was obtained by Public Intelligence and describes the “convergence of cyber and physical domains” as a strategic threat to the nation’s infrastructure.
As ICT is increasingly depended upon in “all 16 critical infrastructure sectors,” there is an “inherent reliance on a network connection for functionality” that “creates numerous vulnerabilities” and makes “universal security extremely difficult and improbable, allowing cyber attackers to more easily exploit critical infrastructure.” These vulnerabilities are also expected to affect the growth of smart cities and other developments related to the internet of things (IoT). DHS cites a report estimating the smart cities market to be valued at $392 billion by 2019 and estimates that in five years 26-50 billion IoT devices to exist. Warning that the growth of these technologies advantages comes with “inherent vulnerabilities,” DHS states that billions of “interconnected IoT devices creating, transmitting, and storing data will result in ‘data exhaust,’ which allows threat actors to gain significant insights into sensitive information such as telemetry, voice, video, health, and infrastructure component status data.” Moreover, failures of “critical infrastructure IoT devices” could result not just in “economic loss through lost productivity and damage to the national economy,” but also “adversely affect public safety through physical infrastructure damage or catastrophic infrastructure failure.”
Industrial control systems (ICS), such as supervisory control and data acquisition (SCADA) systems, that are connected to cloud infrastructure are also cited as a growing concern as “cloud providers are generally not prepared or equipped” to address many of the specialized security needs of these systems. The report states that the “compromise of critical infrastructure SCADA systems that are connected to cloud infrastructure could have a direct physical effect on human life.” However, the threat to ICS extends far beyond cloud security issues with more than 245 cyber-related incidents in FY2014 according to the Industrial Control Systems-Cyber Emergency Response Team (ICS-CERT). Techniques used in these incidents included “access and exploitation of Internet facing ICS and SCADA devices, exploitation of zero-day vulnerabilities in control system devices and software, malware infections within air-gapped control system networks, Structured Query Language injection and application vulnerability exploitation, network scanning and probing, lateral movement between network zones, targeted spear-phishing campaigns, and strategic Website compromises (a.k.a. watering hole attacks).”
Similar concerns were expressed in a January 2016 intelligence assessment issued by DHS which found that nation-state cyber actors are actively “targeting US energy sector enterprise networks” to maintain “persistent access to facilitate the introduction of malware” in the event of “hostilities with the United States.” While the assessment states that this activity is focused primarily on “data theft” as well as “accessing and maintaining presence on ICS” networks and systems, the report uses unusually blunt language to describe how this kind of access would likely be used as “part of nation-state contingency planning” only to be “implemented to conduct a damaging or disruptive attack in the event of hostilities with the United States.” In December 2015, a coordinated attack on the Ukrainian energy sector demonstrated just how damaging this sort of access to ICS infrastructure can be, resulting in the loss of power for more than 225,000 customers and the disruption of at least fifty regional substations. The attack is described in the DHS assessment as “consistent with our understanding of Moscow’s capability and intent, including observations of cyber operations during regional tensions.”
