Cyberspace operations (CO) is the employment of cyberspace capabilities where the primary purpose is to achieve objectives in or through cyberspace.
This publication focuses on military operations in and through cyberspace; explains the relationships and responsibilities of the Joint Staff (JS), combatant commands (CCMDs), United States Cyber Command (USCYBERCOM), the Service cyberspace component (SCC) commands, and combat support agencies; and establishes a framework for the employment of cyberspace forces and capabilities.
The Nature of Cyberspace Relationship with the Physical Domains.
Cyberspace, while part of the information environment, is dependent on the physical domains of air, land, maritime, and space.
CO use links and nodes located in the physical domains and perform logical functions to create effects first in cyberspace and then, as needed, in the physical domains. Actions in cyberspace, through carefully controlled cascading effects, can enable freedom of action for activities in the physical domains.
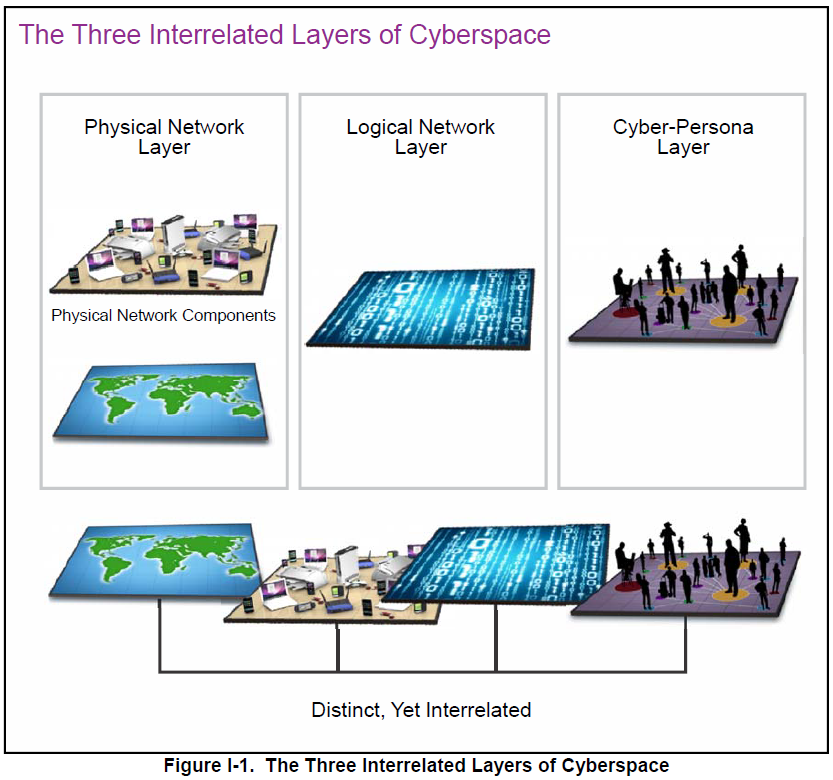
Cyberspace Layer Model. To assist in the planning and execution of CO, cyberspace can be described in terms of three interrelated layers: physical network, logical network, and cyberpersona. Department of Defense (DOD) Cyberspace. The Department of Defense information network (DODIN) is the set of information capabilities and associated processes for collecting, processing, storing, disseminating, and managing information on-demand to warfighters, policy makers, and support personnel, whether interconnected or stand-alone, including owned and leased communications and computing systems and services, software (including applications), data, security services, other associated services, and national security systems.
Connectivity and Access. Gaining access to operationally useful areas of cyberspace, including targets within them, is affected by legal, policy, or operational limitations. For all of these reasons, access is not guaranteed. Additionally, achieving a commander’s objectives can be significantly complicated by specific elements of cyberspace being used by enemies, adversaries, allies, neutral parties, and other United States Government (USG) departments and agencies, all at the same time.
The operational environment (OE) is a composite of the conditions, circumstances, and influences that affect the employment of capabilities and impact the decisions of the commander assigned responsibility for it. The information environment permeates the physical domains and therefore exists in any OE. The information environment is the aggregate of individuals, organizations, and systems that collect, process, disseminate, or act on information.
Given that cyberspace is wholly contained within the information environment and the chief purpose of information operations (IO) is to create effects in the information environment, there is significant interdependency between IO and CO.
Integrating Cyberspace Operations with Other Operations
During joint planning, cyberspace capabilities are integrated into the joint force commander’s (JFC’s) plans and synchronized with other operations across the range of military operations. While not the norm, some military objectives can be achieved by CO alone. Commanders conduct CO to obtain or retain freedom of maneuver in cyberspace, accomplish JFC objectives, deny freedom of action to the threat, and enable other operational activities.
Cyberspace Operations Forces
Commander, United States Cyber Command (CDRUSCYBERCOM), commands a preponderance of the cyberspace forces that are not retained by the Services. USCYBERCOM accomplishes its missions within three primary lines of operation: secure, operate, and defend the DODIN; defend the nation from attack in cyberspace; and provide cyberspace support as required to combatant commanders (CCDRs). The Services man, train, and equip cyberspace units and provide them to USCYBERCOM through the SCCs.
Challenges to the Joint Force’s Use of Cyberspace
Threats. Cyberspace presents the JFC’s operations with many threats, from nation-states to individual actors to accidents and natural hazards. Anonymity and Difficulties with Attribution. To initiate an appropriate defensive response, attribution of threats in cyberspace is crucial for any actions external to the defended cyberspace beyond authorized self-defense.
Geography Challenges. In cyberspace, there is no stateless maneuver space. Therefore, when US military forces maneuver in foreign cyberspace, mission and policy requirements may require they maneuver clandestinely without the knowledge of the state where the infrastructure is located.
Technology Challenges. Using a cyberspace capability that relies on exploitation of technical vulnerabilities in the target may reveal its functionality and compromise the capability’s effectiveness for future missions.
Private Industry and Public Infrastructure. Many of DOD’s critical functions and operations rely on contracted commercial assets, including Internet service providers (ISPs) and global supply chains, over which DOD and its forces have no direct authority.
Globalization. The combination of DOD’s global operations with its reliance on cyberspace and associated technologies means DOD often procures mission-essential information technology products and services from foreign vendors.
Mitigations. DOD partners with the defense industrial base (DIB) to increase the security of information about DOD programs residing on or transiting DIB unclassified networks.
…