The following document was included in a collection of records released January 30, 2015 by Pacific Gas & Electric in response to a ruling from the California Public Utilities Commission.
Northern California Regional Intelligence Center Advisory Bulletin
- 3 pages
- For Official Use Only
- March 27, 2014
(U//FOUO) The 16 April 2013 sabotage of optic cables and electricity transformers supplying Silicon Valley highlighted the vulnerability of critical infrastructure to deliberate, malicious harm. However, indications are lacking of a broader, sophisticated threat in the NCRIC area of responsibility for the following reasons.
The increase in suspicious activity reporting submitted to the NCRIC since the attack is consistent with heightened security awareness and does not signify a rise in nefarious activity.
• While the attack was preplanned, its execution was not sophisticated. Cutting the optic cables required the ability to lift manhole covers and use heavy wire cutters, and the radiators on the transformers presented a large, well-lit target that would be easy to hit.
• Characterizing the perpetrators as ‘snipers’ overstates the capability demonstrated in the attack. The multiple rounds fired from short range to disable each of the large transformers do not point to the shooter(s) possessing advanced marksmanship skills.(U//FOUO) Increased suspicious activity reporting levels consistent with heightened awareness. Following the Metcalf incident, the NCRIC received a significantly higher number of suspicious activity reports (SARs) relating to the electricity and telecommunications sectors, compared to previous months. Allowing for weekly fluctuations, SARs from these sectors have remained at consistently higher levels than before April 2013. No connections between individual SARs have emerged to indicate a specific trend of nefarious activity. Rather, the higher volume of reporting likely reflects heightened vigilance on the part of security personnel and law enforcement and greater sensitization to potential threats to these sectors.
(U//FOUO) Preplanned attack. Just before 1 a.m. on 16 April 2013, one or more individuals cut cables in separate underground vaults near the Metcalf electricity substation south of San Jose, CA. From there, they took up position outside the facility’s perimeter fence and opened fire on the substation’s transformers. They expended over 100 rounds of rifle ammunition, mostly striking the large radiators that cool the transformers. The punctured radiators leaked thousands of gallons of cooling oil, tripping alarms that prompted SCADA systems to prevent overheating and reroute power. The nearby Metcalf Energy Center called 911 to report hearing shots fired. As law enforcement responded, the intruders left the scene. Four strands of barbed wire were cut on a pasture fence near where it met the substation’s perimeter fence.
(U//FOUO) Whodunit? With the investigation of the Metcalf incident still ongoing, the motive for the sabotage and the affiliation or grievance of those who conducted it remains unknown. No one has claimed responsibility for the sabotage and nearly a year later, the motive is still unclear. The scale of the incident and the infrastructure targeted do not match the modus operandi of known threat actors. If the incident was indeed a terrorist attack, it is unusual that those responsible have not exploited media interest to advance their particular agenda. Criminals have targeted energy facilities for metal theft but typically do not go out of their way to take them offline. Environmental extremists and others with an antagonistic view of energy companies and large corporations have resorted to sabotage but rarely on so ambitious a scale. The significant damage caused at Metcalf would also be unusual for a disgruntled employee or frustrated customer. If the attackers’ intention was to terrorize, then it was a failed attack. They were apparently too risk averse to engage responding law enforcement or to cause greater damage to the substation’s components by entering the facility or to exploit the incident to further their social or political ideology.
(U) Electricity Infrastructure Threats and Vulnerabilities
(U//FOUO) Modes of Attack. From a capabilities perspective, various modes of attack could be used to disable critical infrastructure. The Department of Homeland Security assesses that targeted shootings, intentional downing of power lines, and bombings are “the most likely high-profile and potentially consequential” tactics for electricity subsector infrastructure. Depending on level of expertise and access to materials, potential adversaries could use small arms to damage components, as at Metcalf, or resort to improvised explosive devices, vehicle borne explosive devices, construction explosives (e.g., dynamite), grenades, destructive chemicals, introduction of hazardous materials, nuclear or radiological dispersion devices, arson, or sabotage of critical components of the electric infrastructure powering the site. In addition, cyber attacks present non-kinetic options for targeting critical infrastructure to disrupt the functionality of computerized control systems, infiltrate data processing, and cause severe economic and operational repercussions.
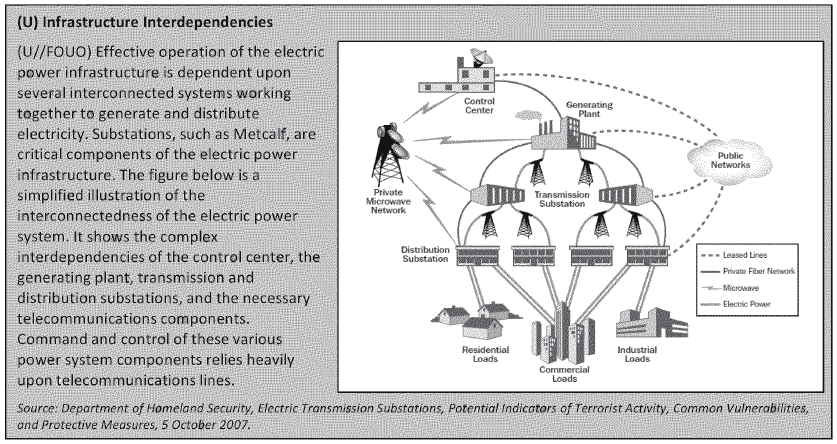
(U//FOUO) Vulnerabilities of Electricity Infrastructure. In recent media coverage of the sabotage at Metcalf, journalists have also noted the inherent vulnerability of electricity substations. As illustrated on the next page, the electric power system requires that all segments function efficiently; attacks upon any of the components can impact the entire system and have the potential for cascading damage effects. DEIS notes, however, that while targeted shootings can cause extensive damage, due to system resiliency, the effects may not result in significant impacts to customers. Because of their size and function, substations are often located in sparsely-populated areas along freeways or major thoroughfares. They are not easily concealed within buildings or behind fences. Critical components, such as the transformer cooling tanks targeted in the April 2013 attack, present an easy target. At the opposite extreme, SCADA systems that are used to control essential functions of many electrical substation components could in theory be disabled by a sophisticated cyber attack. The system also has some resilience, as demonstrated by the rerouting of service via other substations after the Metcalf substation’s transformers were taken offline. Although the sabotage at Metcalf was preceded by cutting optic cables in two nearby vaults, technicians at a remote location were still able to monitor alarms on the transformers as they overheated and shut them down without further damage.